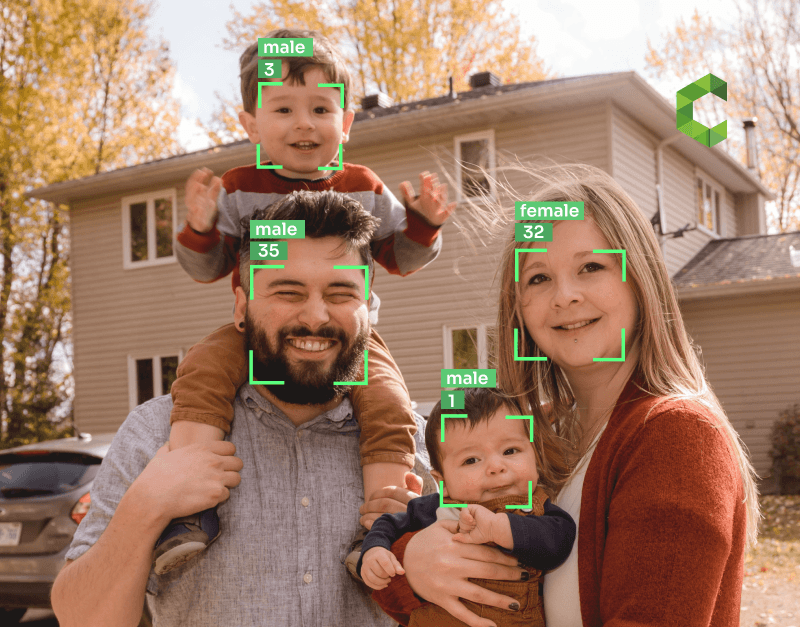
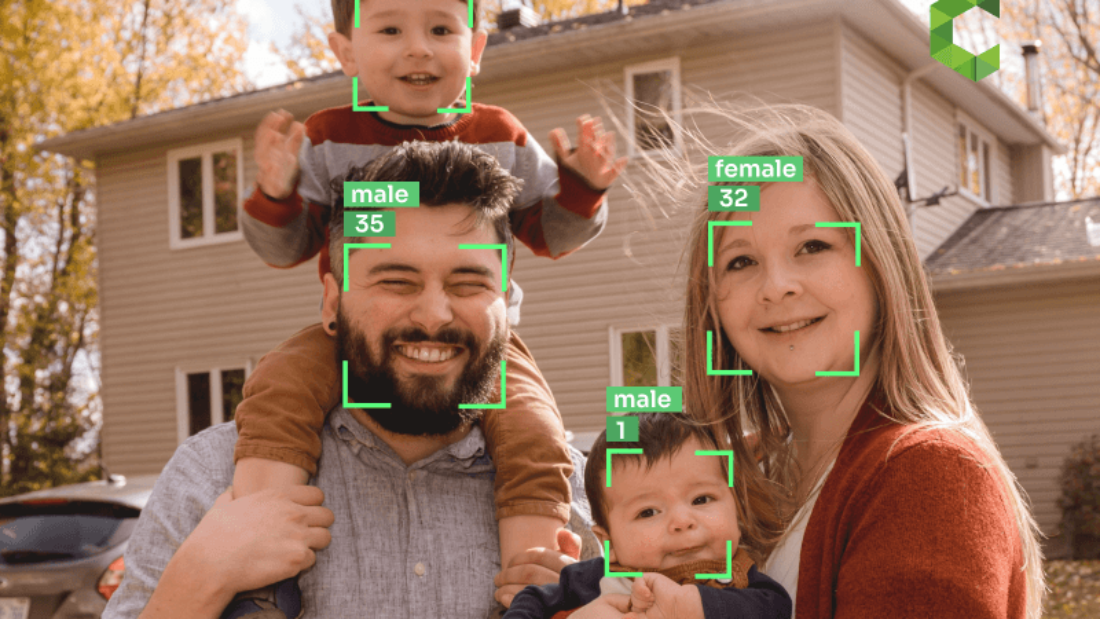
Did you know that targeted marketing through computer vision and machine learning is reshaping the way companies use facial recognition advertising on digital signage to target consumers? In today’s fast-paced world, targeted advertising is key to successful marketing campaigns. Understanding your audience and their preferences allows you to effectively promote your product through digital signage. By reaching the right people at the right time, you can maximize the impact of your marketing efforts. With facial recognition technology (FRT), targeted marketing and advertising can now analyze and target individuals based on their age, gender, location, and even emotional responses. This is made possible through machine learning while prioritizing user privacy. This level of personalization takes marketing to a whole new level for businesses. It allows businesses to tailor their product offerings to individual shoppers, creating a more personalized shopping experience. By using targeted ads spaces, businesses can reach shoppers with relevant content that is tailored specifically to their interests and preferences. This level of personalization is a game-changer for businesses looking to connect with their target audience in a more meaningful way.
Imagine walking into a coffee shop and being greeted by a digital display that uses facial recognition technology to recognize your face. This facial recognition app then displays personalized offers tailored just for you, thanks to advanced facial recognition software and systems. Or browsing a targeted marketing online store where the website adapts its content based on your demographic information, preferences, and mobile product using image recognition technology. Facial recognition software enables real-time image detection for mobile advertising, capturing data to deliver targeted messages that resonate with each individual user.
So buckle up as we dive into the fascinating world of targeted marketing using facial recognition image detection on mobile devices.
Understanding Facial Recognition Advertising
Technology Explained
Facial recognition technology has revolutionized the way we interact with digital advertising, especially in the context of image detection on mobile devices. This innovative technology utilizes complex algorithms for face recognition and image detection, allowing for a deeper understanding of consumer behavior. With its mobile capabilities, it can analyze facial features efficiently. By detecting emotions and characteristics in images, facial recognition technology can provide valuable insights into individual preferences, demographics, and age. This technology is particularly useful for mobile applications.
The process behind facial recognition is fascinating. It works by comparing unique facial patterns captured in real-time with a database of known faces using image recognition and detection technology on mobile devices. The algorithm then analyzes these patterns for face recognition, image recognition, facial detection, and facial recognition app to determine various attributes about the person being scanned. This cutting-edge image recognition technology, including face recognition and facial detection, has come a long way in recent years, making it faster and more accurate than ever before.
Significance in Marketing
Facial recognition advertising, with its ability to analyze and identify individuals based on their unique facial features, holds immense significance in the world of marketing. This technology allows marketers to target specific demographics and deliver personalized content, resulting in more effective and efficient advertising campaigns. By leveraging the power of image recognition, businesses can tailor their messaging and offerings to resonate with their target audience, ultimately driving higher engagement and conversion rates. In a digitally-driven era where visual content dominates, the integration of facial recognition technology in advertising strategies is becoming increasingly essential for brands to stay competitive and relevant By leveraging face recognition, image recognition, and facial detection technology, marketers can deliver highly targeted ads that resonate with consumers on a personal level. With access to real-time data on emotions and reactions, advertisers can create personalized experiences that capture attention and drive engagement using face recognition, image recognition, and facial detection.
This advanced technology, including image recognition and facial detection, also enables marketers to gain a deeper understanding of consumer behavior. By analyzing facial expressions during ad interactions, companies can use image recognition to gauge the effectiveness of their campaigns and make data-driven decisions for future strategies. This level of insight, using facial detection, allows brands to refine their messaging and tailor their offerings to meet specific customer needs.
Targeted Product Promotions
One of the key advantages of facial recognition advertising is its ability to facilitate precise targeting of specific products or services. Marketers can use this technology to tailor ads based on individual preferences and demographics, ensuring that each advertisement is relevant and appealing to the viewer.
Imagine walking past a digital billboard that instantly recognizes your age group and gender through facial recognition technology. In an instant, you’re presented with an ad showcasing a product perfectly suited to your interests or needs. This level of personalization not only enhances user experience but also increases the likelihood of conversion.
The Mechanics of Facial Recognition in Marketing
Emotion Detection
Facial recognition technology has the remarkable ability to accurately detect and analyze emotions. By analyzing facial expressions, marketers can gain valuable insights into how consumers are feeling when they interact with their advertisements. This information allows marketers to create emotionally resonant ads that connect with their target audience on a deeper level.
Emotional engagement is crucial in marketing because it leads to stronger brand connections and increased customer loyalty. When an ad elicits a positive emotional response from viewers, they are more likely to remember the brand and develop a favorable attitude towards it. For example, if a facial recognition system detects that someone is smiling while viewing an ad, the marketer can infer that the content resonates positively with them. Armed with this knowledge, marketers can tailor future campaigns to evoke similar emotions and build stronger relationships with their customers.
Traffic Evaluation
One of the significant benefits of facial recognition advertising is its ability to provide valuable insights into foot traffic patterns. Marketers can use facial recognition systems installed in stores or public spaces to measure the effectiveness of their campaigns in real-time. By tracking how many people engage with specific ads and for how long, marketers gain a better understanding of which strategies are most successful.
This data helps optimize marketing strategies for better results. For instance, if a particular advertisement receives minimal attention from passersby, marketers can make adjustments or replace it entirely with something more compelling. By observing foot traffic patterns throughout different times of the day or week, businesses can determine peak hours or popular areas within their establishments. This information allows them to allocate resources effectively and improve overall customer experience.
Interactive Marketing
Facial recognition technology opens up exciting possibilities for interactive marketing experiences. With this technology, consumers can engage with ads using gestures or even facial expressions. Imagine walking past a digital billboard that prompts you to smile or raise your eyebrows, triggering an interactive experience tailored specifically for you.
Interactive marketing increases engagement and captures attention in a crowded advertising landscape. By providing consumers with an opportunity to actively participate in the ad, brands can create memorable experiences that leave a lasting impression. This not only enhances brand recall but also encourages social sharing and word-of-mouth promotion. When consumers have a positive interactive experience with an advertisement, they are more likely to share it with their friends and family, amplifying its reach and impact.
Benefits for Businesses
Enhanced Customer Experience
Facial recognition advertising offers businesses the opportunity to enhance the customer experience by creating personalized interactions. This technology allows companies to tailor content based on individual preferences and interests, ensuring that customers receive relevant and engaging advertisements.
By analyzing facial features and expressions, facial recognition technology can identify a person’s age, gender, and even mood. This data enables marketers to deliver targeted ads that resonate with each customer on a personal level. For example, if a customer is browsing for skincare products, facial recognition technology can detect their interest and display ads specifically related to skincare.
This personalized approach not only captures the attention of customers but also increases their satisfaction with the brand. When individuals feel that a company understands their needs and desires, they are more likely to develop a sense of loyalty towards that brand. By leveraging facial recognition advertising, businesses can strengthen their relationships with customers and foster long-term loyalty.
Improved Conversion Rates
One of the significant advantages of facial recognition advertising is its ability to boost conversion rates. By delivering targeted ads based on individual preferences, this technology ensures that businesses reach the right audience at the right time with relevant messages.
Traditional advertising methods often involve casting a wide net in hopes of capturing some interested consumers. However, this approach may result in wasted resources as many people who see these ads are not part of the target audience. Facial recognition advertising eliminates this inefficiency by tailoring content specifically to individuals who have shown an interest in similar products or services.
When customers are presented with personalized content that aligns with their interests or needs, they are more likely to take action. Whether it’s making a purchase or signing up for a newsletter, personalized advertisements drive engagement and ultimately lead to increased sales.
Real-time Analytics
Facial recognition technology provides businesses with valuable real-time analytics on consumer behavior. Marketers can track various metrics such as engagement levels, emotions evoked by specific advertisements, and even the amount of time customers spend interacting with an ad.
This wealth of information allows businesses to make immediate adjustments and optimize their advertising campaigns. For example, if a particular ad is not generating the desired response or engagement, marketers can quickly identify this through real-time analytics and modify the content accordingly.
Real-time analytics enable businesses to measure the effectiveness of their marketing efforts in real-time. They can monitor which ads are performing well and which ones may need improvement. This data-driven approach allows for continuous optimization, ensuring that businesses are always delivering the most impactful content to their target audience.
Real-World Applications and Case Studies
Retail Innovations
Facial recognition advertising is revolutionizing the retail industry by driving innovation and transforming the way consumers shop. With this technology, retailers can offer personalized shopping experiences like never before. Imagine walking into a store, and the digital signage recognizes your face, displaying customized recommendations based on your preferences. This level of personalization enhances the overall shopping experience and increases customer satisfaction.
Moreover, facial recognition technology enables virtual try-ons, allowing customers to virtually test products such as clothing or makeup without physically trying them on. This not only saves time but also provides a convenient and hygienic alternative for shoppers. By leveraging facial recognition advertising, retailers can tap into new opportunities for engaging with their customers and boosting sales.
Emotional Analytics
One of the most valuable aspects of facial recognition technology in advertising is its ability to capture emotional analytics data. Marketers can now gain insights into how consumers feel about their products or advertisements by analyzing their facial expressions. This information helps refine marketing strategies to evoke desired emotions in consumers and create more impactful campaigns.
For example, let’s say a company launches a new ad campaign for a luxury fragrance. By utilizing facial recognition technology, marketers can analyze the emotional responses of viewers when they see the ad. If the majority of viewers show positive emotions like happiness or excitement, it indicates that the campaign is resonating well with the target audience. On the other hand, if negative emotions are detected, marketers can make necessary adjustments to improve the effectiveness of their ads.
B2B Marketing Strategies
Facial recognition advertising is not limited to consumer-facing industries; it also has significant applications in B2B marketing strategies. Businesses can utilize this technology to personalize content for their clients and decision-makers, enhancing their overall experience with tailored messaging.
For instance, imagine an executive attending a trade show where various vendors showcase their products or services. With facial recognition technology integrated into interactive displays, the executive’s face can be recognized, and personalized content can be displayed based on their previous interactions or preferences. This level of customization strengthens relationships between businesses and their clients, making them feel valued and understood.
Furthermore, facial recognition advertising in B2B marketing strategies can help drive sales by providing relevant product information to potential buyers. By analyzing the facial expressions of decision-makers during presentations or meetings, marketers can gauge their interest levels and adjust their pitches accordingly. This targeted approach increases the chances of closing deals and building long-term partnerships.
Ethical Considerations and Challenges
Privacy Concerns
Facial recognition advertising has sparked privacy concerns among consumers. The collection and storage of facial data raise questions about the protection of personal information. Consumers worry about how their data will be used, who will have access to it, and whether it will be sold to third parties without their consent.
To address these concerns, marketers must prioritize transparency and consent. They should clearly communicate to consumers how facial data will be collected, stored, and used for advertising purposes. This includes providing information on the specific types of data that will be collected, the duration of storage, and any measures taken to secure the data.
By being transparent about their practices, marketers can build trust with consumers and alleviate privacy concerns. This transparency also allows consumers to make informed decisions about whether or not they want to participate in facial recognition advertising campaigns.
Consent and Transparency
Obtaining consent is a critical aspect of using facial recognition advertising ethically. Marketers must ensure that individuals are aware that their faces are being scanned and analyzed for targeted advertising purposes. Consent should be obtained explicitly, ensuring that individuals understand the implications of participating in such campaigns.
Furthermore, marketers need to clearly communicate how facial data will be protected. This includes explaining the security measures in place to prevent unauthorized access or misuse of the data. By assuring consumers that their personal information is safeguarded, marketers can foster trust and encourage more individuals to engage with facial recognition advertising.
Transparency goes hand in hand with obtaining consent. Marketers should provide clear explanations regarding why they are collecting facial data and how it will benefit both the consumer and the advertiser. By demonstrating a commitment to openness and honesty, marketers can strengthen consumer confidence in this emerging technology.
Regulation Compliance
Compliance with relevant regulations is paramount when using facial recognition technology for advertising purposes. Marketers must familiarize themselves with applicable laws governing data protection and privacy rights in order to ensure ethical practices.
Data protection laws and privacy regulations vary across different jurisdictions. Marketers must be diligent in understanding the specific requirements and restrictions imposed by these laws. This includes obtaining explicit consent, implementing appropriate security measures, and adhering to data retention guidelines.
The Future of Advertising with Facial Recognition
Personalization Trends
Facial recognition advertising is at the forefront of the growing trend of personalization in marketing. In today’s digital age, consumers have come to expect tailored experiences that cater to their unique needs. By leveraging facial recognition technology, marketers can deliver highly personalized advertisements that resonate with individual consumers.
Personalization enhances customer satisfaction by providing relevant content and recommendations. When consumers feel understood and valued, they are more likely to engage with brands and make purchases. Facial recognition advertising allows marketers to analyze a person’s facial features, expressions, and demographics to customize their ad experience accordingly. For example, a beauty brand could use facial recognition technology to identify a consumer’s skin type and recommend suitable skincare products.
Technological Advancements
Continuous advancements in facial recognition technology have significantly improved its accuracy and capabilities. New algorithms and machine learning techniques are constantly being developed to enhance performance over time. These technological advancements enable marketers to leverage facial recognition in more effective ways for their advertising campaigns.
Facial recognition software utilizes computer vision algorithms to identify and analyze unique facial features such as eyes, nose, mouth, and overall face shape. This enables marketers to target specific demographics or individuals based on their appearance or emotions expressed through their faces. For instance, an advertisement for a new sports car could be shown exclusively to individuals who exhibit excitement or enthusiasm when viewing similar products.
Predictive Analytics
One of the key advantages of facial recognition advertising is its ability to enable predictive analytics based on consumer behavior. By analyzing patterns in facial expressions and reactions, marketers can anticipate customer needs and preferences before they are even consciously aware of them.
Predictive analytics helps optimize marketing strategies by allowing advertisers to tailor their campaigns for maximum impact. For example, if a fast-food chain notices that customers tend to show signs of hunger during certain times of the day or week through facial analysis, they can strategically schedule targeted ads during those periods to increase the likelihood of attracting hungry customers.
Emotion Recognition and Customer Insights
Identifying Mind States
Facial recognition technology has the remarkable ability to identify different mind states, such as attention or interest. By analyzing facial expressions and micro-expressions, marketers can gain valuable insights into consumers’ emotional responses to advertisements. This information allows them to deliver relevant messages at the right time, increasing the chances of capturing the audience’s attention and engagement.
Imagine a scenario where you’re watching a video advertisement on your favorite social media platform. As you watch, the facial recognition technology embedded in the platform detects that you’re deeply engaged with the content. In response, it delivers a personalized message tailored specifically to your interests and preferences. This level of understanding mind states not only improves ad targeting but also enhances overall engagement.
Enhancing Engagement
Facial recognition advertising goes beyond traditional methods by delivering personalized content that captures attention and creates a connection with consumers. When an advertisement is customized based on individual characteristics identified through facial recognition technology, it becomes more relatable and resonates with viewers on a deeper level.
Consider this: You’re walking past a digital billboard displaying an advertisement for your favorite brand of sneakers. Suddenly, the billboard recognizes your face through its facial recognition capabilities and displays an exclusive offer just for you. The personalized nature of this interaction instantly grabs your attention and sparks a sense of excitement within you. Enhanced engagement like this not only increases brand recall but also fosters customer loyalty.
Tailoring Messages
One of the most powerful aspects of facial recognition technology in advertising is its ability to tailor messages based on individual characteristics. By analyzing features such as age, gender, or even emotions expressed through facial expressions, marketers can customize ads to resonate with specific demographics or evoke desired emotional responses.
Let’s say you’re browsing an online store for skincare products. The website utilizes facial recognition technology to analyze your age range and skin concerns based on uploaded selfies or webcam footage. With this information, the website can then present you with personalized product recommendations and targeted advertisements that address your specific needs. Tailored messages like these increase the relevance and effectiveness of advertising campaigns, ultimately driving higher conversion rates.
Bridging the Gap Between Digital and Physical
Interactive Experiences
Facial recognition advertising has revolutionized the way consumers interact with advertisements. With this technology, users can now engage in interactive experiences that go beyond passive viewing. By utilizing gestures, expressions, or voice commands, individuals can actively participate in the ad content.
Imagine walking past a digital billboard and having it respond to your presence. Facial recognition technology enables ads to recognize your facial features and tailor the content specifically for you. This level of personalization creates a memorable brand interaction that captures attention and leaves a lasting impression.
For example, an ad for a clothing store could use facial recognition to analyze your age and gender, then display outfits that are most likely to appeal to you. By allowing users to virtually try on different outfits through augmented reality, this interactive experience not only engages customers but also helps them visualize themselves wearing the clothing.
Omnichannel Marketing
In today’s interconnected world, marketers strive to deliver consistent messaging across multiple channels. Facial recognition technology plays a vital role in achieving this goal by supporting omnichannel marketing strategies.
With visual data captured through facial recognition, marketers can gather valuable insights about their target audience’s preferences and behaviors. This information allows them to create personalized campaigns that resonate with consumers across various touchpoints.
For instance, if a customer interacts with an advertisement using facial recognition at a brick-and-mortar store, their preferences can be seamlessly integrated into their online shopping experience. By utilizing proximity sensors within physical stores, marketers can trigger personalized recommendations or exclusive offers when customers enter specific areas of the store.
By leveraging facial recognition technology throughout various channels – from social media platforms to physical retail spaces – marketers can provide a seamless experience for customers throughout their entire journey with the brand.
Customer Journey Mapping
Understanding each stage of the customer journey is crucial for optimizing marketing efforts. Facial recognition advertising provides valuable insights into touchpoints and interactions along this journey.
By analyzing visual data captured through facial recognition, marketers can gain a deeper understanding of how consumers engage with their brand at different stages. This knowledge helps them identify pain points, areas of improvement, and opportunities for delivering targeted messaging.
For example, by tracking customer reactions to specific ads or products using facial recognition technology, marketers can determine which messages are most effective in driving engagement. They can then tailor their marketing strategies to align with these findings and optimize the impact of their campaigns.
Innovations in Targeted Marketing Strategies
Dynamic Content Delivery
Facial recognition technology has revolutionized targeted marketing strategies by enabling dynamic content delivery in real-time. With this technology, advertisements can be adjusted based on consumer reactions or preferences, creating a more personalized and engaging experience.
By analyzing facial expressions and emotions, advertisers can tailor their ads to match the viewer’s mood and level of interest. For example, if a person appears happy or excited, the ad can feature upbeat content that resonates with their positive emotions. On the other hand, if someone seems bored or disinterested, the ad can quickly adapt to capture their attention with more captivating visuals or compelling messaging.
This dynamic content delivery not only increases relevancy but also enhances engagement. When consumers see ads that align with their current state of mind, they are more likely to pay attention and respond positively. As a result, brands can deliver more impactful messages and improve overall campaign performance.
Audience Segmentation
Facial recognition advertising allows for precise audience segmentation, enabling marketers to target specific demographics, interests, or emotions effectively. By analyzing facial features and expressions captured by cameras or sensors, advertisers can identify key characteristics of individuals within a given audience.
For instance, if an advertisement aims to target young adults interested in fitness and wellness products, facial recognition technology can help identify individuals who exhibit signs of an active lifestyle or health-consciousness. This information allows marketers to tailor their messaging specifically for this audience segment.
Audience segmentation not only improves campaign effectiveness but also enhances return on investment (ROI). By delivering highly relevant ads to specific target groups, brands can maximize their marketing budget by focusing on those most likely to convert into customers. This level of precision targeting reduces wasted impressions on audiences who may have little interest in the product or service being advertised.
Campaign Optimization
Another significant innovation facilitated by facial recognition technology is continuous campaign optimization. Marketers now have access to real-time data and insights that can be used to make data-driven decisions and improve campaign performance.
By analyzing consumer reactions captured through facial recognition, marketers can identify which ads are resonating with their target audience and which ones may need adjustments. This real-time feedback allows for quick optimization of campaigns, ensuring that the right message is delivered to the right people at the right time.
Continuous campaign optimization leads to better performance and higher returns on investment. Marketers can refine their strategies based on actual consumer responses rather than relying solely on assumptions or post-campaign analysis. As a result, they can allocate resources more effectively, optimize ad placements, and adjust messaging to maximize results.
Conclusion
Congratulations! You’ve now gained a deeper understanding of facial recognition advertising and its potential impact on the marketing world. From uncovering the mechanics behind this technology to exploring its real-world applications, you’ve seen how businesses can benefit from targeted marketing strategies that bridge the gap between digital and physical realms. However, it’s important to acknowledge the ethical considerations and challenges that come with implementing facial recognition advertising. As we look to the future, innovations in emotion recognition and customer insights hold great promise for enhancing personalized marketing experiences.
Now that you’re armed with this knowledge, it’s time to consider how facial recognition advertising can be integrated into your own marketing strategies. Think about the ways in which it can help you better understand your customers, tailor your messaging, and create more impactful campaigns. Remember, as with any new technology, it’s crucial to prioritize ethical practices and ensure transparency in data collection and usage. By harnessing the power of facial recognition advertising responsibly, you have the opportunity to revolutionize your marketing efforts and stay ahead in an increasingly competitive landscape.
Frequently Asked Questions
Can facial recognition advertising benefit businesses?
Yes, facial recognition advertising can bring numerous benefits to businesses. By leveraging this technology, companies can deliver personalized and targeted advertisements to their customers, leading to increased engagement and conversion rates. It enables businesses to understand customer preferences better, optimize marketing strategies, and enhance overall customer experience.
Are there any ethical considerations and challenges associated with facial recognition advertising?
Indeed, there are ethical considerations and challenges related to facial recognition advertising. Privacy concerns arise as personal data is collected through this technology. Transparency and consent become crucial in ensuring user trust. Potential biases in the algorithms used for facial recognition pose challenges regarding fairness and inclusivity.
How does emotion recognition contribute to customer insights?
Emotion recognition plays a significant role in gathering valuable customer insights. By analyzing facial expressions, advertisers can gauge customers’ emotional responses to ads or products. This information helps them understand which elements of their marketing campaigns are resonating with customers on an emotional level, enabling them to refine their strategies accordingly.
What are some real-world applications of facial recognition advertising?
Facial recognition advertising has found applications across various industries. Retail stores use it to offer personalized product recommendations based on individual preferences. In airports, it facilitates seamless check-ins by matching faces with passport photos. Moreover, digital signage uses this technology for dynamic ad displays that adapt based on the viewer’s demographics or emotions.
How does facial recognition bridge the gap between digital and physical experiences?
Facial recognition bridges the gap between digital and physical experiences by enabling personalized interactions in both realms. For example, it allows retailers to provide customized offers or greetings when a recognized customer enters their store physically or visits their website online. This integration enhances brand consistency and creates a seamless customer journey across channels.