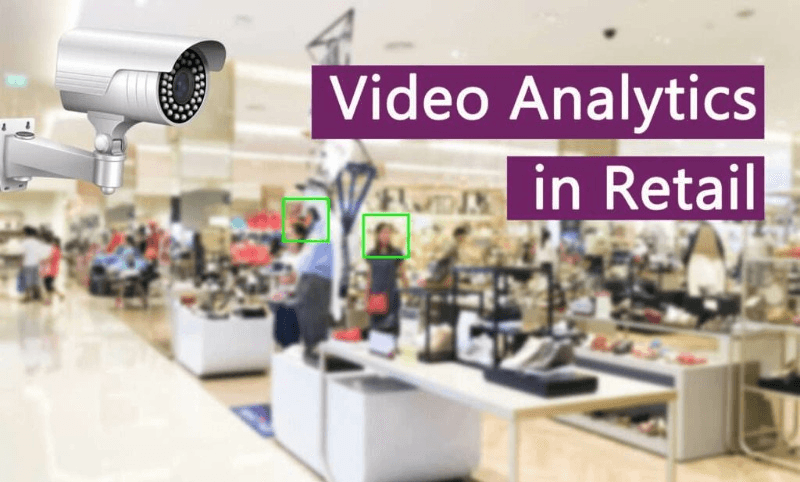
Ever wondered how fitness centers are making data-driven decisions to optimize operations for health and quality? Video analytics is the game-changer. This technology isn’t just about security – it’s a powerful tool providing valuable insights into member behavior, equipment usage, facility traffic, and active video. From understanding peak hours to optimizing class schedules, video analytics offers a variety of benefits for health clubs worldwide. By leveraging this active video technology, fitness centers can create personalized experiences that keep members, audience, and viewers coming back for more. With real-time data and sound metrics at their fingertips, managers can make informed decisions that enhance member satisfaction and drive business growth.///
Fitness Center Video Analytics Overview
Applications and Uses
Video analytics for fitness centers serves multiple purposes. It allows monitoring customer behavior, preferences, movement patterns, and audience within the facility. For instance, it can track which areas of the gym are most frequented or which equipment is popular among members. The sentence does not need to be modified.
Moreover, fitness centers utilize video analytics to analyze and improve workout performance for their audience. By tracking how customers interact with equipment and measuring their movements during exercises, staff can gain insights into how to optimize the layout of the gym floor or modify training programs for better results. ///
Technology Integration
The integration of video analytics technology into fitness centers’ existing systems has been seamless for the audience. This technology can be easily incorporated with surveillance cameras already installed in various areas of the facility such as entrances, workout zones, locker rooms, and parking lots. The amalgamation of these systems enhances overall operational efficiency while providing a comprehensive view of all activities within the center.
Impact on Operations
Video analytics significantly streamline operational processes in fitness centers by optimizing resource allocation based on data-driven insights gathered from member behavior analysis. For example, if certain areas are consistently crowded at specific times throughout the day or week due to classes or peak hours for workouts; resources like staff scheduling could be adjusted accordingly to meet demand efficiently.
Furthermore,video analytics improves staff productivity, allowing them to focus more on delivering quality service rather than spending time manually analyzing data trends that can now be effortlessly derived through this technology’s automated process.
Future Trends
The future landscape for fitness center management will undoubtedly rely heavily on advanced video analytics solutions powered by artificial intelligence (AI). These technologies will provide even more accurate and detailed insights into customer behavior patterns within facilities while also enabling predictive modeling capabilities that anticipate member needs before they arise.
Enhancing Gym Security
AI for Dumbbell Workouts
AI-powered video analytics can revolutionize the way dumbbell workouts are monitored at fitness centers. By using advanced algorithms, these systems can analyze dumbbell exercises in real-time, offering personalized recommendations to members based on their performance. For instance, if a member is not maintaining the correct form during a workout, the AI algorithm can detect this and provide immediate feedback or correction suggestions.
Furthermore, these AI algorithms have the capability to identify incorrect techniques or forms during dumbbell exercises. This ensures that gym-goers are performing their workouts safely and effectively. With this technology in place, fitness centers can offer an added layer of security by actively monitoring and guiding members through their exercise routines.
HD Surveillance Systems
High-definition (HD) surveillance cameras play a pivotal role in enhancing gym security through video analytics. These cameras capture clear and detailed footage within fitness centers, enabling precise tracking of customer movements. The clarity provided by HD surveillance systems significantly enhances the effectiveness of video analytics as it allows for accurate analysis of individual actions and behaviors within the facility.
The use of HD surveillance footage also aids in identifying any suspicious activities or unauthorized access within the premises. This proactive approach to security helps create a safe environment for all individuals utilizing the fitness center’s facilities.
Smart Presence Technology
Smart presence technology leverages video analytics to track customer presence across different areas within a fitness center. By analyzing foot traffic patterns and occupancy data, this technology enables gyms to optimize space utilization efficiently while ensuring maximum comfort for its patrons.
Moreover, smart presence technology provides real-time insights into crowd management by monitoring occupancy levels at various sections of the facility. Fitness centers can utilize this information to implement strategies that enhance customer experience while maintaining safety protocols during peak hours or special events.
Optimizing Gym Operations
Video Analysis Benefits
Video analytics for fitness centers offers numerous benefits. By analyzing video footage, fitness center management can identify the most popular workout areas, helping them optimize equipment placement to meet customer demand more effectively. This means ensuring that the most sought-after machines and exercise spaces are readily available to members when they need them. video analysis provides valuable insights into customer preferences and behavior within the fitness center, enabling management to tailor their services and offerings accordingly.
Implementing video analytics also allows health clubs to remotely monitor operations with ease. Through remote management systems, real-time access to video feeds from anywhere is possible. This capability enables staff to keep a close eye on all areas of the facility without being physically present at all times. Moreover, it facilitates quick troubleshooting and issue resolution as problems can be identified promptly through video surveillance.
Remote Management Systems
Remote management systems equipped with video analytics for fitness centers offer unparalleled convenience and efficiency in overseeing gym operations from afar. These systems provide a level of control that was previously unattainable without physical presence on-site, allowing managers to address issues swiftly before they escalate.
The use of video analytics extends beyond general gym operations; it’s also employed in analyzing sports performance within fitness centers. Athletes benefit greatly from detailed feedback on their technique and form derived from video analysis tools installed in these facilities. Such feedback helps athletes identify areas for improvement while tracking their progress over time.
Business Growth through Video Analytics
Video analytics for fitness centers plays a crucial role in evaluating the effectiveness of marketing strategies. By utilizing video analytics data, fitness centers can target specific customer demographics more accurately. For instance, if the data shows that a particular age group engages more with strength training videos, the center can tailor their marketing efforts towards that demographic.
Integrating video analytics with marketing strategies enhances customer engagement by providing content that resonates with their interests and preferences. This results in higher interaction rates and better conversion from prospects to leads and eventually paying customers.
Fitness centers can leverage video analytics to measure the success of various marketing campaigns. For example, they can track which types of workout videos receive the most views or shares on social media platforms. This information helps them understand what type of content is popular among their audience and adjust their marketing strategy accordingly.
Brand Promotion Leverage
Leveraging video analytics, fitness centers are able to promote their brand effectively by creating targeted promotional content based on customer preferences. If video analytics reveals that customers engage more with yoga-related content, the center can create promotional material centered around yoga classes or products.
By understanding consumer behavior through video analytics, fitness centers are better equipped to increase brand visibility and awareness. They can tailor advertising campaigns based on insights gained from video metrics such as viewer retention rates, average watch time, and click-through rates.
Using these insights allows businesses to craft compelling ad messages that resonate with potential clients’ needs and desires—ultimately leading to increased brand recognition within the community served by the fitness center.
Consistent Video Production
Consistent video production ensures a steady flow of engaging content for fitness centers’ audiences. Regularly producing videos keeps customers engaged and motivated while also attracting new prospects who find value in this consistent stream of informative or entertaining material.
Video analytics aids in identifying popular video content for continuous production; it provides insight into which topics generate high viewer interest or drive significant engagement levels across different online platforms like YouTube or Instagram TV.
Video Marketing Strategies for Fitness Centers
Video analytics for fitness centers plays a crucial role in creating high-quality and relevant content. By analyzing viewer engagement, fitness centers can produce impactful videos that resonate with their audience. This data-driven approach ensures that the content meets the needs and preferences of the viewers, ultimately driving customer satisfaction and loyalty.
For instance, if video analytics reveal that viewers tend to drop off after a certain point in a workout tutorial video, fitness centers can use this information to refine future videos by adjusting pacing or providing additional explanations at critical points. This iterative process allows fitness centers to continuously improve their content based on real-time feedback from their audience.
Furthermore, understanding which types of videos perform best – whether it’s instructional workouts, nutrition tips, or success stories – enables fitness centers to tailor their content strategy accordingly. By consistently delivering valuable and engaging content through video analytics insights, fitness centers can establish themselves as trusted sources of information within the industry.
In addition to refining content creation strategies, video analytics for fitness centers also assists in optimizing call-to-action (CTA) implementation in videos. By tracking CTA click-through rates using video analytics data, fitness centers gain valuable insights into how viewers are responding to prompts within the videos.
By strategically placing CTAs at optimal points within the video based on analytical data findings rather than guesswork alone increases conversions significantly for calls-to-action such as signing up for membership trials or booking personal training sessions.
Moreover, fitness centers leverage video analytics insights to maximize the potential of their videos by analyzing viewer behavior. Understanding how long viewers engage with specific types of content helps optimize video length and format while tailoring them according to different platforms like social media or website integration.
This level of optimization not only enhances customer engagement but also contributes significantly towards viewer retention as they find more value in consuming these tailored contents.
Leveraging Video Content for Branding
Crafting Successful Strategies
Video analytics data is a powerful tool for fitness centers to craft successful marketing and operational strategies. By analyzing videos, fitness centers can make data-driven decisions, leading to improved business performance. For example, if video analytics show that a certain type of workout video receives more views or engagement, the fitness center can tailor its marketing efforts accordingly.
Crafting successful strategies using video analytics isn’t just about marketing; it also extends to operational decisions. For instance, if video analytics reveal that certain equipment or classes are consistently featured in popular videos, the fitness center can adjust its offerings to meet customer demand accurately. This strategic use of video analytics ensures that the center’s resources are allocated effectively.
Fitness Video Consistency
Consistent production of fitness videos plays a crucial role in maintaining a reliable content schedule for customers. Through video analytics, fitness centers can track which types of videos resonate most with their audience and then ensure a steady stream of similar content. This consistency helps establish and maintain a strong brand image across all videos.
Maintaining uniformity in fitness videos through the use of video analytics contributes significantly to building customer trust and loyalty. When viewers know what kind of content to expect from the fitness center’s videos, they are more likely to engage regularly with the brand’s online presence.
Customer Engagement
Understanding customer preferences is key. With insights gained from video analytics, these establishments can create engaging videos tailored specifically to their audience’s interests and needs.
By tailoring their content based on video analytic insights, such as preferred workout styles or class formats, fitness centers have an opportunity not only to attract new customers but also retain existing ones over time.
Engaging customers through personalized and relevant content fosters long-term relationships between members and the fitness center itself.
Empowering Gym Safety with Surveillance Tech
Advanced surveillance solutions in fitness centers incorporate cutting-edge video analytics technology to provide comprehensive monitoring capabilities. These systems offer enhanced security and analysis, benefiting fitness centers in numerous ways. For instance, they can identify suspicious activities or potential threats through real-time video analysis.
Moreover, these advanced surveillance solutions enable fitness centers to enhance their overall safety measures by continuously monitoring the premises. This constant vigilance ensures that any emergencies or safety concerns are promptly addressed, contributing to a safer environment for all members and staff.
Fitness center owners can leverage the power of video analytics technology within their surveillance systems to gain insights into member behavior and facility usage patterns. By analyzing this data, they can make informed decisions about improving equipment placement, optimizing space utilization, and enhancing customer experience.
Customer Protection Enhancement
Video analytics plays a crucial role in enhancing customer protection within fitness centers. Through advanced surveillance solutions, fitness center management can proactively identify and address safety concerns such as overcrowding in certain areas or unauthorized access to restricted zones.
This proactive approach not only ensures the physical well-being of members but also builds trust and confidence among them. When members feel safe and secure within the premises of a fitness center, it fosters a positive relationship between the establishment and its clientele.
By leveraging video analytics for customer protection enhancement purposes, fitness centers demonstrate their commitment to providing a secure environment where members’ well-being is prioritized at all times.
24/7 Security Cameras
The implementation of 24/7 security cameras significantly contributes to round-the-clock monitoring in fitness centers. These cameras equipped with video analytics capabilities enable real-time alerts for any suspicious activities or emergencies that may arise within the facility.
For example:
In case of an accident on gym equipment,
If someone attempts unauthorized access after hours,
Or if there’s an unexpected altercation between patrons,
the 24/7 security cameras equipped with video analytics would promptly alert staff so that immediate action could be taken. Continuous surveillance through these security cameras serves as a powerful deterrent against misconduct while also providing valuable evidence in case incidents occur within the facility.
Analyzing Performance with Video Solutions
Workout Analysis Automation
Workout analysis automation, powered by video analytics for fitness centers, is a game-changer. Imagine the time and effort saved when workout analysis is automated. Instead of manually reviewing each session, fitness centers can now analyze multiple workouts simultaneously using automated processes. This not only saves time but also improves efficiency and accuracy in assessing performance. For instance, a gym can track the number of reps or monitor body posture during weightlifting exercises through video analytics without human intervention.
The benefits are substantial – from reducing the burden on staff to providing more detailed insights into members’ progress. With workout analysis automation, fitness centers can ensure that every member’s performance is thoroughly evaluated without compromising accuracy or quality.
Saves time and effort
Allows simultaneous analysis of multiple workouts
Enhances efficiency and accuracy in performance assessment
Computer Intelligence in Coaching
Computer intelligence combined with video analytics opens up new possibilities for personalized training programs at fitness centers. Coaches can leverage computer intelligence to provide tailored guidance based on individual workout sessions analyzed through video solutions. This level of customization optimizes training effectiveness as it caters to each member’s specific needs.
For example, an AI-powered system could identify areas where a member needs improvement and suggest personalized exercise routines accordingly. By harnessing computer intelligence in coaching, fitness centers can offer unparalleled support to their members while ensuring that they achieve their desired results effectively.
Enables personalized training programs
Optimizes training effectiveness through customization
Provides tailored guidance based on individual workout sessions
Impact on Fitness Training
The impact of video analytics on fitness training cannot be overstated; it revolutionizes the way workouts are conducted at gyms worldwide. Real-time feedback provided through video analysis significantly enhances the effectiveness of workouts by allowing immediate adjustments based on accurate data insights gathered during exercises.
Consider a scenario where a member receives instant feedback about their form during a squatting exercise via video analytics software integrated into gym equipment screens – this real-time input allows them to make necessary corrections immediately for better results.
Fitness training with video analytics brings forth comprehensive improvements in overall performance by leveraging technology to refine traditional approaches towards achieving optimal results efficiently.
The Future of Fitness Analytics Technology
Fitness centers are increasingly embracing smart technology solutions powered by video analytics to enhance their operations and customer experience. By integrating smart devices with video analytics, fitness centers can significantly improve operational efficiency and overall customer satisfaction.
For example, fitness centers can utilize video analytics to monitor the usage of equipment in real-time. This data helps them understand which machines are popular among members, allowing for better placement and maintenance scheduling.
Moreover, through the adoption of smart technology solutions like video analytics, fitness center staff can gain valuable insights into member behavior. They can identify peak hours of foot traffic within the facility and adjust staffing levels accordingly to ensure a seamless experience for all members.
The integration of smart technology not only streamlines day-to-day operations but also creates an environment that is more conducive to achieving fitness goals.
Crafting a Gym Video Strategy
Fitness centers use video analytics to align their operations with business goals. By leveraging video analytics data, they can track progress towards achieving these objectives. For instance, if a fitness center aims to increase membership retention by 15% within the next year, they can utilize video analytics to monitor member engagement and satisfaction levels.
This alignment allows them to make informed decisions that contribute to the overall success of the business. By understanding members’ preferences and behavior through video analysis, fitness centers can tailor their offerings and services accordingly. This approach not only enhances customer satisfaction but also increases loyalty and retention rates.
Engaging Audience with Content
Utilizing video analytics, fitness centers are able to create engaging content that resonates with their audience. They can identify viewer preferences through analysis of metrics such as watch time, likes, comments, and shares on various videos. For example, if a gym’s audience engages more with high-intensity workout videos compared to yoga sessions, they can focus on creating more content in line with this preference.
Tailoring videos based on viewer preferences ensures that the content is relevant and appealing to the target audience. As a result, this strategy leads to increased viewership and customer satisfaction.
Tracking and Analyzing Results
Through video analytics, fitness centers have the capability to track and analyze results effectively using key performance indicators (KPIs). Metrics such as conversion rates from video views to membership sign-ups or class bookings provide valuable insights for decision-making processes.
Conclusion
Congratulations on reaching the end of this fitness analytics journey! You’ve uncovered the immense potential of video analytics for fitness centers, from enhancing security to optimizing operations and driving business growth. As you craft your gym’s video strategy, remember that leveraging surveillance technology isn’t just about safety – it’s a powerful tool for analyzing performance and boosting branding through video marketing strategies. The future of fitness analytics is in your hands, so embrace this technology to propel your gym to new heights!
Now, it’s time to put your newfound knowledge into action. Start by evaluating your gym’s current video setup and identify areas where analytics can make a difference. Whether it’s refining security measures, streamlining operations, or engaging members through compelling video content, there’s a world of opportunities waiting for you. Get ready to revolutionize your fitness center with the transformative power of video analytics!
Frequently Asked Questions
How can video analytics benefit fitness centers?
Video analytics can provide valuable insights into member behavior, equipment usage, and facility traffic flow. By analyzing this data, fitness centers can optimize operations, enhance security, and tailor marketing strategies to attract more members.
What are the key aspects of gym security that video analytics can enhance for health clubs and fitness businesses during training sessions?
Video analytics can improve gym security by monitoring access control, detecting unauthorized entry or suspicious behavior, and providing real-time alerts for potential safety threats. This technology helps in creating a safer environment for members and staff.
How does video content, such as explainer videos, contribute to branding for fitness centers, health clubs?
Utilizing engaging video content allows fitness centers to showcase their facilities, services, and success stories effectively. It helps in building brand identity, connecting with the target audience emotionally, and differentiating from competitors in the highly competitive fitness industry.
In what ways does active video surveillance tech empower safety measures in gyms, health clubs, and fitness businesses?
Surveillance tech enables proactive monitoring of various areas within a gym facility to ensure the safety of members and staff. It acts as an extra set of vigilant eyes that can help prevent accidents or respond promptly in case of emergencies.
What is the significance of crafting a dedicated video strategy for gyms and fitness businesses?
Crafting a tailored video strategy ensures that gyms maximize the impact of their visual content across various platforms such as social media channels and websites. A well-thought-out strategy helps in reaching a wider audience while conveying a compelling message about the gym’s offerings.