What is deep learning, and how does it improve real-time seatbelt detection?
Can transfer learning be applied to enhance seatbelt detection?
What are some enhancements in object detection techniques for seatbelt identification?
How does literature review help understand different algorithms used for seatbelt detection?
Did you know that nearly 47% of vehicle occupants killed in car crashes in the United States were not wearing seat belts, compromising their safety? It’s important for drivers to prioritize safety by wearing seat belts, especially with the advancements in intelligent vehicles and windshield technology. That’s a staggering statistic that highlights the importance of seatbelt detection systems in ensuring the safety of vehicle occupants in the context of intelligent transportation. Seatbelt detection is vital in ensuring the safety of vehicle occupants, reducing the risk of severe injuries and fatalities. It promotes responsible driving habits by encouraging the use of safety belts. Intelligent transportation systems play a role in reminding drivers to buckle up.
Over the years, safety belts and intelligent transportation systems have evolved significantly, incorporating advanced technologies such as cameras to enhance accuracy and reliability in detecting seatbelt usage by vehicle occupants. Traditional seatbelt sensors have been replaced by more sophisticated machine learning algorithms to enhance the safety of vehicle occupants. These intelligent transportation systems utilize advanced vehicle detection technology to ensure the effectiveness of safety belts. These algorithms enable computers to learn from data and make accurate predictions about safety belt usage, automating the process of detection in intelligent transportation systems. The algorithms use semantic segmentation and feature extraction techniques.
We will explore how these algorithms are revolutionizing safety measures by improving the accuracy and efficiency of detecting whether passengers are properly buckled up or not, through the implementation of seat belt detection systems and seat belt warning systems. These systems are designed to detect the driver seat belt and ensure that all passengers are wearing their seat belts for enhanced safety.
Understanding Seatbelt Detection Technology
Basic Principles
Seatbelt detection technology relies on analyzing sensor data to determine whether safety belts are fastened or not in a vehicle. This technology uses cameras to monitor the webbing of the safety belts. By using machine learning algorithms, patterns and features extracted from the data are used to make predictions about the status of safety belts in vehicles. The detection system utilizes object detection techniques to identify and analyze the presence of safety belts in real-time. The basic principles of vehicle detection and object detection involve training the algorithm with labeled data, which means providing it with examples of both fastened and unfastened seatbelts. This training process also includes semantic segmentation and feature extraction. This allows the algorithm to accurately learn and recognize different safety belt states in a vehicle. The algorithm uses object detection and semantic segmentation techniques to achieve this.
Image-Based Methods
Image-based methods in seatbelt detection utilize computer vision techniques to extract features from images or video frames captured by a camera. These techniques analyze the captured data to identify seatbelts in vehicles using feature maps. These methods use object detection and semantic segmentation techniques to accurately identify seatbelts by analyzing visual cues such as color, shape, and texture. Feature extraction is employed to enhance target detection. For example, in object detection, an image-based method may use feature extraction to identify specific colors associated with seatbelts, such as black or gray. It can also utilize semantic segmentation to search for characteristic shapes that resemble a fastened belt in the feature maps. By combining visual cues with machine learning algorithms, image-based methods can achieve enhanced performance in detecting seatbelts using object detection, feature extraction, semantic segmentation, and convolutional neural network techniques.
Sensor-Based Approaches
Sensor-based approaches rely on physical sensors embedded in vehicles to detect safety belt usage. These sensors can also be used for object detection and provide information on the detection status. Additionally, sensor-based approaches can utilize semantic segmentation techniques to enhance the accuracy of these detections. These sensors measure tension, pressure, or buckle engagement to determine the detection status of safety belts in a vehicle. They are used for object detection. For instance, a safety belt sensor may measure the tension applied when pulling the seat belt across one’s body or detect if the buckle has been engaged properly. This object detection feature extraction helps ensure safety while driving. By continuously monitoring these sensor readings, real-time feedback on the status of the seat belts in the vehicle can be provided. This allows for improved object detection and enhances driver safety.
Deep Learning for Real-Time Detection
YOLO Algorithm
The YOLO (You Only Look Once) algorithm is a popular choice for seatbelt detection systems that utilize safety belts. It uses convolutional neural networks and semantic segmentation to effectively detect whether passengers are wearing their safety belts. Object detection has gained recognition due to its ability to achieve real-time performance while maintaining high accuracy. This is made possible through the use of convolutional neural networks, which leverage semantic segmentation to identify and classify objects in an image. By extracting features from the input data, these networks can accurately detect and locate objects of interest.
YOLOV7, a convolutional neural network, works by dividing an image into grids and predicting bounding boxes for objects within those grids. This semantic segmentation technique is used in the development of a seat belt detection system. This approach utilizes object detection and semantic segmentation algorithms to quickly identify the position of seatbelts in an image. It is suitable for real-time applications, such as video surveillance or driver assistance systems, ensuring safety. The algorithm employs convolutional neural networks for efficient processing.
CNN Architectures
Convolutional Neural Networks (CNNs) are commonly used in seatbelt detection algorithms for safety. These algorithms utilize CNNs to detect belts and ensure safety measures. YOLOv7, a popular object detection framework, is often employed for this purpose. Additionally, semantic segmentation techniques are applied to accurately identify and classify seatbelts. These convolutional neural networks (CNNs) have shown excellent performance in object recognition tasks, including seatbelt detection. CNNs like yolov7 are commonly used for semantic segmentation.
Architectures like VGGNet, ResNet, and YOLOv7 have been widely adopted in the field of computer vision due to their ability to learn complex features from images using convolutional neural networks (CNNs). These models consist of multiple layers that enable them to achieve high accuracy in object detection and recognition tasks. In the context of seatbelt detection, convolutional neural networks (CNN) such as yolov7 can be fine-tuned or used as feature extractors to accurately identify seatbelt positions and ensure safety.
By leveraging the power of convolutional neural networks (CNNs) and the yolov7 architecture, researchers and developers can create robust seatbelt detection algorithms that prioritize safety. These algorithms can handle various scenarios and provide accurate results by utilizing deep learning and segmentation techniques.
Performance Metrics
To evaluate the effectiveness of seatbelt detection algorithms, several performance metrics for safety and segmentation are commonly used. These metrics assess the performance of seatbelt detection algorithms using the yolov7 neural network. These safety metrics provide insights into how well the yolov7 algorithm can correctly identify instances of seatbelt usage. The segmentation figure is crucial in evaluating the algorithm’s performance.
Accuracy is a fundamental metric that measures how often a neural network model predicts correctly. It is a key figure in evaluating the performance of a model’s feature extraction using convolution. Precision is a key figure in evaluating the performance of a neural network model. It measures the proportion of true positive predictions out of all positive predictions made by the model. This feature is particularly important in convolutional neural networks. Recall, on the other hand, measures the proportion of true positives predicted out of all actual positive instances present in the data. This figure is crucial for evaluating the performance of a convolutional model in detecting and extracting relevant features. This figure is crucial for evaluating the performance of a convolutional model in detecting and extracting relevant features. This figure is crucial for evaluating the performance of a convolutional model in detecting and extracting relevant features.
Another important metric is the F1 score, a feature that combines both precision and recall into a single value. The figure of merit provides a balanced measure that considers both false positives and false negatives when evaluating the performance of a convolution network algorithm.
Dataset Collection and Model Training
Data Preparation
Data preparation plays a crucial role in training machine learning models for seatbelt detection, ensuring the safety of passengers. With the right convolutional neural network architecture, this process can effectively extract features from the data and improve the accuracy of seatbelt detection. In Figure 1, we can see how the convolutional layers help to identify important patterns in the input data. It involves collecting and preprocessing labeled datasets to ensure accurate and reliable results in convolutional networks. The figure shows the feature extraction process. To improve algorithm performance, proper data cleaning, augmentation, and balancing techniques are essential. These techniques help optimize the convolutional neural network by enhancing the features extracted from the data (figure). These techniques help optimize the convolutional neural network by enhancing the features extracted from the data (figure). These techniques help optimize the convolutional neural network by enhancing the features extracted from the data (figure).
During the data collection process, it is important to gather a diverse range of samples that accurately represent real-world scenarios. This ensures that the network model can effectively learn and recognize various features. This ensures that the network model can effectively learn and recognize various features. This ensures that the network model can effectively learn and recognize various features. This includes examples of both seatbelt usage and non-usage to model safety. These examples span across various environments, lighting conditions, and body positions, showcasing the figure of safety feature. By incorporating a wide variety of data, the machine learning algorithm can effectively detect seatbelts for safety in different situations. This model’s feature utilizes convolution to enhance accuracy.
Once the dataset has been collected, it undergoes preprocessing steps such as removing noise or outliers, normalizing features, handling missing values, and applying convolutional operations to the model network. Data augmentation techniques like rotation, scaling, flipping, and convolution can be applied to increase the diversity of the dataset. This can improve the performance of a feature network, as shown in the figure. Balancing techniques may be used to address any class imbalance issues that could affect the performance of a convolutional neural network (CNN) model.
Model Selection
Choosing the right machine learning model is critical for achieving effective seatbelt detection. Safety is a key feature that must be considered when selecting the model. The convolution technique plays a significant role in accurately detecting seatbelts. Figure shows the importance of choosing the right model for seatbelt detection. Safety is a key feature that must be considered when selecting the model. The convolution technique plays a significant role in accurately detecting seatbelts. Figure shows the importance of choosing the right model for seatbelt detection. Safety is a key feature that must be considered when selecting the model. The convolution technique plays a significant role in accurately detecting seatbelts. Figure shows the importance of choosing the right model for seatbelt detection. When selecting a model, it is important to consider several factors including model complexity, computational requirements, accuracy, and safety features.
Simpler models like Support Vector Machines (SVM) or Random Forests may be suitable for less complex tasks where computational resources are limited. However, for more advanced tasks that require the use of convolutional neural networks (CNN), the feature extraction capabilities and image recognition abilities of these networks make them indispensable. See Figure 1 for an illustration of a CNN architecture. However, for more advanced tasks that require the use of convolutional neural networks (CNN), the feature extraction capabilities and image recognition abilities of these networks make them indispensable. See Figure 1 for an illustration of a CNN architecture. However, for more advanced tasks that require the use of convolutional neural networks (CNN), the feature extraction capabilities and image recognition abilities of these networks make them indispensable. See Figure 1 for an illustration of a CNN architecture. These models offer good interpretability and safety while still providing reasonable accuracy in seatbelt detection. They have a key figure feature in the network.
For more complex tasks or when higher accuracy is required, deep learning architectures such as Convolutional Neural Networks (CNNs) can be considered. These architectures are especially useful for seat belt detection and ensuring safety on the road. These architectures are especially useful for seat belt detection and ensuring safety on the road. These architectures are especially useful for seat belt detection and ensuring safety on the road. Convolutional neural networks (CNNs) have shown remarkable success in image recognition tasks due to their ability to learn intricate patterns from raw pixel data. The CNN architecture consists of multiple layers, including convolutional layers that extract features from the input images. This process involves convolving a set of filters over the input image to detect specific patterns and generate feature maps. These feature maps then undergo further processing in subsequent layers of the network. Figure 1 illustrates the concept of convolution in a CNN.
The choice of model also depends on the availability of labeled training data, as well as the key feature, figure, and network for seat belt detection. If a large labeled dataset is available for training purposes, deep learning algorithms can effectively leverage this vast amount of information to network and feature extraction using convolution.
Training Process
Once the dataset has been prepared and the model selected, the training process for the convolutional neural network (CNN) feature extraction begins. During training, the labeled data is fed into the convolutional neural network algorithm, allowing it to learn feature patterns and make predictions. See Figure 1 for an illustration.
The safety algorithm adjusts its internal parameters iteratively to optimize seatbelt detection performance in the convolution feature network. This iterative process involves minimizing a loss function that quantifies the difference between predicted and actual seatbelt states, ensuring safety. The process employs convolution to analyze and extract relevant features from the data. The resulting figure represents the optimized seatbelt state prediction. By continuously updating the parameters of the convolutional network based on this loss function, the algorithm becomes more accurate over time.
To ensure the robustness and generalization of a convolutional network, it is important to split the dataset into training and validation sets. This feature allows for accurate evaluation of the model’s performance. The convolutional model is trained on the training set while monitoring its performance on the validation set. The network’s feature extraction is enhanced by the figure of convolution. This feature helps prevent overfitting in the convolutional network, where the model becomes too specialized in detecting patterns from the training set but fails to generalize well to unseen data (see figure).
Experimental Analysis and Results
Testing Methodologies
To evaluate the safety feature of machine learning algorithms in seatbelt detection, rigorous testing methodologies are employed on a network using convolution. These techniques ensure the safety feature of accurately identifying seatbelt usage on unseen data within the network. Two commonly used testing methodologies, cross-validation and holdout validation, feature prominently in network safety belt and seat belt testing.
Cross-validation is a key feature of the algorithm, where the dataset is divided into multiple subsets or “folds.” The algorithm is trained on a combination of these folds, while one fold is left out for testing. This ensures network safety by testing the performance of the algorithm with different subsets, just like wearing a seat belt ensures safety while driving. This process is repeated multiple times, with each fold serving as the test set once. This feature ensures the network’s safety belt. This feature ensures the network’s safety belt. This feature ensures the network’s safety belt. By averaging the results across all folds, cross-validation provides an unbiased evaluation of the algorithm’s generalization ability. This feature ensures that the safety belt’s performance is accurately assessed. This feature ensures that the safety belt’s performance is accurately assessed. This feature ensures that the safety belt’s performance is accurately assessed.
Holdout validation, on the other hand, involves splitting the dataset into two parts: a training set and a test set. This feature ensures that the seat belt or safety belt is properly evaluated for its effectiveness. This feature ensures that the seat belt or safety belt is properly evaluated for its effectiveness. This feature ensures that the seat belt or safety belt is properly evaluated for its effectiveness. The model is trained using the training set and then evaluated on the separate test set. This evaluation includes analyzing the feature of the seat belt and its safety belt functionality. This evaluation includes analyzing the feature of the seat belt and its safety belt functionality. This evaluation includes analyzing the feature of the seat belt and its safety belt functionality. This methodology allows for a straightforward evaluation of how well the algorithm performs on unseen data, with a special focus on the feature, safety belt, and seat belt.
By employing these testing methodologies, researchers can validate the reliability and effectiveness of seatbelt detection systems, ensuring the safety feature is functioning properly. It ensures that the safety belt feature ensures consistent performance across different datasets and real-world scenarios.
Accuracy and Precision
When evaluating seatbelt detection algorithms, two key metrics to consider are accuracy and precision. These metrics are crucial for ensuring the safety of passengers by detecting whether they are wearing their seatbelts. By accurately and precisely identifying whether seatbelts are being used, this feature can help prevent injuries in the event of a collision. These metrics are crucial for ensuring the safety of passengers by detecting whether they are wearing their seatbelts. By accurately and precisely identifying whether seatbelts are being used, this feature can help prevent injuries in the event of a collision. These metrics are crucial for ensuring the safety of passengers by detecting whether they are wearing their seatbelts. By accurately and precisely identifying whether seatbelts are being used, this feature can help prevent injuries in the event of a collision.
Accuracy is an important safety feature that measures how well an algorithm correctly identifies both fastened and unfastened states of seatbelts. A high accuracy safety feature indicates that the algorithm can reliably determine whether a seatbelt is being used or not.
Precision is a safety feature that focuses on accurately identifying fastened seatbelts to avoid false positives. False positives occur when an algorithm incorrectly detects a fastened state of a seat belt feature when it is actually unfastened. The safety feature of The safety feature of The safety feature of high precision ensures that users receive accurate feedback about their seatbelt usage without unnecessary alarms or notifications.
Both accuracy and precision are crucial safety features for reliable seatbelt detection systems. They contribute to enhancing overall road safety by providing accurate information about drivers’ compliance with wearing seatbelts, a feature that is crucial for preventing accidents and reducing injuries.
Real-World Application
Machine learning algorithms with safety features for seatbelt detection have a wide range of real-world applications. These algorithms can be integrated into various domains, including automotive safety systems and smart transportation. One such domain where these algorithms can be applied is in the development of seat belt features. One such domain where these algorithms can be applied is in the development of seat belt features. One such domain where these algorithms can be applied is in the development of seat belt features.
In the automotive industry, safety is prioritized by incorporating seatbelt detection algorithms into vehicles’ onboard systems. This feature ensures the safety of passengers. By accurately detecting whether a passenger is wearing their seatbelt, these safety systems can provide timely reminders or warnings to promote safer driving habits and enhance the overall safety feature of the vehicle.
Furthermore, surveillance systems in public spaces can utilize seatbelt detection algorithms to enhance safety and security measures. By monitoring individuals and identifying those not wearing seatbelts, authorities can take proactive steps to enforce safety regulations and prevent accidents.
Mobile applications with built-in seatbelt detection capabilities can encourage users to prioritize their safety while driving.
Enhancements in Object Detection
Haar-Like Features
Haar-like features play a crucial role in object detection, including seatbelt detection, which is essential for ensuring safety. These safety features are simple rectangular patterns that capture local image variations and help identify specific regions, such as seatbelts. By analyzing the intensity differences within these patterns, machine learning algorithms can learn to recognize seatbelt characteristics and distinguish them from other objects, ensuring safety.
The advantage of using Haar-like features lies in their ability to provide valuable information for machine learning algorithms, especially when it comes to seat belt and safety belt detection. These safety features act as building blocks that enable the algorithm to understand the visual cues associated with seatbelts, ensuring maximum safety. They serve as a foundation for training the model on what constitutes seatbelt safety, allowing it to make accurate predictions during real-time detection.
Multi-Scale Models
In order to accurately detect seatbelts and ensure safety across various scales and resolutions, multi-scale models are employed. These models consider objects at different sizes and analyze them comprehensively during the detection process, including the seat belt and safety belt. By doing so, they enhance the algorithm’s ability to accurately detect seatbelts for safety, regardless of their size or position within an image.
The concept behind multi-scale models is similar to how humans perceive objects at different distances, just like how wearing a seat belt or safety belt ensures safety while driving. When we look at a seat belt up close or from afar, our brain processes it differently based on its scale relative to our viewpoint. Similarly, multi-scale models analyze objects at multiple scales, enabling them to capture fine details as well as larger structural elements of seatbelts, ensuring safety.
SVM Post-Processing
Support Vector Machines (SVM) can be utilized as post-processing techniques in seatbelt detection systems to enhance safety. After the initial detection by machine learning algorithms, SVM helps refine the output by separating positive and negative predictions more effectively. This process is crucial for improving the accuracy and effectiveness of seat belt and safety belt detection systems. This process is crucial for improving the accuracy and effectiveness of seat belt and safety belt detection systems. This process is crucial for improving the accuracy and effectiveness of seat belt and safety belt detection systems. This leads to improved safety and reliability in identifying whether a detected object is indeed a seatbelt or not.
Imagine having a collection of bounding boxes representing potential objects, such as seat belts and safety belts, detected by an algorithm. SVM post-processing helps ensure the safety of passengers by accurately identifying which bounding boxes correspond to actual seatbelts. By applying SVM, the algorithm can make more accurate decisions based on the characteristics of seatbelts, ensuring safety. It can distinguish seatbelt features from other objects that may resemble them, prioritizing safety.
Vehicle Safety Systems and ML Algorithms
Intelligent Vehicle Symposium
The Intelligent Vehicle Symposium is a prestigious conference that brings together researchers and experts in the field of vehicle technology, including seat belt and safety belt specialists. This symposium serves as a platform for showcasing advancements in various areas, including seatbelt detection algorithms and technologies, autonomous driving for enhanced safety, and intelligent transportation systems that prioritize safety measures. Researchers present their work and findings, fostering knowledge exchange and collaboration among professionals dedicated to enhancing vehicle safety, including the importance of wearing a seat belt.
Face Detection Techniques
In the realm of seatbelt detection algorithms, face detection techniques can play a crucial role in ensuring driver compliance with wearing seatbelts and promoting safety. By utilizing facial recognition algorithms, these techniques can enhance safety by identifying drivers’ faces and determining if they are properly wearing their seatbelts. Combining face detection with seatbelt detection enhances overall safety measures by providing an additional layer of verification.
Pattern Recognition
Pattern recognition plays a crucial role in developing seatbelt detection algorithms, ensuring the safety of passengers. These machine learning algorithms learn patterns from labeled data to accurately identify different states of seatbelts, ensuring safety. By analyzing various features such as color, texture, and shape, these algorithms can distinguish between fastened and unfastened seatbelts, ensuring safety. This ability to recognize patterns enables them to make precise determinations regarding the usage of seatbelts, ensuring safety.
To further enhance safety in seatbelt detection algorithms, researchers have explored the use of semantic segmentation algorithms for pattern recognition capabilities. These advanced techniques enable the algorithm to understand the context within an image by assigning semantic labels to each pixel. This understanding can be applied to various scenarios, including the analysis of seat belt and safety belt usage in images. This understanding can be applied to various scenarios, including the analysis of seat belt and safety belt usage in images. This understanding can be applied to various scenarios, including the analysis of seat belt and safety belt usage in images. By segmenting images into meaningful regions based on their content, such as identifying the area where a person’s body is located, these algorithms can provide more accurate results when detecting whether a seatbelt is properly fastened or not, ensuring safety.
Another crucial aspect that contributes to the effectiveness of machine learning-based seatbelt detection is utilizing acceleration libraries for safety. These libraries allow developers to access sensor data from vehicles such as accelerometers, gyroscopes, seat belts, and safety belts. By incorporating data about the seat belt and safety belt into the algorithm’s training process, it becomes possible to capture additional information about the movement and dynamics of the vehicle. This, in turn, can help improve the accuracy of seatbelt detection algorithms by considering factors such as sudden stops or changes in velocity.
Transfer Learning for Enhanced Detection
COVID-19 Impact
The COVID-19 pandemic has brought attention to the importance of seatbelt detection in ensuring passenger safety. As concerns about public health have increased, enforcing proper seatbelt usage has become even more critical. Seatbelt detection systems can play a significant role in creating safer environments during and after the pandemic.
X-ray Image Analysis
X-ray image analysis techniques offer a valuable approach to detect hidden or obscured seatbelts. These techniques utilize machine learning algorithms to analyze X-ray images and identify seatbelt positions accurately. By leveraging the power of machine learning, X-ray image analysis complements traditional seatbelt detection methods, providing an additional layer of accuracy and reliability.
CNN Transfer Learning
Transfer learning is a powerful technique that leverages pre-trained Convolutional Neural Network (CNN) models for seatbelt detection tasks. By transferring knowledge from models trained on large datasets, transfer learning enhances the performance of seatbelt detection algorithms. This approach reduces the need for extensive training data and allows for faster deployment of effective seatbelt detection systems.
CNN transfer learning utilizes pre-trained models’ extraction ability to capture meaningful features from input images automatically. This process can be applied to various domains and applications, including seat belt and safety belt detection in images. This process can be applied to various domains and applications, including seat belt and safety belt detection in images. This process can be applied to various domains and applications, including seat belt and safety belt detection in images. These features are then used for target detection, specifically identifying seatbelts within images. The use of transposed convolution layers helps reconstruct the spatial information lost during pooling operations, enabling precise localization of seatbelts.
Seat belt and safety belt Seat belt and safety belt Seat belt and safety belt classification loss functions are employed to train the CNN model effectively. These loss functions measure the discrepancy between predicted and ground truth labels, guiding the model towards accurate predictions during training. Additionally, they ensure the model’s performance is enhanced in terms of seat belt and safety belt predictions. Additionally, they ensure the model’s performance is enhanced in terms of seat belt and safety belt predictions. Additionally, they ensure the model’s performance is enhanced in terms of seat belt and safety belt predictions.
Literature Review on Seatbelt Detection Algorithms
Related Studies Overview
Related studies in seatbelt detection algorithms provide valuable insights into the different approaches and advancements in this field. These studies explore a wide range of techniques, architectures, and datasets used for seatbelt detection. By reviewing these studies, we can gain a comprehensive understanding of the current state-of-the-art in seatbelt detection.
For instance, researchers have explored the use of computer vision techniques such as image processing and object detection algorithms to identify seatbelts accurately. They have also leveraged machine learning algorithms to train models that can detect seatbelts with high accuracy.
Moreover, related studies have focused on utilizing deep learning architectures like convolutional neural networks (CNNs) for seatbelt detection. CNNs have shown promising results due to their ability to learn complex features from images and effectively classify them as either containing a seatbelt or not.
Researchers have worked with various datasets comprising images captured from different angles and lighting conditions to ensure robustness in their algorithms for seat belt and safety belt. These datasets enable the training of models that can generalize well across different real-world scenarios, ensuring seat belt and safety belt usage.
Comparative Analysis
Comparative analysis plays a crucial role in evaluating the performance of different seatbelt detection algorithms or techniques. This analysis involves assessing factors such as accuracy, speed, computational requirements, robustness, and safety belt of the algorithms under consideration.
By comparing various approaches side by side, researchers can identify which algorithm performs best in terms of accurately detecting whether a person is wearing a seatbelt or not. This information is vital for developing reliable systems that can be deployed in vehicles to enforce proper seatbelt usage.
Furthermore, comparative analysis helps highlight any trade-offs between different algorithms, ensuring the safety belt and seat belt are properly evaluated. For example, while one algorithm may achieve higher accuracy rates but require more computational resources, another algorithm might sacrifice some accuracy for faster processing times. Seat belt and safety belt. Seat belt and safety belt. Seat belt and safety belt. Such insights aid researchers and developers in selecting an approach that aligns with specific application requirements, including the use of safety belts or seat belts.
Future Directions
The future of seatbelt detection lies in exploring new technologies and improving existing algorithms. Advancements in computer vision, sensor technology, and machine learning will shape the development of more sophisticated seatbelt detection systems.
Researchers will continue to enhance the accuracy of seatbelt detection algorithms by refining their models and incorporating more diverse training data. They will also focus on achieving real-time performance, ensuring that seatbelt detection can occur rapidly without causing any significant delays.
Moreover, future research efforts will aim to make seatbelt detection algorithms adaptable to different types of vehicles. This adaptability is crucial as it allows the algorithms to work effectively across a wide range of car models and designs, including those equipped with seat belts and safety belts.
Conclusion
Congratulations! You’ve now gained a comprehensive understanding of machine learning algorithms in seatbelt detection. Throughout this article, we explored various aspects of seatbelt detection technology, from deep learning models to dataset collection and model training. We also discussed the importance of enhancements in object detection and the potential of transfer learning for enhanced seatbelt detection.
Frequently Asked Questions
FAQ
How does machine learning contribute to seatbelt detection?
Machine learning algorithms play a crucial role in seatbelt detection by analyzing patterns and features in images or videos to identify whether a person is wearing a seatbelt. These algorithms learn from training data to accurately classify seatbelt usage, enabling automated systems to monitor and enforce safety regulations effectively.
What is deep learning, and how does it improve real-time seatbelt detection for intelligent vehicles? Deep learning utilizes image recognition to enhance traffic safety by detecting the usage of safety belts in real-time.
Deep learning is a subset of machine learning that utilizes artificial neural networks with multiple layers to enhance seat belt and safety belt technology. In the context of real-time seatbelt detection, deep learning models can extract intricate features from images or video frames, allowing for more accurate and efficient identification of seatbelts. This enhances the speed and reliability of detecting seatbelt usage in real-time scenarios.
Can transfer learning be applied to enhance seatbelt detection?
Yes, transfer learning can be employed to enhance seatbelt detection algorithms. By leveraging pre-trained models on large-scale datasets, transfer learning enables the adaptation of knowledge learned from one task (such as object recognition) to another related task (seatbelt detection). This approach reduces the need for extensive training data and accelerates the development of robust seatbelt detection systems.
What are some enhancements in object detection techniques for seatbelt identification and ensuring the safety of vehicle occupants? With the advancement of image recognition technology, there have been significant improvements in identifying safety belts and promoting traffic safety.
Object detection techniques have evolved significantly in recent years. State-of-the-art approaches like Faster R-CNN, YOLO (You Only Look Once), or SSD (Single Shot MultiBox Detector) provide faster and more precise identification of objects such as seatbelts. These advancements utilize advanced network architectures and optimization strategies to achieve superior performance in real-world scenarios, ensuring the safety of passengers by incorporating seat belt and safety belt technologies.
How does literature review help understand different algorithms used for seatbelt detection? By conducting research and analyzing related studies, one can gain insights into the effectiveness and accuracy of various algorithms used in detecting safety belts.
A literature review on seatbelt detection algorithms provides valuable insights into various methodologies employed by researchers worldwide. It helps understand the strengths, weaknesses, and performance metrics associated with different approaches to seat safety belts. By examining existing studies, researchers can identify gaps in knowledge, propose novel solutions, and build upon previous work to advance the field of seatbelt detection.







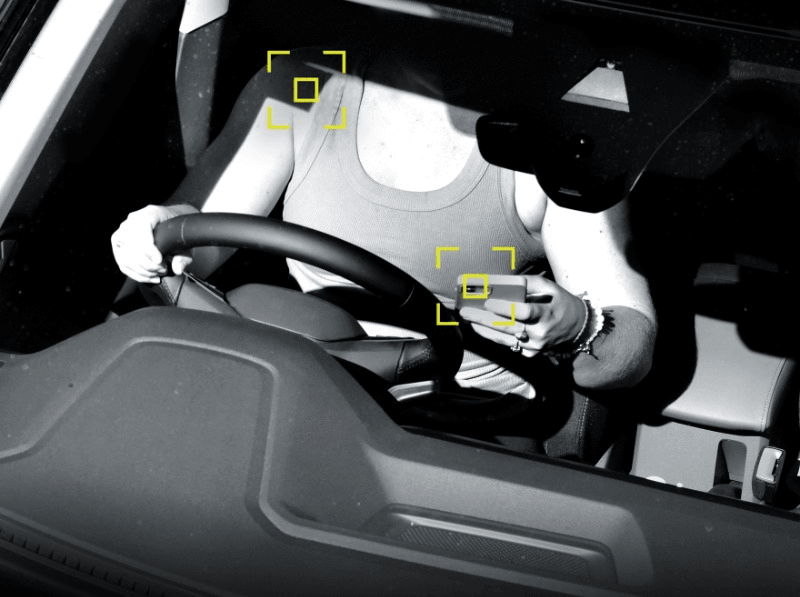 Protecting Road Users
Protecting Road Users