Did you know that phones, including mobile devices, are not only essential for our daily lives but also susceptible to spoofed calls and anti spoofing attacks? Additionally, it’s important to be cautious of phishing emails. In fact, the threat of spoofed calls and anti spoofing in mobile phones is on the rise, posing a significant concern for users. Additionally, phishing emails are also becoming a growing issue. As technology continues to advance, so do the tactics used by malicious actors to gain unauthorized access to personal information and sensitive data. Device spoofing, phishing emails, and biometric spoofing are some of the methods they employ to bypass security systems.
In this blog post, we will explore different types of presentation attacks, such as biometric spoofing targeting facial recognition systems or fingerprint sensors. We will delve into the vulnerabilities of biometric identification and the potential risks associated with digital fingerprints and other biometric data. In this blog post, we will discuss the importance of robust identification methods, such as fingerprint recognition, to prevent anti spoofing attempts and safeguard user privacy. It is crucial to implement these methods to protect against fraudsters who may try to manipulate digital fingerprints. By understanding the concepts of anti spoofing and implementing effective measures against fraudsters, individuals and organizations can better protect themselves against potential security breaches. This includes utilizing fingerprint recognition technology to prevent presentation attacks.
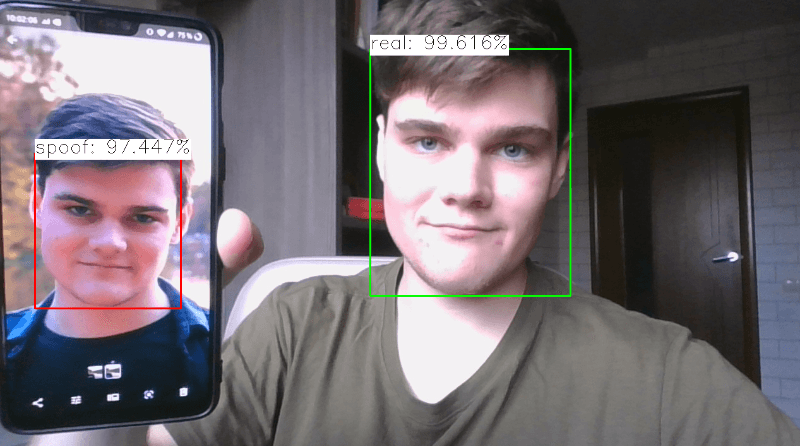
Understanding Anti-Spoofing
Spoofing is a deceptive tactic that involves falsifying information to trick or deceive someone. Anti spoofing techniques are used to prevent presentation attacks, such as face anti-spoofing and voice anti-spoofing. Anti spoofing techniques are used to prevent presentation attacks, such as face anti-spoofing and voice anti-spoofing. In the context of mobile devices, anti spoofing typically refers to manipulating caller ID or other identification methods to prevent phone number spoofing. This presentation will focus on the importance of implementing anti spoofing measures to enhance voice security. This can be done through various means, such as using device spoofing or IP spoofing to manipulate the caller ID and make it appear as if the call is coming from a trusted source. Spoofing can have malicious intentions, including scams, phishing attempts, or even identity theft. Anti spoofing measures can help prevent these fraudulent activities by verifying the authenticity of the caller’s voice or face.
Mobile Device Vulnerabilities
Mobile devices are particularly vulnerable to anti spoofing due to their reliance on wireless networks and communication protocols for voice identification. These vulnerabilities, such as device spoofing and biometric spoofing, can be exploited by attackers to manipulate or deceive users for their own gain. Implementing anti spoofing measures is crucial to protect the system. Weaknesses in operating systems and applications can provide opportunities for device spoofing, IP spoofing, and biometric spoofing to carry out their fraudulent activities. Anti spoofing measures should be implemented to prevent these attacks.
Understanding these vulnerabilities is crucial for implementing an effective anti spoofing system with face liveness detection measures. By implementing anti spoofing measures and incorporating liveness detection into the system, device manufacturers and software developers can bolster the security of mobile devices. This ensures users are safeguarded against a range of spoofing attacks that exploit vulnerabilities in the system.
Importance of Security
Ensuring security in mobile devices is paramount in safeguarding personal information and preventing unauthorized access. This includes protecting against biometric spoofing, IP spoofing, and other forms of system breaches. Anti-spoofing measures are essential for maintaining the integrity and trustworthiness of mobile communications, especially when it comes to the security of biometric systems. These measures ensure that the number of fraudulent attempts is minimized and that the liveness detection technology can accurately verify the authenticity of biometric data. By implementing robust security protocols, mobile device users can have peace of mind knowing that their calls, messages, and personal data are protected from malicious actors attempting ip spoofing, biometric spoofing, or any other system breach.
Anti-spoofing measures include technologies like digital signatures, encryption algorithms, biometric authentication mechanisms, and liveness verification that confirm the authenticity of incoming calls or messages. These measures help users differentiate between legitimate communications and potentially harmful device spoofing or IP spoofing attempts. Additionally, they enhance security by implementing biometric authentication and liveness detection.
Moreover, biometric anti-spoofing solutions also rely on continuous monitoring for suspicious activities or patterns that may indicate an ongoing liveness spoofing attack. By detecting anomalies in real-time, these solutions can take immediate action to mitigate any potential threats such as device spoofing, biometric manipulation, liveness fraud, and IP spoofing before they cause harm.
Recognizing Phone Number Spoofing
Caller ID deception, also known as spoofing, is a common form of biometric and liveness manipulation where attackers manipulate the displayed phone number or name. By using device spoofing and IP spoofing, they can appear as someone else or a trusted entity, compromising liveness and biometric security. This technique of device spoofing and IP spoofing is often used by scammers to trick individuals into answering their calls or providing sensitive information. Biometric and liveness measures can help prevent such scams.
Being able to recognize caller ID deception is crucial for identifying potential spoofing attempts and ensuring liveness. There are several signs that can indicate an IP spoofing or liveness call. For instance, unexpected calls from familiar numbers or unknown entities should raise suspicion, especially if there are signs of IP spoofing or lack of liveness. If you receive a call from a number that you know well, but it seems out of character for them to be calling at that particular moment, it could be a sign of liveness spoofing.
Another indicator of possible spoofing is poor call quality or unusual background noise during the conversation, which can indicate a lack of liveness. If you notice static, echoes, or other disturbances on the line that are not typical for your phone service, it may be an indication of liveness manipulation.
It’s important to remain vigilant and aware of the signs of liveness when receiving calls from unfamiliar numbers or unexpected sources. Scammers often rely on people’s trust and liveness in order to deceive them successfully. By staying alert and recognizing the signs of spoofing, you can avoid falling victim to these fraudulent activities that lack liveness.
In some cases, individuals may receive calls claiming to be from well-known organizations such as banks or government agencies. These calls often require the person to prove their liveness. These callers may use sophisticated techniques to ensure liveness by displaying official-looking phone numbers on the caller ID screen. However, it’s essential to remember that reputable organizations typically do not request personal information over the phone without prior arrangement. This is because they prioritize liveness and ensure that personal information is not compromised.
If you suspect a call may be spoofed or fraudulent, it’s best not to provide any personal information or engage with the caller further to ensure liveness. Instead, hang up and independently verify the liveness and legitimacy of the call by contacting the organization directly using official contact information obtained through reliable sources such as their official website.
Preventing Phone Spoofing
Phone spoofing, a common tactic used by attackers to deceive and manipulate individuals, has become a prevalent issue in the age of liveness. To protect mobile devices from falling victim to these spoofing attacks and ensure liveness, there are several preventive measures that can be implemented.
Verification Methods
Implementing liveness verification methods on mobile devices adds an extra layer of security, making it harder for attackers to spoof user credentials. One effective method is two-factor authentication (2FA). With 2FA, users are required to provide two forms of identification, including liveness, before accessing their device or sensitive information. This could involve entering a password and then receiving a unique code via SMS or email to ensure liveness.
Biometric authentication, including liveness detection, is another powerful tool in the fight against phone spoofing. By utilizing fingerprint or face recognition technology, mobile devices can verify the user’s identity based on unique physical characteristics, ensuring liveness. This method is not only convenient but also highly secure since it utilizes liveness to ensure that biometric data is difficult to replicate.
By implementing these verification methods, users can significantly reduce the risk of falling victim to phone spoofing attacks. Attackers will find it much more challenging to bypass these additional layers of security.
Call Blocking Apps
Call blocking apps have emerged as a valuable defense against phone spoofing. These apps utilize databases of reported spoofed numbers, allowing users to filter out and block potential threats. By using call blocking apps, individuals can proactively protect themselves from known scam numbers and avoid engaging with fraudulent calls.
One advantage of call blocking apps is their ability to continuously update their databases with newly reported numbers. This ensures that users stay protected against the latest phone spoofing tactics employed by scammers. Some call blocking apps offer features such as community reporting and spam detection algorithms, further enhancing their effectiveness in identifying and blocking suspicious calls.
By leveraging call blocking apps, individuals can take control over their incoming calls and minimize the risk of falling for phone spoofing scams. These apps provide an additional line of defense against malicious actors attempting to deceive and defraud unsuspecting users.
Incorporating verification methods and utilizing call blocking apps are essential steps in preventing phone spoofing attacks. These measures empower individuals to protect themselves from potential threats and maintain the security of their mobile devices. By implementing these strategies, users can safeguard their personal information, avoid falling for phishing emails or calls, and ensure a safer digital experience.
Recognizing IP Spoofing
IP spoofing is a technique used by malicious individuals to manipulate their IP addresses, concealing their true location or identity. This makes it difficult to trace the origin of spoofed calls or messages, posing a significant challenge for security professionals and law enforcement agencies.
Understanding the various tactics employed in IP deception is crucial for developing effective anti-spoofing strategies. By recognizing these tactics, organizations can better protect themselves against potential threats and mitigate the risks associated with spoofed communications.
IP Deception Tactics
Spoofers employ several tactics to deceive others through their IP addresses. One common tactic is source IP address forgery, where the spoofer manipulates the source address in packets to make it appear as if they are originating from a different location or device. This can be achieved by using readily available tools and techniques, making it relatively easy for attackers to carry out such attacks.
Another tactic is known as destination IP address spoofing. In this case, the attacker manipulates the destination address in packets to redirect traffic to an unintended recipient or network. By doing so, they can intercept sensitive information or launch further attacks on unsuspecting victims.
IP deception also involves techniques like session hijacking and TCP/IP sequence number prediction. These methods allow attackers to gain unauthorized access to ongoing sessions and manipulate data exchanges between parties involved. By exploiting vulnerabilities within network protocols, attackers can inject malicious code or compromise sensitive data.
Network Vulnerabilities
Mobile networks are particularly vulnerable to various types of attacks due to their inherent nature and architecture. One common vulnerability is man-in-the-middle (MITM) attacks, where an attacker intercepts communication between two parties without their knowledge. This allows them to eavesdrop on conversations, modify messages, or even impersonate one of the legitimate parties involved.
Network hijacking is another prevalent vulnerability that spoofers exploit. By gaining control over mobile networks’ infrastructure elements such as base stations or routers, attackers can redirect traffic to their own malicious servers. This enables them to intercept and manipulate communications, potentially leading to unauthorized access or data breaches.
To mitigate these risks, it is essential to implement secure network protocols. By using encryption technologies such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), organizations can ensure that data transmitted over mobile networks remains confidential and protected from interception or manipulation.
Implementing robust authentication mechanisms and intrusion detection systems can help identify and prevent potential spoofing attacks.
Safeguarding Against IP Spoofing
There are several measures that can be taken. Two key strategies involve implementing secure network protocols and encryption techniques.
Secure Network Protocols
Secure network protocols like HTTPS (Hypertext Transfer Protocol Secure) and VPNs (Virtual Private Networks) play a crucial role in safeguarding against IP spoofing. These protocols encrypt data transmitted over mobile networks, ensuring that communication remains confidential and protected from spoofing attempts.
By encrypting the data, secure network protocols make it extremely difficult for malicious actors to intercept or manipulate the information being transmitted. This adds an extra layer of security to mobile devices, making it harder for attackers to impersonate legitimate IP addresses or alter the source address.
For example, when you visit a website using HTTPS, your browser establishes a secure connection with the server through encryption. This prevents attackers from eavesdropping on your communication or tampering with the data being exchanged.
Similarly, when using a VPN on your mobile device, all your internet traffic is encrypted and routed through a remote server before reaching its destination. This not only protects your data but also masks your actual IP address, making it challenging for attackers to spoof your identity.
Encryption Techniques
Encryption techniques are another essential aspect of protecting against IP spoofing in mobile devices. Encryption involves scrambling data so that it can only be accessed by authorized parties who possess the decryption key.
Implementing robust encryption techniques is crucial for preventing spoofing attacks because they ensure that sensitive information remains secure during transmission. Even if an attacker manages to intercept the data packets being sent over a network, they will be unable to decipher the encrypted content without the decryption key.
Strong encryption algorithms such as AES (Advanced Encryption Standard) are widely used to protect sensitive information on mobile devices. These algorithms provide high levels of security by transforming plain text into ciphertext using complex mathematical operations.
Biometric Anti-Spoofing Technologies
Biometric anti-spoofing technologies play a crucial role in enhancing the security of mobile devices. They provide an additional layer of protection against spoofing attacks, ensuring that only authorized users can access sensitive information. Let’s explore some of the key biometric anti-spoofing technologies used in mobile devices.
Fingerprint Security
Fingerprint security is one of the most widely adopted biometric authentication methods in mobile devices. It utilizes the unique patterns on a user’s finger to authenticate their identity. By scanning and analyzing these patterns, mobile devices can verify whether the fingerprint belongs to an authorized user or not.
The advantage of fingerprint security lies in its high level of accuracy and reliability. Spoofing attempts, such as using artificial fingerprints or copies, are difficult to replicate accurately enough to deceive fingerprint scanners. This makes fingerprint security an effective measure against biometric spoofing.
Incorporating fingerprint security into mobile devices significantly enhances their anti-spoofing measures. Users can conveniently unlock their devices and authorize transactions with just a touch of their finger, knowing that their identity is protected by this robust biometric system.
Voice Recognition
Voice recognition technology is another powerful tool for combating spoofing attacks on mobile devices. It analyzes the unique characteristics of a person’s voice, such as pitch, tone, and pronunciation, to verify their identity. By comparing these characteristics with stored voice data, mobile devices can determine if the speaker is genuine or attempting to deceive the system.
Implementing voice recognition as an additional layer of security enhances the overall anti-spoofing capabilities of mobile devices. Even if someone manages to mimic another person’s voice or use pre-recorded audio clips, sophisticated algorithms can detect anomalies and identify potential fraud attempts.
With voice recognition technology integrated into mobile devices, users can enjoy secure interactions through voice commands and authentication processes without worrying about unauthorized access or fraudulent activities.
Face Authentication
Face authentication is another biometric anti-spoofing technology that has gained significant popularity in recent years. It uses facial features, such as the arrangement of eyes, nose, and mouth, to authenticate a user’s identity. By capturing and analyzing these features, mobile devices can accurately verify whether the face belongs to an authorized user or not.
One of the key advantages of face authentication is its difficulty to spoof.
Liveness Detection in Biometrics
Liveness detection is a crucial aspect of biometric authentication that helps ensure the security and reliability of mobile devices. By incorporating advanced technologies like motion analysis and texture detection, mobile devices can effectively detect and prevent spoofing attempts, adding an extra layer of protection to user data.
Motion Analysis
Motion analysis technology plays a vital role in liveness detection. It detects and analyzes the unique movement patterns of a user, such as the way they hold their device or interact with it. By studying these patterns, mobile devices can distinguish between genuine users and spoofing attempts.
For example, when a user interacts with their device, they create distinct motion patterns that are difficult for attackers to replicate accurately. By analyzing these patterns in real-time, mobile devices can verify the authenticity of a user’s actions.
Implementing motion analysis enhances the anti-spoofing capabilities of mobile devices by ensuring that only legitimate users have access to sensitive information. This technology adds an additional layer of security against various types of attacks, including replay attacks or using static images or videos for authentication purposes.
Texture Detection
Texture detection is another powerful technology used in liveness detection to combat spoofing attempts. It analyzes the unique texture patterns on a user’s fingers or hands for authentication purposes.
Every individual has distinctive texture patterns on their skin that are virtually impossible for an attacker to replicate accurately. By leveraging this uniqueness, mobile devices can verify the presence of live human tissue during biometric authentication processes.
Incorporating texture detection into mobile devices significantly strengthens anti-spoofing measures. It ensures that only genuine users with live skin are granted access to sensitive data or functionalities. This added layer of security makes it extremely challenging for attackers to bypass biometric authentication systems through methods like using high-resolution photographs or artificial replicas.
Types of Biometric Identification
Biometric identification has become an essential part of mobile device security, providing robust protection against spoofing attacks.
Retinal Scans
Retinal scans utilize the unique patterns found in a person’s retina to authenticate their identity. This highly secure method is difficult to spoof, as each individual’s retina pattern is distinct and cannot be easily replicated. By capturing detailed images of the blood vessels in the back of the eye, retinal scans provide a reliable and accurate means of biometric authentication.
Implementing retinal scans in mobile devices significantly enhances their anti-spoofing capabilities. With this technology, users can be confident that their personal information remains protected even if someone attempts to deceive the system using fake or stolen credentials. The complexity involved in replicating a person’s retina pattern makes it extremely challenging for fraudsters to bypass this level of security.
Voice Patterns
Voice pattern analysis is another effective method used for biometric identification. It identifies and verifies individuals based on their unique vocal characteristics such as pitch, tone, rhythm, and pronunciation. Just like fingerprints or iris patterns, each person has a distinctive voice print that sets them apart from others.
Incorporating voice pattern analysis into mobile devices adds an extra layer of security against voice spoofing attempts. By analyzing various aspects of an individual’s speech patterns, including intonation and cadence, these systems can differentiate between genuine voices and artificially generated ones. This technology ensures that only authorized users are granted access to sensitive information or functionalities on their mobile devices.
Facial Recognition
Facial recognition technology has gained significant popularity in recent years due to its ability to analyze facial features for biometric authentication purposes. By capturing key points on a person’s face – such as the distance between their eyes, the shape of their nose and mouth, and the contours of their face – facial recognition algorithms create a unique template that can be used to verify identity.
Implementing facial recognition in mobile devices enhances their anti-spoofing capabilities by providing strong security against spoofing attempts. This technology is particularly effective in detecting fraudulent activities involving masks or other physical disguises. By comparing real-time images with stored templates, facial recognition systems ensure that only authorized individuals can unlock and access sensitive data on their mobile devices.
Guarding Against Fraudulent Calls
Spoofing, the act of falsifying caller ID information to deceive recipients, has become a prevalent issue in mobile devices. To combat this fraudulent practice and protect users from falling victim to scams, it is crucial to implement effective security measures.
Awareness Training
One of the most effective ways to combat spoofing is by providing awareness training to mobile device users. By educating individuals about common spoofing techniques and how to recognize and respond to them, we empower them to make informed decisions when receiving calls.
Through awareness training, users can learn about various types of spoofing attempts, such as neighbor spoofing (where fraudsters mimic the recipient’s area code) or government agency impersonation (where scammers pose as representatives from official organizations). Armed with this knowledge, individuals can be cautious when receiving incoming calls that appear suspicious or too good to be true.
Moreover, awareness training plays a vital role in enhancing overall mobile device security. By educating users about the risks associated with answering unknown calls or sharing personal information over the phone, we create a more vigilant user base that actively contributes to safeguarding their own devices and personal data.
Reporting Mechanisms
Implementing reporting mechanisms is another essential step in the fight against spoofing. These mechanisms allow users who suspect they have received a spoofed call to report it directly through designated channels. By doing so, authorities can gather valuable information on suspected incidents and take appropriate action against fraudsters.
Effective reporting mechanisms not only enable users to play an active role in combating spoofing but also aid law enforcement agencies in tracking and investigating these activities. The data collected through reports can help identify patterns and trends related to specific spoofer tactics or target demographics. This information strengthens enforcement efforts by allowing authorities to focus their resources on areas where fraudulent activities are most prevalent.
Furthermore, reporting mechanisms contribute to creating a safer environment for mobile device users. When individuals know that their reports are taken seriously and followed up on, they are more likely to come forward with information about suspected spoofing incidents. This collective effort helps build a robust network of users who actively participate in the fight against fraudulent calls.
Network Security Measures
Intrusion Detection Systems:
Intrusion detection systems (IDS) are an essential component of network security measures to combat spoofing in mobile devices. These systems continuously monitor network traffic, analyzing it for any suspicious activities or patterns that could indicate a spoofing attempt. By detecting and alerting users in real-time, IDS can significantly enhance the anti-spoofing capabilities of mobile devices.
Implementing intrusion detection systems provides an additional layer of protection against spoofing attacks. These systems use various techniques such as signature-based detection and anomaly detection to identify potential threats. Signature-based detection compares network traffic against a database of known attack signatures, while anomaly detection looks for deviations from normal network behavior.
Regular Audits:
Conducting regular audits of mobile devices and networks is crucial in maintaining strong anti-spoofing defenses. These audits help identify vulnerabilities that could be exploited by spoofers and ensure that security measures are up-to-date and effective.
During audits, security professionals thoroughly inspect the configuration settings, software versions, and security protocols on mobile devices. They also assess the effectiveness of countermeasures such as packet filtering to prevent unauthorized access to networks.
By regularly auditing mobile devices and networks, organizations can proactively address any weaknesses or gaps in their anti-spoofing strategies before they are exploited by malicious actors. This proactive approach helps minimize the risk of successful spoofing attacks and strengthens overall network security.
Audits play a vital role in compliance with industry regulations and standards related to data privacy and security. Organizations need to demonstrate that they have implemented adequate safeguards against spoofing attempts through regular audits to maintain regulatory compliance.
Conclusion
Congratulations! You are now equipped with the knowledge to combat spoofing on your mobile devices. By understanding the various types of spoofing, such as phone number spoofing and IP spoofing, you can recognize and prevent these fraudulent activities. Implementing biometric anti-spoofing technologies, such as liveness detection, can add an extra layer of security to your device. Taking network security measures and being vigilant against fraudulent calls will further safeguard your personal information.
Now it’s time to put this knowledge into action. Take a proactive approach in protecting yourself and your devices from spoofing attacks. Stay updated on the latest security measures and technologies, and share this information with your friends and family to help them stay safe too. Remember, prevention is key. Keep your guard up, stay informed, and enjoy a secure mobile experience.
Frequently Asked Questions
What is anti-spoofing in mobile devices?
Anti-spoofing in mobile devices refers to the measures taken to prevent fraudulent activities such as phone number spoofing and IP spoofing. It involves implementing security mechanisms to ensure that the identity of a device or user is not maliciously impersonated.
How does phone number spoofing work?
Phone number spoofing involves manipulating caller ID information to display a different phone number than the actual one used for making a call. This deceptive technique allows scammers to mask their true identity and trick recipients into answering or trusting the call.
How can I prevent phone number spoofing?
To prevent phone number spoofing, be cautious when receiving calls from unfamiliar numbers. Avoid sharing personal information over the phone unless you are certain about the caller’s authenticity. Consider using call-blocking apps or services that identify potential spam or fraudulent calls.
What is IP spoofing?
IP spoofing is a technique where an attacker alters the source IP address of packets sent over a network, making it appear as if they originated from a different source. This deceptive practice can be used for various malicious purposes, including bypassing network security measures.
How can I safeguard against IP spoofing?
To safeguard against IP spoofing, ensure that your network infrastructure has robust security protocols in place, such as firewalls and intrusion detection systems. Regularly update software and firmware to patch any vulnerabilities that could be exploited by attackers attempting IP spoofing attacks.
Add a Comment