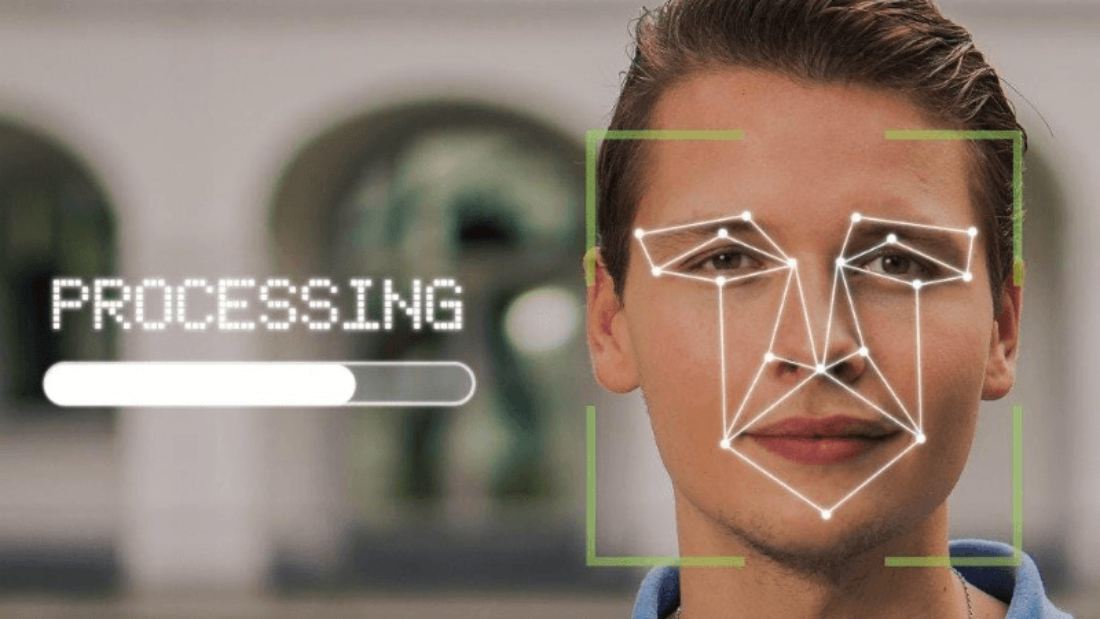
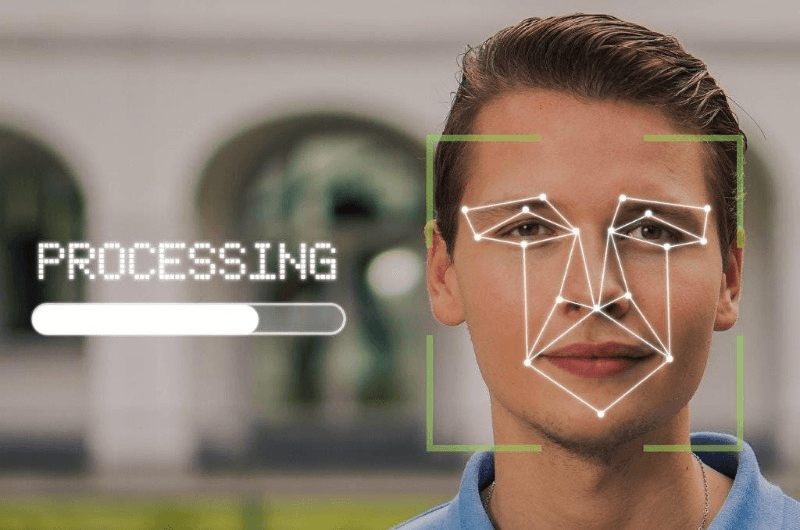
Biometric technology is revolutionizing the healthcare industry, specifically the biometrics market, by becoming an integral part of patient care. These technologies are transforming medical things and enabling personalized medicine. The future of healthcare lies in the seamless integration of biometrics and technologies, offering a secure and efficient way to enhance patient care with predictive analytics and personalized medicine. Medical things play a crucial role in this advancement.
From ongoing developments in biometric technologies to real-world applications, we will delve into how predictive analytics are transforming the way healthcare providers operate, ultimately enhancing the patient experience. For example, biometrics technology can be used for patient registration, attendance tracking, voice recognition for secure access to health information, and even clinical trial participant identification. The biometrics market offers a range of technologies that enable these applications.
By leveraging biometric technologies, healthcare providers can improve accuracy and efficiency in various processes by using analytics and machine learning. This not only reduces risks associated with identity theft and medical fraud but also paves the way for personalized medicine. Join us as we uncover the potential of biometrics in creating a safer and more streamlined healthcare environment, leveraging technologies like analytics and data science applications to analyze blood and improve patient care.
Understanding the Basics of Biometric Technology

Biometric technologies are revolutionizing organisations in the healthcare industry, offering a secure and efficient way to verify patient identities. By utilizing unique physiological or behavioral characteristics, such as fingerprints or facial recognition, biometrics provide a reliable method for identity verification in various technologies, health information, and health systems used by organisations. This section will delve into the factors driving the use of biometric technologies in healthcare organizations and explore the anticipated growth in its applications.
Factors Driving Biometric Technology Use
One of the key drivers behind the adoption of biometric technologies in healthcare organizations is the increasing concern about data breaches. With cyber threats becoming more sophisticated, traditional methods of identification, such as passwords or ID cards, are no longer sufficient to protect sensitive patient information. This is where biometrics technology and its various technologies come into play. Biometric data analysis and the expertise of biometric research professionals are crucial in safeguarding patient information. Biometrics technologies offer an extra layer of security in the health system by relying on unique biological traits that are difficult to replicate.
Moreover, accurate patient identification using biometrics technology is crucial for delivering high-quality healthcare services. This involves the use of biometric data analysis by biometric research professionals to ensure accurate identification and enhance patient care. These technologies play a vital role in improving healthcare outcomes. Misidentification in the health system can lead to medical errors, delayed treatments, and compromised patient safety. Biometric data analysis by biometric research professionals can help prevent such issues by utilizing advanced technologies. Biometric technologies provide a reliable way to ensure accurate identification throughout various touchpoints within the healthcare system. These biometric solutions incorporate advanced technologies to enhance security and streamline processes. Biometric data analysis technologies eliminate manual errors associated with traditional identification methods and streamline administrative processes for biometric research professionals in the health system.
Furthermore, biometric technologies offer a convenient and user-friendly solution for identity verification in the health system. Patients no longer need to remember multiple passwords or carry physical IDs with them thanks to advancements in biometric research and biometric data analysis. With just a fingerprint scan or facial recognition, individuals can quickly and securely access their medical records or authorize medical procedures, thanks to advancements in biometric research.
Anticipating Growth in Biometric Applications
The use of biometrics in healthcare is expected to grow exponentially in the coming years due to advancements in technology and its proven benefits. As technology continues to evolve, innovative applications of biometrics are being explored across various aspects of healthcare delivery.
For instance, biometric data analysis holds immense potential for early disease detection and personalized treatment plans. By analyzing patterns within large datasets derived from biometric measurements like heart rate variability or gait analysis, healthcare professionals can identify subtle changes indicative of underlying health conditions before symptoms manifest. This proactive approach, supported by biometric research, can significantly improve patient outcomes and reduce healthcare costs.
The integration of biometric solutions into healthcare systems will become increasingly prevalent worldwide. From hospitals to clinics, biometrics will be used for patient identification, access control, medication administration, and even remote monitoring. These biometric research applications not only enhance security but also streamline workflows, leading to improved efficiency and better patient experiences.
The Role of Biometrics Beyond Security in Healthcare
Enhancing Patient Safety and Care
Biometric technology has a significant role to play beyond security in the healthcare industry. One of the key areas where biometrics can make a difference is in enhancing patient safety and care. By accurately identifying patients using biometric data, medical errors can be significantly reduced. This is especially crucial.
In addition to accurate identification, biometrics also enable secure access control within healthcare facilities. With the use of biometric authentication such as fingerprint or iris scanning, only authorized personnel can gain access to sensitive areas or patient records. This helps prevent unauthorized individuals from accessing confidential information, thus safeguarding patient privacy and further enhancing overall patient safety.
Furthermore, biometrics offer real-time monitoring and tracking capabilities that can greatly improve patient care. For instance, wearable biometric devices can continuously monitor vital signs such as heart rate, blood pressure, and oxygen levels. This allows healthcare providers to closely monitor patients remotely and detect any abnormalities or emergencies promptly. With this real-time data at their fingertips, doctors and nurses can provide timely interventions, leading to better outcomes for patients.
Streamlining Administration Processes
Another area where biometrics prove invaluable is in streamlining administration processes within healthcare settings. Traditional administrative tasks such as patient registration and check-in processes often involve manual paperwork that can be time-consuming and prone to errors. However, with the use of biometric authentication systems, these processes can be streamlined efficiently.
By implementing biometric solutions for patient registration, hospitals can eliminate the need for repetitive paperwork. Patients simply need to authenticate themselves using their unique biological traits like fingerprints or facial recognition instead of filling out multiple forms manually. This not only saves time but also reduces the chances of errors caused by illegible handwriting or incorrect data entry.
Moreover, automating administrative processes with biometrics improves overall efficiency within healthcare facilities. For example, biometric systems can be integrated with electronic health record (EHR) systems, allowing for seamless access to patient information. This eliminates the need for healthcare professionals to search through physical files or navigate complex digital interfaces, enabling them to focus more on providing quality care to patients.
Overview of Future Trends in Biometrics for Healthcare
Personalized Medicine and Biometrics
Biometrics, such as fingerprint scans and iris recognition, are revolutionizing the healthcare industry by enabling personalized medicine. With biometric data, healthcare providers can gather individualized patient information that goes beyond traditional medical records. This allows for the development of tailored treatment plans based on a patient’s unique biometric profile.
For example, biometric sensors integrated into wearable devices can continuously monitor vital signs like heart rate, blood pressure, and oxygen levels. This real-time data provides valuable insights into a patient’s health status and helps healthcare professionals make more informed decisions about their care.
Precision medicine is another area where biometrics play a crucial role. By integrating biometric information into healthcare systems, doctors can identify genetic markers that may influence an individual’s response to certain medications or treatments. This helps optimize treatment plans and increases the chances of successful outcomes.
Artificial Intelligence in Smarter Healthcare Solutions
Artificial intelligence (AI) is transforming the way healthcare solutions utilize biometrics. AI-powered systems can analyze vast amounts of patient data quickly and accurately, leading to better diagnosis and treatment options.
Machine learning algorithms enhance the accuracy and reliability of biometric solutions by continuously learning from new data inputs. This enables AI-driven healthcare platforms to adapt and improve over time, providing more precise insights into patients’ conditions.
One significant advantage of AI-driven healthcare solutions is their ability to leverage biometrics for improved patient outcomes. For instance, AI algorithms can detect patterns in large datasets that human clinicians might miss. By analyzing these patterns alongside biometric information, AI systems can predict disease progression or identify potential risks early on.
Moreover, AI-powered chatbots equipped with voice recognition technology enable patients to interact with virtual assistants for preliminary diagnoses or general health inquiries. These chatbots use natural language processing algorithms to understand patients’ concerns accurately and provide appropriate responses or recommendations based on their individual health profiles.
Impact of Biometrics on Patient Care
Biometrics, the use of unique physical or behavioral characteristics for identification purposes, is revolutionizing the healthcare industry.
Accurate Patient Identification
One of the most critical aspects of healthcare is accurate patient identification. Mistaken identity or patient misidentification can lead to serious medical errors, including incorrect treatment plans and medication administration. However, biometric authentication provides a reliable solution to this problem.
By utilizing biometric identifiers such as fingerprints, palm prints, or iris scans, healthcare providers can accurately identify patients and link them to their correct medical records. This eliminates the risk of duplicate medical records and ensures that each patient receives personalized care based on their specific needs.
According to a study published in the Journal of Patient Safety, misidentification errors occur at an alarming rate of 1 in every 1,000 hospital admissions. By implementing biometrics for patient identification, hospitals and healthcare facilities can significantly reduce these errors and improve overall patient safety.
Imagine a scenario where a patient with allergies is mistakenly given medication they are allergic to due to an identification error. Biometric authentication would prevent such incidents by accurately identifying the patient before administering any treatment.
Strengthening EHR Security with Biometrics
In today’s digital age, protecting sensitive patient data stored within electronic health records (EHRs) is crucial. Unauthorized access to EHRs can result in data breaches and identity theft, compromising both patients’ privacy and healthcare organizations’ reputation. This is where biometrics play a vital role in enhancing EHR security.
Traditional methods of securing EHRs like passwords or PIN codes are often vulnerable to hacking or unauthorized access through stolen credentials. Biometric authentication adds an extra layer of security by using unique biological traits that cannot be easily replicated or stolen.
By integrating biometric authentication into EHR systems, healthcare organizations can ensure that only authorized individuals, such as doctors and nurses, can access patient records. This not only safeguards patient privacy but also helps to maintain the integrity of medical data.
According to a survey conducted by HIMSS Analytics, 75% of healthcare organizations reported using biometrics for EHR security. This widespread adoption demonstrates the industry’s recognition of the effectiveness of biometrics in protecting patient data and preventing unauthorized access.
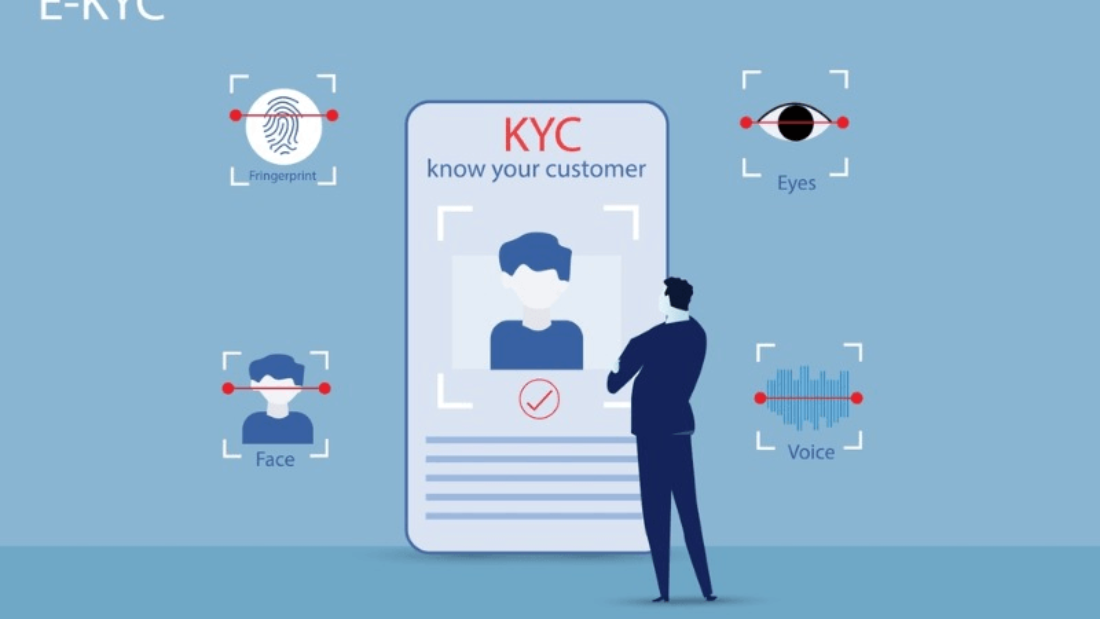
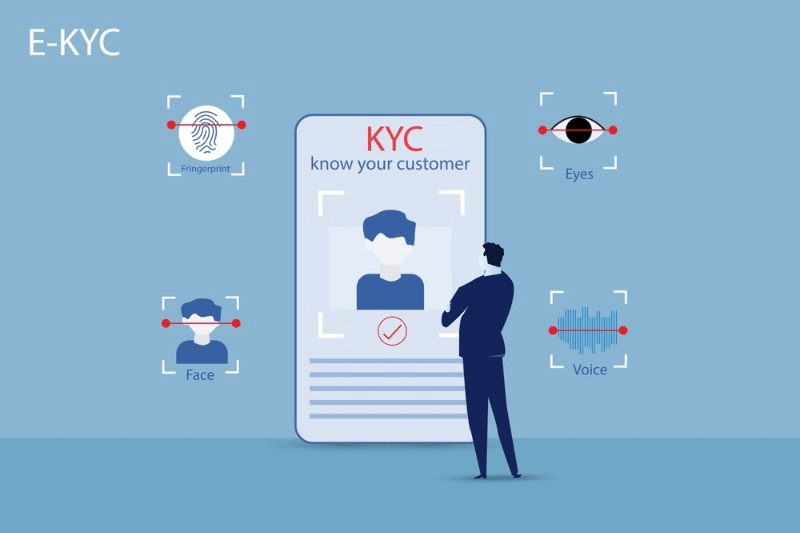
Applications of Biometrics in the Healthcare Industry
Biometrics, the use of unique physical or behavioral characteristics for identification and authentication purposes, is revolutionizing the healthcare industry. It offers a wide range of applications that enhance security, convenience, and accessibility in healthcare facilities. Let’s explore two key areas where biometrics are making a significant impact: access control solutions and telemedicine/remote patient monitoring.
Access Control Solutions for Healthcare Facilities
Biometric access control systems play a crucial role in enhancing security within healthcare facilities. With traditional methods like keys or ID cards being susceptible to loss or theft, biometrics offer a more secure and convenient way to manage access permissions. By utilizing features such as fingerprint recognition or iris scanning, unauthorized access to restricted areas can be effectively prevented.
The integration of biometric authentication not only ensures the physical security of healthcare facilities but also safeguards sensitive patient data stored within electronic health records (EHRs). Only authorized personnel with their unique biometric traits can gain access to these records, protecting patient privacy and preventing data breaches.
Biometrics streamline administrative processes by eliminating the need for manual check-ins or password-based systems. This saves time for both patients and staff while reducing administrative errors. Patients can easily verify their identities using biometric traits such as fingerprints during registration, ensuring accurate record-keeping throughout their healthcare journey.
Telemedicine and Remote Patient Monitoring
In recent years, telemedicine has gained popularity as an efficient means of delivering healthcare services remotely. Biometrics play a vital role in enabling secure telemedicine consultations and remote patient monitoring.
With remote patient monitoring, healthcare providers can track patients’ vital signs from a distance using wearable devices equipped with biometric sensors. These sensors measure parameters like heart rate, blood pressure, and oxygen levels, providing real-time data that helps clinicians monitor patients’ health conditions remotely. This technology is particularly beneficial for individuals with chronic illnesses who require regular monitoring without frequent hospital visits.
Biometric authentication ensures the security and privacy of telemedicine consultations. By implementing features like facial recognition or voice recognition, healthcare providers can verify the identities of patients and ensure that sensitive medical information is shared only with authorized individuals.
Furthermore, remote patient monitoring with biometrics improves accessibility to healthcare services, especially for individuals residing in remote or underserved areas. Patients can receive timely medical advice and intervention without the need for physical visits to healthcare facilities, reducing costs and improving overall healthcare outcomes.
Empowering Patients and Staff with Biometric Technology
Self-Service Healthcare Solutions
Biometric self-service kiosks are revolutionizing the way patients interact with healthcare facilities. These innovative devices empower patients to take control of their healthcare journey by offering a range of convenient services. With biometric authentication, patients can check-in, schedule appointments, and access their medical records independently. This eliminates the need to wait in long queues or rely on administrative staff for basic tasks.
One key advantage of biometric self-service solutions is the reduction in waiting times. By streamlining the check-in process, patients can quickly complete necessary procedures and proceed directly to their appointments. This not only improves patient satisfaction but also optimizes resource allocation within healthcare facilities.
Moreover, biometric self-service kiosks enable patients to conveniently update their personal information. Instead of filling out paper forms or relying on administrative staff, individuals can use biometric authentication to securely update their details in real-time. This ensures that healthcare providers have accurate and up-to-date information when delivering care.
Efficient Time and Attendance Tracking
In addition to empowering patients, biometrics also enhance efficiency in time and attendance tracking for healthcare professionals. Traditional methods of recording working hours often involve manual processes that are prone to errors and inaccuracies. However, with biometric technology, these systems are automated and provide a reliable means of tracking employee attendance.
By implementing biometric time clocks, healthcare organizations can accurately record the working hours of their staff members. This ensures fair compensation for employees based on actual hours worked. It eliminates any discrepancies or disputes that may arise from manual attendance management systems.
The use of biometrics in time and attendance tracking also promotes accountability among healthcare professionals. With accurate records readily available, supervisors can easily monitor employee punctuality and identify any patterns of absenteeism or tardiness. This allows for timely intervention when necessary and helps maintain a high level of productivity within the workforce.
Real-World Applications and the Future Landscape
Automation in Clinical Trials and Research
Biometric technology has revolutionized the field of clinical trials and research, offering a range of benefits that streamline processes and enhance efficiency. With the use of biometrics, participant enrollment and data collection have become more efficient than ever before. By implementing biometric systems, researchers can accurately identify and enroll participants, ensuring that they meet the necessary criteria for the study. This not only saves time but also improves the accuracy of data collection.
Moreover, automated data analysis using biometric technology expedites the research process. Traditionally, researchers would spend countless hours manually analyzing data collected during clinical trials. However, with biometrics, this task becomes much simpler and quicker. Biometric systems can automatically analyze vast amounts of data in real-time, providing valuable insights to researchers promptly.
Biometrics improve the accuracy and reliability of clinical trial results. By utilizing biometric identifiers such as fingerprints or facial recognition, researchers can ensure that participants’ identities are verified accurately throughout the duration of the study. This helps eliminate any potential errors or discrepancies in data collection, leading to more reliable outcomes.
Enhanced Access Control for Improved Security
In healthcare organizations where security is paramount, biometric access control systems have emerged as a game-changer. These systems strengthen security measures by allowing only authorized personnel to gain access to sensitive areas within healthcare facilities. With traditional access cards or keys being prone to loss or theft, biometrics offer a more secure alternative.
By implementing biometric authentication methods such as fingerprint scans or iris recognition, healthcare organizations can significantly reduce the risk of unauthorized entry. These unique biological characteristics serve as an impenetrable barrier against individuals attempting to gain unauthorized access to restricted areas.
Furthermore, biometric access control eliminates the need for cumbersome physical keys or access cards that can be easily misplaced or duplicated. This not only enhances security but also streamlines access management processes, saving time for both staff and patients.
The future of biometrics in healthcare holds even more exciting possibilities. Ongoing developments in areas such as virtual reality and data science applications are set to revolutionize the industry further. For instance, virtual reality combined with biometric technology can provide immersive experiences for patients during therapy sessions or pain management procedures, enhancing their overall well-being.
Biometrics Revolutionizing Healthcare Across Various Industries
Impact on Banking, Financial Services, and Beyond
Biometric technology is not limited to the healthcare industry; it has also found applications in banking and financial services. The integration of biometrics in these industries ensures enhanced security and convenience for both businesses and customers.
One significant impact of biometrics in banking and financial services is secure authentication for transactions. Traditional methods like passwords or PINs can be easily compromised, leading to fraudulent activities. Biometrics, on the other hand, utilize unique physical or behavioral characteristics such as fingerprints, iris scans, or voice recognition to verify a person’s identity. This provides an additional layer of security, minimizing the risk of fraud and unauthorized access to accounts.
According to market research reports, the global biometrics market in the banking sector is expected to reach a value of $5.8 billion by 2025[^1^]. This indicates the growing adoption of biometric solutions in this industry due to their effectiveness in combating fraud and improving customer experience.
Apart from banking and financial services, biometrics have also made their way into various other sectors. For instance, airports are increasingly using biometric data like facial recognition for seamless passenger identification during check-ins and security screenings[^2^]. This streamlines processes while ensuring accurate identification without compromising security.
Transforming Medical Practices through Biometrics
Biometric solutions are revolutionizing medical practices by enhancing efficiency, accuracy, and patient care. Healthcare providers can leverage biometric technology to deliver better outcomes for their patients.
One area where biometrics have proven beneficial is patient identification. By using unique identifiers such as fingerprints or palm vein patterns, healthcare facilities can accurately match patients with their medical records. This eliminates errors caused by manual record-keeping or mistaken identities that could lead to incorrect treatments or delays in care.
Furthermore, integrating biometric solutions into medical practices improves operational efficiency. For example, hospitals can use fingerprint scanners to provide secure access to restricted areas, ensuring that only authorized personnel can enter. This prevents unauthorized individuals from gaining access to sensitive patient information or medical supplies.
Biometrics also play a crucial role in telemedicine and remote patient monitoring. With the use of wearable devices equipped with biometric sensors, healthcare professionals can remotely monitor patients’ vital signs and health data. This enables early detection of any anomalies or changes in a patient’s condition, allowing for timely interventions and personalized care.
Preparing for a Future with Reliable Biometric Authentication
Creating Secure Authentication Platforms
Biometrics, such as fingerprint recognition and facial recognition, offer a highly secure method of user authentication across different platforms. Unlike passwords and PINs that can be easily forgotten or hacked, biometric authentication relies on unique physical characteristics that are difficult to replicate. This makes it an ideal solution for strengthening security in healthcare.
By implementing biometrics as the primary means of authentication, healthcare organizations can eliminate the vulnerabilities associated with traditional password-based systems. With biometric authentication, individuals no longer need to remember complex passwords or worry about their credentials being stolen. Instead, they can simply use their fingerprint or face to gain access to sensitive medical information.
Moreover, biometric authentication can be combined with other factors such as a PIN or token for multi-factor authentication. This provides an extra layer of protection against unauthorized access by requiring multiple forms of identification. By leveraging these advanced security measures, healthcare providers can ensure that only authorized personnel have access to patient records and critical systems.
Empowering Advancements in Biometric Research
Ongoing research in biometrics is driving continuous advancements in the field and opening up new possibilities for healthcare applications. Researchers are constantly exploring innovative ways to improve the accuracy and reliability of biometric identification methods.
For example, advancements in facial recognition technology have made it possible to detect emotions and monitor vital signs through facial expressions. This has significant implications for healthcare professionals who can use this data to assess patients’ well-being remotely or identify early warning signs of certain conditions.
Furthermore, researchers are developing new techniques to enhance fingerprint recognition accuracy by considering factors such as sweat pores and vein patterns beneath the surface of the skin. These developments not only improve the reliability of fingerprint-based authentication but also expand its potential applications beyond traditional use cases.
The continuous progress in biometric research is crucial for ensuring that healthcare organizations stay ahead in terms of security and efficiency. As more sophisticated biometric technologies emerge, healthcare providers will be able to offer improved patient experiences while safeguarding sensitive data.
Conclusion
In conclusion, the future of biometrics in healthcare is promising and holds immense potential for revolutionizing the industry. Biometric technology offers a secure and efficient way to authenticate patients, protect sensitive medical information, and streamline healthcare processes. With advancements in biometric sensors, artificial intelligence, and data analytics, the applications of biometrics in healthcare are expanding rapidly.
By leveraging biometric authentication methods such as fingerprint recognition, facial recognition, and voice recognition, healthcare providers can enhance patient care, improve operational efficiency, and reduce medical errors. Biometrics also empower patients with greater control over their health data and enable seamless access to healthcare services. Moreover, the integration of biometrics with wearable devices and telemedicine platforms opens up new possibilities for remote monitoring and personalized healthcare.
As we move forward, it is crucial for healthcare organizations to embrace biometric technology and invest in robust security measures to protect patient privacy. Policymakers should also establish guidelines and regulations to ensure ethical use of biometrics in healthcare. By harnessing the power of biometrics responsibly, we can create a future where healthcare is more accessible, efficient, and secure.
Frequently Asked Questions
FAQ
Can you explain the basics of biometric technology?
Biometric technology uses unique physical or behavioral characteristics, such as fingerprints, iris patterns, or voice recognition, to identify and authenticate individuals. It offers a highly secure and reliable method of identification that is difficult to forge or replicate.
How does biometrics go beyond security in healthcare?
Beyond security, biometrics plays a crucial role in healthcare by streamlining processes like patient identification, access control, and medication administration. It enhances efficiency, reduces errors, and improves patient care by ensuring accurate identification and providing quick access to medical records.
What are some future trends in biometrics for healthcare?
Future trends in biometrics for healthcare include advancements in wearable biometric devices, remote patient monitoring using biometric sensors, integration of artificial intelligence for real-time analysis of biometric data, and the use of facial recognition technology for contactless identification.
How does biometrics impact patient care?
Biometrics positively impacts patient care by eliminating duplicate medical records through accurate patient identification. It also ensures that patients receive the correct medications and treatments by verifying their identity before administering any procedures. This helps prevent medical errors and enhances overall patient safety.
In which areas is biometric technology applied within the healthcare industry?
Biometric technology finds applications in various areas within the healthcare industry such as access control to restricted areas, securing electronic health records (EHRs), tracking staff attendance and time management, monitoring vital signs remotely through wearables, verifying patients’ identities during appointments or emergencies.




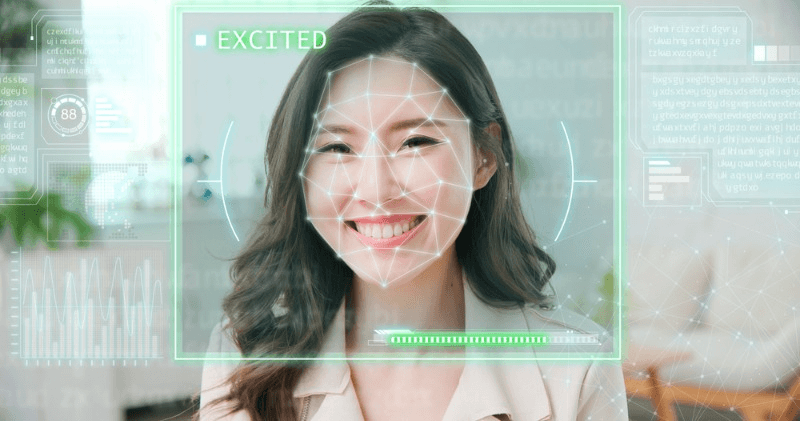

 Advanced facial clocking solutions come equipped with a range of features that further enhance their functionality and usability. These clock systems offer real-time monitoring capabilities that allow employers to track employee attendance instantly. Managers can easily view the attendance status of employees using the time clock system, which eliminates the need for manual processes or waiting for reports.
Advanced facial clocking solutions come equipped with a range of features that further enhance their functionality and usability. These clock systems offer real-time monitoring capabilities that allow employers to track employee attendance instantly. Managers can easily view the attendance status of employees using the time clock system, which eliminates the need for manual processes or waiting for reports.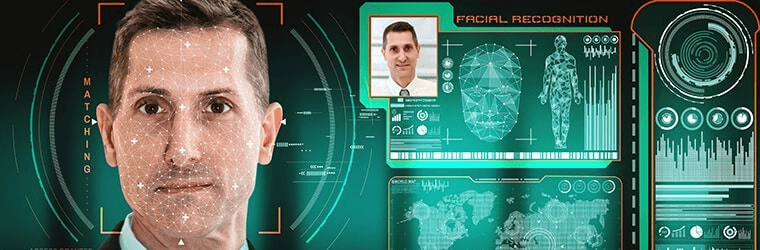



 The process begins with high-resolution cameras capturing employee data through facial images on the time clock. These images captured by the time clock are then processed using complex algorithms that analyze unique facial features such as the distance between eyes, nose shape, and jawline structure. This meticulous analysis ensures accurate identification while minimizing false positives or negatives using a time clock.
The process begins with high-resolution cameras capturing employee data through facial images on the time clock. These images captured by the time clock are then processed using complex algorithms that analyze unique facial features such as the distance between eyes, nose shape, and jawline structure. This meticulous analysis ensures accurate identification while minimizing false positives or negatives using a time clock.


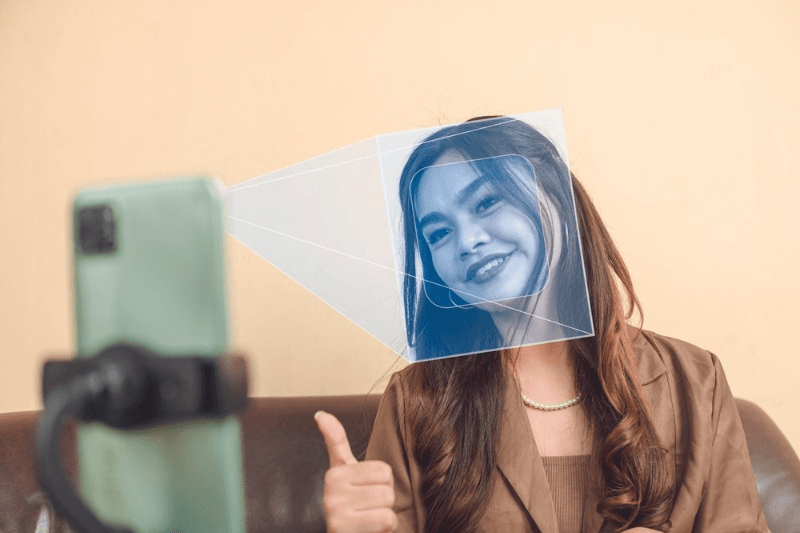
 The benefits offered by face recognition technology have led to its widespread adoption across various industries. From educational institutions to corporate offices and healthcare facilities, organizations are increasingly recognizing the value of this advanced system for
The benefits offered by face recognition technology have led to its widespread adoption across various industries. From educational institutions to corporate offices and healthcare facilities, organizations are increasingly recognizing the value of this advanced system for