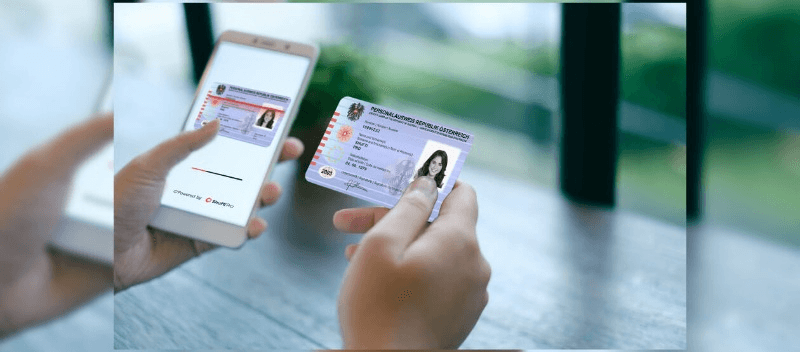
Identity verification, using verifiable credentials and biometric authentication, is a crucial process in today’s digital world. With the increasing reliance on biometric data and the advancements in blockchain technology, ensuring secure and trustworthy identity verification has become more important than ever. As we navigate an era where most services and activities are conducted online, establishing trust and ensuring the security of personal information has become paramount. Verifiable credentials play a crucial role in identity management and remote identity verification, helping to prevent identity theft. However, traditional methods of identity verification, such as checks, no longer suffice in this rapidly evolving landscape of digital identification and verifiable credentials. A new solution is needed to securely store and manage these digital credentials, which is where a digital wallet comes into play.
The evolution of identity verification has brought about a significant shift in how we approach establishing trust online. With the introduction of verifiable credentials and digital identification, individuals can now securely store and manage their records in a digital wallet. Gone are the days when simply presenting a government-issued ID or providing basic personal information for digital identification would suffice in preventing identity theft. With the rise of decentralized identity verification, verifiable credentials have become essential in ensuring secure and trustworthy online interactions. With the rise of sophisticated fraud techniques and the interconnectedness of networks through the Internet of Things (IoT), organizations and individuals alike face heightened risks in remote identity verification and digital identification. It is crucial to implement decentralized identity verification methods and ensure the security of personal information stored in a digital wallet.
Join us as we delve into the world of machine learning, artificial intelligence (AI), and advanced biometric technologies that are shaping the future of digital identification and wallet.
Historical Identity Verification
Traditional Methods
Traditional methods of identity verification relied on physical documents, face-to-face interactions, and the use of a wallet. Individuals were required to present identification documents such as passports, driver’s licenses, birth certificates, or wallet to prove their identity. These methods of wallet-based decentralized identity verification were time-consuming and prone to human error, especially in the context of remote identity verification. For instance, a simple mistake in recording personal information during decentralized identity verification could lead to incorrect identification. Similarly, during remote identity verification, a small error in capturing personal details can also result in inaccurate identification.
Moreover, traditional methods lacked the scalability needed for the digital era, especially in the context of decentralized identity verification and remote identity verification. As technology advanced and more transactions moved online, the need for remote identity verification became apparent. The traditional approach of centralized identity verification was not equipped to handle the growing volume of online transactions efficiently. With the rise of decentralized identity verification, this problem is being addressed.
Birth of Digital Identity
The rise of the internet gave birth to the concept of digital identity. Digital identity refers to the online representation of an individual’s personal information. Decentralized identity verification encompasses various aspects such as name, date of birth, address, and even biometric data like fingerprints or facial recognition patterns.
Digital identity opened up new possibilities for remote identity verification. Instead of physically presenting identification documents, individuals could now verify their decentralized identity verification through secure online platforms using their digital identities. This shift allowed for faster and more convenient verification processes while reducing the risk of fraud.
Centralized Trust
Centralized trust models became the norm for identity verification in the digital age. These models relied on a central authority, such as credit bureaus or government agencies, to verify and store individuals’ information securely. When a person applied for a service requiring identity verification, the service provider would request access to this centralized database.
While centralized trust models provided a convenient solution for verifying identities at scale, they also faced challenges in terms of security and privacy. A single point of failure could compromise sensitive personal information stored within these central databases. Concerns arose regarding data breaches and unauthorized access by malicious actors.
To address these issues and enhance security and privacy in identity verification processes further, new approaches have emerged that emphasize user control over their own identities—known as sovereign identity solutions. These solutions leverage decentralized technologies such as blockchain to allow individuals to maintain control over their personal information and selectively share it with service providers as needed.
Digital Identification Evolution
From Identity 1.0 to Credit Bureaus
Identity verification has come a long way, evolving from traditional document-based processes to the introduction of credit bureaus. In the early stages, known as Identity 1.0, identity verification relied heavily on manual verifications and physical documents like passports or driver’s licenses. However, this approach had its limitations.
Document-based processes were susceptible to fraud and required significant manual intervention. Verifying identities solely based on physical documents was time-consuming and not scalable for the growing digital economy. Fortunately, the evolution of identity verification led to the emergence of credit bureaus.
The introduction of credit bureaus revolutionized identity verification by utilizing financial data as a measure of trustworthiness. These bureaus became a crucial component in assessing individuals’ creditworthiness and providing a more comprehensive view of their financial history. Instead of relying solely on physical documents, credit bureaus leveraged financial data from various sources to establish an individual’s credibility.
Credit bureaus collect information about an individual’s loans, debts, payment history, and other relevant financial details. This data is then used to generate credit reports that help lenders determine whether someone is likely to repay borrowed funds. By analyzing these reports, lenders can make informed decisions regarding loan approvals or denials.
The use of credit bureaus significantly streamlined the process of identity verification by automating much of the assessment previously done manually. This automation allowed for faster and more efficient evaluations while minimizing the risk of human error.
Document-Based Processes
Document-based processes formed the foundation of early identity verification methods. Individuals would present physical documents such as passports or driver’s licenses as proof of their identity during various transactions or interactions with organizations.
However, relying solely on these documents had its drawbacks. For instance, it was relatively easy for individuals with malicious intent to forge or manipulate physical documents—making it difficult for organizations to verify authenticity accurately.
Moreover, document-based processes required significant manual intervention. Organizations had to allocate resources to manually verify each document presented, leading to increased costs and longer processing times. This approach was not scalable in the digital age, where speed and efficiency are paramount.
The shift towards digital identification aimed to address these limitations. Digital identities leverage secure digital certificates that encapsulate an individual’s identity information. These certificates can be stored and accessed electronically, providing a more efficient and secure method of identity verification.
Digital identification methods enable organizations to authenticate individuals remotely without the need for physical documents. By leveraging advanced encryption techniques and secure platforms, organizations can establish trust in a person’s identity while minimizing the risk of fraud.
Biometric and Database Techniques
Advanced Liveness Detection
Advanced liveness detection technologies have emerged as a powerful tool in the evolution of identity verification. These technologies address the growing concern of impersonation and fraud attempts by ensuring that the person being verified is physically present during the process. By utilizing facial recognition and biometrics, advanced liveness detection enhances the security and accuracy of identity verification.
In today’s digital landscape, where remote transactions are becoming increasingly common, it is crucial to have robust measures in place to verify an individual’s identity. Advanced liveness detection techniques provide an extra layer of security by verifying that the individual undergoing verification is not just a photograph or video but a live person. This technology can detect various signs of life, such as eye movement, blinking, or even asking the user to perform specific actions like smiling or turning their head.
By incorporating advanced liveness detection into identity verification processes, organizations can significantly reduce the risk of fraudulent activities. This technology ensures that only legitimate individuals gain access to sensitive information or perform critical operations. Whether it’s opening a bank account, accessing online services, or conducting financial transactions remotely, advanced liveness detection plays a vital role in safeguarding against impersonation and fraud attempts.
Biometric Verification
Biometric verification has become increasingly prevalent across various industries due to its high level of accuracy and security. This technique utilizes unique physical or behavioral characteristics like fingerprints or voice patterns to verify an individual’s identity. Unlike traditional methods such as passwords or PINs that can be easily compromised or forgotten, biometrics offer a more reliable and convenient way to authenticate individuals.
One significant advantage of biometric verification is its ability to provide a highly accurate identification process. Each person possesses distinct biometric traits that are difficult to replicate or forge, making it challenging for impostors to deceive this system. For example, fingerprint recognition systems analyze intricate details within fingerprints that are virtually impossible for someone else to reproduce accurately.
Moreover, biometric verification offers a seamless user experience. Instead of remembering complex passwords or carrying physical identification cards, individuals can simply use their unique biometric traits for authentication purposes. This not only simplifies the verification process but also eliminates the need for additional credentials that can be lost or stolen.
The adoption of biometric verification has been widespread across various industries, including banking, healthcare, travel, and government sectors. For instance, banks are increasingly implementing fingerprint or facial recognition systems to enhance security while providing customers with a frictionless banking experience. Similarly, airports have started using biometrics to expedite passenger processing by allowing travelers to verify their identity through facial recognition technology.
Decentralized Identity Verification
Role of Blockchain
Blockchain technology has emerged as a game-changer in the field of identity verification. By offering decentralized and tamper-proof storage of identity information, blockchain ensures that personal data remains secure and immutable. Unlike traditional centralized systems where data is stored in a single location, blockchain distributes the information across multiple nodes, making it highly resistant to hacking or unauthorized access.
One of the key advantages of using blockchain for identity verification is that it gives individuals control over their own data. With verifiable credentials stored on the blockchain, individuals can choose which information to share with different parties without compromising their privacy. This level of control empowers users and eliminates the need for intermediaries such as identity verification providers.
While still in its early stages, the role of blockchain in identity verification shows great potential. As more organizations and governments explore its capabilities, we can expect to see innovative solutions that leverage blockchain’s security and transparency features to revolutionize how identities are verified.
Digital Wallets Integration
Digital wallets have become an integral part of our daily lives, allowing us to store payment cards, loyalty cards, and even concert tickets on our smartphones. But they also offer a convenient solution for integrating various forms of identification into a single platform.
By incorporating driver’s licenses, passports, or other official documents into digital wallets, individuals can streamline the identity verification process. Instead of presenting physical copies or uploading scanned documents each time they need to prove their identity, users can simply share their verified information from their digital wallet securely.
The integration of digital wallets not only simplifies user experience but also enhances efficiency. For example, when applying for a loan or opening a bank account online, users can quickly provide all necessary identification details with just a few taps on their smartphone screen. This reduces friction in transactions and speeds up processes that would otherwise require manual document verification.
As more industries embrace digital transformation and move towards online services, the integration of digital wallets will play a crucial role in ensuring smooth and secure identity verification processes.
Remote Identity Verification Rise
Document Liveness Solutions
Document liveness solutions have emerged as a crucial component in the evolution of identity verification. These innovative solutions utilize advanced technologies to detect forged or tampered documents, ensuring the authenticity and integrity of the verification process.
By leveraging features like holograms or watermarks, document liveness solutions verify the legitimacy of identification documents. This significantly reduces the risk of fraudulent identities being used for malicious purposes. With these robust measures in place, organizations can confidently authenticate individuals remotely without compromising security.
For instance, let’s consider a scenario where an individual is applying for a loan online. The lender requires proof of identity and asks the applicant to upload their government-issued ID. Through document liveness solutions, the lender can ensure that the uploaded document is genuine and has not been manipulated in any way. This helps prevent identity theft and protects both parties involved in the transaction.
PKI Technology Role
Public Key Infrastructure (PKI) technology plays a pivotal role in remote identity verification by enabling secure communication and authentication. PKI ensures that sensitive data exchanged during the verification process remains encrypted and digitally signed, safeguarding it from unauthorized access or tampering.
The use of PKI technology enhances both the integrity and confidentiality of identity information. By employing asymmetric encryption techniques, PKI enables secure transmission of data between parties involved in remote identity verification processes.
Consider an example where an individual needs to verify their identity for accessing their online banking account. The bank utilizes PKI technology to encrypt sensitive user information such as passwords or personal identification numbers (PINs) during transmission over untrusted networks like the internet. This ensures that even if intercepted by malicious actors, the data remains unreadable and protected.
Moreover, PKI technology also facilitates digital signatures during remote identity verification. Digital signatures provide non-repudiation, verifying that a specific message or document originated from a particular sender and has not been altered since its creation. This adds an extra layer of trust and authenticity to the verification process.
Impact of IoT on Verification Trust
Enhancing Security
Identity verification processes have come a long way in the evolution of technology. With the rise of the Internet of Things (IoT), the need for robust security measures has become even more critical. As more devices and systems become interconnected, it becomes easier for hackers to exploit vulnerabilities and gain unauthorized access to personal information.
To combat these threats, identity verification methods have evolved to incorporate multi-factor authentication. This means that instead of relying solely on passwords, users are required to provide additional proof of their identity. One example is the use of one-time passwords (OTPs) sent to a user’s registered mobile device. By requiring this extra step, it adds an additional layer of protection against unauthorized access.
Furthermore, security questions have also become a common feature in identity verification processes. These questions are designed to be personal and unique to each individual, making it harder for hackers or fraudsters to bypass them. For instance, a security question might ask about your first pet’s name or your favorite childhood vacation spot.
Continuous advancements are being made in identity verification technology to stay ahead of emerging threats. Companies invest heavily in research and development to ensure that their systems can withstand sophisticated attacks from cybercriminals. By constantly updating and improving their security protocols, they can enhance trust in their verification processes.
Data Privacy Concerns
While the evolution of identity verification brings many benefits, it also raises concerns about data privacy and protection. As more personal information is collected and stored by organizations, individuals worry about how their data is being used and whether it is adequately protected.
Striking a balance between convenience and privacy is crucial when designing identity verification systems. On one hand, users want a seamless experience that does not require excessive steps or sharing unnecessary personal information. On the other hand, they want assurance that their data will not be misused or compromised.
To address these concerns, regulations like the General Data Protection Regulation (GDPR) have been implemented. GDPR aims to protect individuals’ rights by setting strict guidelines for the collection, storage, and processing of personal data. Organizations must ensure that they obtain proper consent from individuals before collecting their information and provide transparency on how it will be used.
Organizations must implement strong security measures to safeguard personal data from unauthorized access or breaches. This includes encryption techniques, secure storage systems, and regular audits to identify and address vulnerabilities.
Data Privacy and Ownership Emphasis
Control and Ownership Issues
The evolution of identity verification has brought to light concerns about control and ownership of personal data. Traditional identity verification systems are often centralized, meaning that individuals have limited control over their own data. This centralized nature raises questions about who owns the data and who has access to it.
However, decentralized solutions like self-sovereign identity offer a promising alternative. Self-sovereign identity aims to give individuals full control over their personal data by allowing them to manage and share their information securely. With self-sovereign identity, users can choose which entities have access to their data, ensuring greater privacy and ownership.
Resolving control and ownership issues is crucial for building trust in identity verification systems. When individuals have control over their own data, they feel more empowered and confident in sharing their information with service providers. It also reduces the risk of unauthorized access or misuse of personal data.
Equal Access and Empowerment
One of the key benefits of the evolution of identity verification is its potential to provide equal access to services for all individuals. Digital identities can empower marginalized populations by enabling them to participate in the digital economy. For example, individuals without traditional forms of identification, such as refugees or those living in remote areas, can now establish a digital identity that grants them access to financial services, healthcare, education, and more.
Ensuring inclusivity and accessibility should be a priority when designing identity verification systems. By considering the needs of diverse populations during development, we can create solutions that cater to everyone’s unique circumstances. This may involve providing alternative methods for verifying identities or accommodating different levels of digital literacy.
Moreover, digital identities can also facilitate financial inclusion by enabling individuals without a formal banking history to access financial services like loans or insurance products based on their verified digital profiles. This empowers individuals economically by giving them opportunities they might otherwise not have had.
Future Trends in Identity Verification
Predictive Analytics
Identity verification processes are evolving rapidly, and one of the key trends shaping this evolution is the integration of predictive analytics. By harnessing the power of data analysis and machine learning algorithms, businesses can assess risk more accurately and detect fraudulent activities with greater efficiency.
Predictive analytics involves analyzing patterns and historical data to identify suspicious behaviors or anomalies that may indicate potential fraud. This proactive approach enables organizations to prevent unauthorized access and protect sensitive information. For example, by examining a user’s previous login behavior, such as IP addresses or device types, companies can determine whether there is a deviation from their usual patterns. If any irregularities are detected, additional security measures can be implemented to verify the user’s identity.
The use of predictive analytics in identity verification enhances accuracy by reducing false positives and false negatives. It allows businesses to make informed decisions based on data-driven insights rather than relying solely on traditional methods like document verification or personal interviews. Moreover, it significantly improves operational efficiency by automating repetitive tasks and streamlining the overall verification process.
Regulatory Landscape
As technology advances and new risks emerge, regulatory frameworks around identity verification are constantly evolving to address these challenges effectively. One such regulation gaining prominence is Know Your Customer (KYC), which requires businesses to verify the identities of their customers before providing services or conducting transactions.
Compliance with regulations like KYC is crucial for industries that require strong identity verification measures, such as financial institutions, healthcare providers, or online marketplaces. These regulations aim to mitigate risks associated with money laundering, terrorist financing, fraud, and other illicit activities by ensuring that individuals’ identities are properly verified.
To comply with these regulations effectively, organizations must implement robust identity verification solutions that meet stringent requirements while also providing a seamless user experience. This includes verifying various aspects of an individual’s identity using reliable sources like government-issued documents or biometric data.
In addition to KYC, other regulations and standards like the General Data Protection Regulation (GDPR) and Payment Card Industry Data Security Standard (PCI DSS) also impact identity verification practices. These regulations emphasize the importance of protecting personal data, ensuring transparency in data processing, and implementing appropriate security measures.
Conclusion
And there you have it, the evolution of identity verification laid out before you. From the early days of physical identification to the rise of digital techniques and biometrics, we have witnessed a remarkable transformation in how we establish and verify our identities. The advent of decentralized systems and remote verification methods has further revolutionized this space, paving the way for more secure and convenient processes. As we move forward, it is crucial to prioritize data privacy and ownership, ensuring that individuals have control over their personal information.
But this journey is far from over. The future holds exciting possibilities for identity verification, with emerging technologies like blockchain and artificial intelligence poised to play significant roles. As individuals, businesses, and governments, we must stay informed and adapt to these advancements to ensure the continued trustworthiness and reliability of our identification systems. So, keep exploring, keep innovating, and keep pushing the boundaries of what’s possible in the realm of identity verification.
Frequently Asked Questions
FAQ
What is the importance of identity verification?
Identity verification is crucial for various reasons. It helps prevent fraud, protect sensitive information, and ensure trust in online transactions. By verifying someone’s identity, businesses can authenticate users, comply with regulations, and maintain a secure environment.
How has identity verification evolved over time?
Identity verification has come a long way from traditional methods like paper documents to digital solutions. The evolution includes advancements in biometric technologies, decentralized systems, remote verification processes, and the integration of IoT devices—all aimed at enhancing security and convenience.
What are the biometric and database techniques used in digital identification and identity verification? These techniques involve the use of verifiable credentials, digital certificates, and behavioral analytics.
Biometric techniques involve using unique physical or behavioral characteristics such as fingerprints or facial recognition to verify an individual’s identity. Database techniques employ cross-referencing personal data against trusted sources to validate identities more accurately.
How does decentralized identity verification work?
Decentralized identity verification shifts control from centralized authorities to individuals themselves. It utilizes blockchain technology to securely store and manage personal data without relying on a central authority. This empowers users with ownership of their own information while maintaining privacy and security.
How does IoT impact identity verification trust?
The Internet of Things (IoT) plays a significant role in enhancing trust during the identity verification process. By integrating IoT devices like smartphones or wearables into the authentication process, it adds an extra layer of assurance by leveraging device-specific data for validation purposes.
Who owns the data in identity verification processes?
Data privacy and ownership are paramount in modern identity verification practices. Users should have control over their personal information and be aware of how it is being used. Organizations should prioritize transparency, consent-based data sharing, and adhere to relevant privacy regulations to ensure user trust.
What can we expect in the future of identity verification with verifiable credentials, digital identification, biometric authentication, and digital certificates?
The future holds exciting possibilities for identity verification. Advancements like AI-powered biometrics, blockchain-based solutions, machine learning algorithms for fraud detection, and seamless user experiences are expected. The focus will be on strengthening security while providing frictionless verification processes.