##Introduction
Did you know that 92% of people are dissatisfied with the quality of their own photos due to image processing issues? With the advancement of technology, face recognition has become a crucial aspect of improving the quality of human faces in photographs. Additionally, specific image defect detection has also played a significant role in addressing concerns related to photo quality. Whether it’s capturing face recognition in blurry images, poor lighting conditions, or awkward poses, taking picture-perfect moments of human faces can be challenging. This is especially true when using smartphones with varying shutter angles. But what if there was a way to automatically detect and improve the quality of your photos using image processing? With specific image defect detection techniques, you can enhance the clarity and resolution of your pictures. Additionally, face recognition algorithms can be applied to identify and optimize facial features in your images. Explore these capabilities in our computer vision workshops. That’s where face quality detection comes in.
Face quality detection using computer vision is revolutionizing various applications, from security systems to social media platforms. With the advancement of technology, smartphones equipped with pattern recognition algorithms can now accurately analyze and assess the quality of people’s faces. Face recognition, a crucial aspect of computer vision and face analysis, not only helps accurately identify and verify people but also enhances user experience and privacy. This article discusses how computer vision and pattern recognition are revolutionizing industries like healthcare, retail, and entertainment. These technologies enable personalized services by detecting specific image defects. People can now benefit from these advancements in various sectors.
Get ready to discover how computer vision, AI, and face ID are transforming the way we capture and share our most memorable moments in this article.
Understanding Face Detection
Working Principles
Face quality detection is a process in computer vision that relies on sophisticated algorithms to analyze various facial attributes. This article discusses the participation of these algorithms in the proceedings. These computer algorithms assess factors such as pose, illumination, occlusions, and resolution to determine the overall quality of a face image. This article explores how these attributes are evaluated using IEEE standards. By comparing these attributes against predefined thresholds, the computer system can accurately classify the quality of a face image. This article from IEEE discusses the system’s participation in analyzing face images.
The working principles behind face quality detection involve intricate analysis of different aspects of a face image. This ieee article discusses the attribute and document the intricate analysis involved in face quality detection. For example, the algorithm may assess the alignment of the face’s pose with specific reference points to evaluate image quality. This evaluation follows the guidelines set by IEEE for image quality assessment. It also examines illumination conditions to identify images with poor lighting or excessive shadows in IEEE proceedings documents. Occlusions caused by accessories or partial coverage of the face are considered in the context of ieee to ensure accurate assessment of pp.
To further enhance accuracy, these algorithms take into account the resolution of an image, as specified by the IEEE and measured in pixels per inch (pp). Higher-resolution images tend to provide more details and clearer facial features, leading to better-quality assessments. According to the IEEE, the use of higher-resolution images can significantly improve the quality of assessments. The improved clarity and level of detail in the images can enhance the accuracy and precision of evaluations (pp). By considering all these factors collectively, IEEE face quality detection algorithms can effectively evaluate and categorize face images based on their overall quality. These algorithms utilize pp techniques to accurately assess the quality of face images.
Different Methods
There are multiple methods employed in face quality detection, each utilizing different approaches to evaluate image quality. The IEEE plays a significant role in advancing these methods. Feature-based methods extract specific facial characteristics like symmetry or texture from an image for evaluation purposes. These methods are commonly used in the field of computer vision and image processing, and are often mentioned in IEEE publications and research papers. The extracted features are then analyzed using various algorithms and techniques, such as Principal Component Analysis (PCA) or Local Binary Patterns (LBP), to derive meaningful information about the image. This information can be used for a wide range of applications, including face recognition, emotion detection, and age estimation. Overall, feature-based methods play a crucial role in the analysis and understanding These methods rely on predefined rules and heuristics to determine whether an image meets certain criteria for high-quality results, as defined by the IEEE. These criteria are specified in the IEEE’s guidelines and are used to evaluate the image’s quality, referred to as the PP.
On the other hand, machine learning techniques have gained popularity in recent years due to their ability to automatically assess the quality of face images using large datasets. These techniques have been widely studied and implemented by researchers in the IEEE community, resulting in numerous papers (PP) being published on this topic. These techniques involve training models with vast amounts of data that include both high-quality and low-quality images, using the IEEE and PP standards. The models learn patterns and correlations within this data to make accurate predictions about new images they encounter. This process is guided by the principles of ieee and takes into account the information contained in the pp.
Machine learning-based approaches, including those developed by IEEE, have shown promising results in detecting various issues affecting image quality, such as blurriness caused by motion or poor focus. They can also identify common problems like occlusions resulting from accessories like sunglasses or masks covering parts of the face, which is important for image quality assessment. The method follows the guidelines set by IEEE and is published in the Proceedings of the IEEE (pp). By leveraging the power of machine learning, these techniques provide efficient and reliable face quality detection capabilities for IEEE transactions and conference proceedings (IEEE TPAMI, IEEE CVPR, etc.).
Key Capabilities
Face quality detection algorithms, such as those used in the ieee, possess several key capabilities that enable them to accurately assess image quality and measure pp. One important capability of the IEEE is the ability to identify low-quality images affected by factors such as blurriness or poor lighting conditions. The IEEE uses its expertise in image processing (pp) to accurately detect and flag these issues, ensuring that only high-quality images are used. This ensures that only high-quality images from IEEE are used for further analysis or processing, ensuring the best results. The images are carefully selected and processed to meet the standards set by IEEE, guaranteeing their reliability and accuracy.
These ieee algorithms can detect common issues such as occlusions caused by accessories or partial face coverage. This capability is crucial in scenarios where accurate facial recognition or authentication is required, as it prevents false positives or unauthorized access attempts. The IEEE recognizes the importance of this capability in ensuring reliable and secure identification processes.
Another essential capability of IEEE face quality detection algorithms is their ability to assess the authenticity of a face image and prevent spoofing attacks.
The Evolution of Face Detection Technology
Historical Development
The development of face quality detection, an area of research that has been explored by the IEEE, has a rich history that spans several decades. Early research in the field of facial recognition, as published by IEEE, focused on simple feature extraction techniques. These techniques involved identifying specific facial landmarks such as the eyes, nose, and mouth. These early methods laid the foundation for subsequent advancements in computer vision and machine learning.
As technology progressed, more sophisticated algorithms were developed to improve the accuracy and reliability of face detection systems. One notable milestone was the introduction of Viola-Jones algorithm in 2001, which revolutionized real-time face detection by using Haar-like features and cascading classifiers. This breakthrough paved the way for widespread adoption of face detection technology in various applications.
In recent years, deep learning techniques have emerged as a game-changer in the field of face detection. Convolutional Neural Networks (CNNs) have proven to be highly effective in detecting faces with remarkable accuracy. By leveraging large datasets and powerful computational resources, these deep learning models can learn intricate patterns and features that were previously difficult to capture.
Future Prospects
The future of face quality detection holds great promise as researchers continue to explore ways to enhance its accuracy and efficiency. Ongoing studies are focusing on refining existing algorithms and developing new approaches that can address challenges such as occlusions, variations in lighting conditions, and pose variations.
Advancements in deep learning and artificial intelligence are expected to play a pivotal role in shaping the future of face quality detection. These technologies enable machines to learn from vast amounts of data and make intelligent decisions based on patterns they discover. With continued progress in this area, we can anticipate even higher levels of accuracy and robustness in face detection systems.
As face recognition technology becomes more prevalent across industries like security, retail, healthcare, and entertainment, ensuring reliable identification is crucial. Face quality detection will play an integral role in this process by assessing various factors like image resolution, pose estimation, illumination, and facial expression to determine the quality of a face image. By detecting and filtering out low-quality images, these systems can improve the overall performance and reliability of face recognition algorithms.
Applications and Uses of Face Detection
Everyday Scenarios
Face quality detection technology has become an integral part of our daily lives, finding applications in various scenarios. One common use is unlocking smartphones through facial recognition. By analyzing the unique features of an individual’s face, this technology ensures secure access to personal devices. It provides a convenient and efficient way to authenticate users without the need for passwords or PINs.
Another everyday application of face quality detection is in video conferencing applications. These platforms optimize video quality based on the user’s face image. By detecting facial features, such as expressions and movements, the system can adjust lighting, focus, and resolution to enhance the overall video experience for all participants. This ensures that everyone looks their best during virtual meetings or online gatherings.
Social media platforms also leverage face quality detection to enhance photo uploads. When you upload a picture, these platforms analyze your face and suggest improvements or filters that can enhance the overall appearance of the image. This feature allows users to effortlessly enhance their photos before sharing them with friends and followers.
Industry-Specific Applications
In addition to everyday scenarios, face quality detection technology finds valuable applications in various industries.
In healthcare, accurate patient identification is crucial for providing effective medical care. Face quality detection assists in this process by verifying patients’ identities through facial recognition systems. This ensures that medical records are correctly associated with the right individuals and helps prevent errors in treatment plans or medication administration.
The retail industry utilizes face quality detection technology to deliver personalized customer experiences. By analyzing customers’ facial features, retailers can tailor their advertising efforts to target specific demographics more effectively. For example, if a customer has shown interest in a particular product category before, targeted advertisements related to those products can be delivered based on their facial analysis data. Retailers can use this technology for product recommendations based on customers’ preferences and previous buying patterns.
Entertainment sectors have also embraced face quality detection technology for various applications. Augmented reality (AR) experiences, such as virtual makeup try-ons, rely on accurate face detection to overlay digital elements onto a person’s face in real-time. This allows users to virtually try different makeup looks without physically applying any products. Furthermore, in gaming, face quality detection enables character customization by mapping players’ facial features onto virtual avatars, creating a more immersive and personalized gaming experience.
Face quality detection technology has revolutionized the way we interact with everyday devices and has opened up new possibilities across industries. From unlocking smartphones to enhancing video conferencing experiences, and from improving healthcare identification to delivering personalized retail experiences and entertainment applications – the potential of this technology is vast.
Technical Aspects of Face Detection Systems
Evaluating Image Quality
Algorithms play a crucial role. These algorithms analyze various factors such as sharpness, contrast, and noise levels to determine the overall quality of an image. By examining pixel-level details, they can identify blurriness or artifacts that may affect the reliability of facial analysis.
For instance, face quality detection algorithms assess the level of sharpness in an image. A blurry or out-of-focus image may hinder accurate facial recognition and subsequent analysis. Similarly, these algorithms examine the contrast levels within an image to ensure that facial features are clearly distinguishable. They evaluate noise levels to detect any unwanted distortions that could impact the accuracy of face detection.
By assessing image quality, these algorithms provide valuable insights into whether an image is suitable for further processing or if it requires improvement. This evaluation helps developers optimize their systems by filtering out low-quality images and ensuring reliable results.
Performance Evaluation Algorithms
To ensure the effectiveness and efficiency of face quality detection systems, performance evaluation algorithms are employed. These algorithms compare the output generated by a system against ground truth data to measure key metrics such as precision, recall, and processing time.
Precision refers to the proportion of correctly identified faces out of all detected faces. It provides insights into how accurately the system distinguishes between faces and non-faces. On the other hand, recall measures the system’s ability to identify all relevant faces within a given dataset.
Processing time is another important metric assessed by performance evaluation algorithms. It determines how quickly a system can analyze images and provide results. Developers strive to optimize processing time without compromising accuracy to enhance user experience in real-time applications.
By evaluating system performance using these metrics, developers can fine-tune their algorithms and optimize overall system efficiency.
Input Data Requirements
To achieve accurate results in face detection systems, high-resolution images with sufficient facial details are necessary. These algorithms rely on clear and detailed images to accurately identify and analyze facial features.
Adequate lighting conditions are also crucial for optimal image quality during image capture. Insufficient lighting can result in shadows or uneven illumination, which may affect the accuracy of face detection algorithms.
In video-based applications, a continuous stream of frames is required to assess the quality of facial images over time. This enables real-time monitoring and analysis, making it suitable for applications such as surveillance or emotion recognition systems.
By adhering to these input data requirements, developers can ensure that face detection algorithms perform optimally and provide reliable results.
Face Analysis Technology (FATE) Quality Assessment
Standards and Documentation
To ensure interoperability and consistency in face quality detection systems, various standards and documentation have been established. The International Organization for Standardization (ISO) is one such organization that provides guidelines for image quality assessment and evaluation metrics. These standards serve as a reference point for developers, enabling them to adhere to industry best practices.
By following these standards, developers can ensure that their face analysis technology evaluation systems meet the required criteria for accurate and reliable results. The guidelines outlined by ISO help in evaluating factors such as resolution, noise levels, compression artifacts, color accuracy, and sharpness of facial images. Adhering to these standards ensures that the algorithms used in face quality detection systems deliver consistent performance across different platforms and environments.
Example Results Analysis
Analyzing example results from face quality detection algorithms plays a crucial role in understanding their effectiveness in various scenarios. By examining both successful detections and false positives/negatives, developers gain valuable insights into the strengths and weaknesses of their algorithms.
For instance, let’s consider a scenario where a face quality detection algorithm is applied to images with varying pose variations or occlusions. Through result analysis, developers can identify areas for improvement in handling these challenges effectively. They can refine their algorithms to better handle situations where faces are partially obscured or captured from different angles.
Furthermore, analyzing example results helps determine the confidence score associated with each detection. This score quantifies the algorithm’s level of certainty in its assessment of face quality. Developers can use this information to establish thresholds for accepting or rejecting detected faces based on desired confidence levels.
Example results analysis allows developers to evaluate the robustness of their algorithms against common challenges faced in real-world scenarios. By studying how well an algorithm performs when faced with low-quality images or challenging lighting conditions, they can fine-tune their systems accordingly.
Developing Face Detection Systems
Participating in Development
Developers play a crucial role in advancing face quality detection technology. By actively participating in research communities, conferences, or open-source projects, they can contribute to the growth and innovation of this field. Sharing knowledge, collaborating with experts, and exchanging ideas can drive progress and lead to breakthroughs in face quality detection.
Participating in computer vision workshops and conferences allows developers to stay updated on the latest advancements and techniques in detecting human faces. These events provide valuable opportunities to learn from industry leaders and researchers who are at the forefront of developing face detection models. Through these interactions, developers can gain insights into cutting-edge neural network architectures and algorithms that enhance face quality assessment.
Open-source projects also offer an avenue for developers to contribute their expertise to the development of face quality detection systems. Libraries like OpenCV provide pre-trained models and APIs that simplify integration into projects. Developers can leverage these resources to implement sophisticated algorithms for analyzing facial features accurately.
Collaboration is key. Engaging with like-minded individuals through online forums or research communities fosters a spirit of collaboration where developers can share their experiences, seek advice, and collaborate on innovative solutions. This collective effort helps refine existing models and develop new approaches that improve the accuracy and reliability of detecting face quality.
Available Programs and Resources
For developers interested in implementing face quality detection, there are numerous programs and resources available that facilitate learning and implementation. Online tutorials provide step-by-step guidance on understanding the underlying concepts of face quality assessment algorithms. These tutorials break down complex topics into easily digestible explanations, enabling developers to grasp the fundamentals quickly.
Developer consoles provided by various face quality detection platforms offer comprehensive tools for seamless integration into applications. These consoles often come equipped with APIs, SDKs (Software Development Kits), sample code snippets, detailed documentation, and testing environments. With these resources, developers can efficiently incorporate face quality detection capabilities into their applications, saving time and effort in the development process.
Developer Consoles
Developer consoles provided by face quality detection platforms offer a range of tools and resources to support developers in implementing face quality assessment. These consoles serve as centralized hubs where developers can access APIs, SDKs, sample code, and comprehensive documentation. The availability of these resources simplifies the integration process and enables developers to quickly get started with incorporating face quality detection functionalities into their applications.
In addition to providing essential resources for implementation, developer consoles often include testing environments. These environments allow developers to evaluate the performance of their face quality detection implementations in real-world scenarios.
Data Security in Face Detection Systems
Encryption and Data Protection
Face quality detection systems prioritize encryption and data protection measures to ensure the privacy and security of user information. Robust encryption protocols are implemented to safeguard sensitive data during transmission and storage. This ensures that even if unauthorized individuals gain access to the data, it remains indecipherable and unusable.
Encryption plays a vital role in protecting user information by converting it into an unreadable format that can only be decrypted with the correct key. Advanced encryption algorithms, such as AES (Advanced Encryption Standard), are commonly employed to provide a high level of security. By encrypting the data, face detection systems add an extra layer of protection against potential threats.
In addition to encryption, face quality detection systems comply with data protection regulations, such as GDPR (General Data Protection Regulation). These regulations establish strict guidelines for handling personal data, including facial images or biometric information. Adhering to these regulations is essential not only for maintaining user trust but also for legal compliance.
Handling Sensitive Information
Face quality detection systems must handle sensitive information with utmost care. This includes facial images or biometric data that can potentially reveal unique characteristics of individuals. To minimize the risk of unauthorized access or misuse, secure data handling practices are implemented.
Access controls play a crucial role in ensuring that only authorized personnel have access to sensitive information. By implementing strong authentication mechanisms and restricting access based on roles and responsibilities, face detection systems prevent unauthorized individuals from obtaining sensitive data.
Furthermore, encryption is used not only during transmission but also when storing sensitive information. By encrypting stored data, face detection systems prevent unauthorized access even if physical devices or databases are compromised.
Responsible management of sensitive information also involves adhering to privacy policies and obtaining user consent. Before collecting any personal data through face detection systems, users should be informed about how their information will be used and given the option to provide consent. This transparency helps build trust between users and the system, ensuring that their privacy is respected.
Implementing Face Detection Systems
API Documentation and Usage
API documentation for face quality detection platforms provides detailed instructions on how to integrate the technology into applications. This documentation serves as a comprehensive guide, offering developers valuable insights into the capabilities and functionalities of the API.
By referring to the API documentation, developers can gain a clear understanding of available endpoints, request/response formats, authentication methods, and usage limits. These details enable them to effectively utilize the features provided by the face quality detection system.
For example, let’s say you are developing a mobile application that requires face quality detection for user authentication. By following the API documentation, you can easily integrate the necessary code snippets and implement this functionality seamlessly within your app.
Handling Video and Orientation Data
Face quality detection algorithms are designed to handle video streams by analyzing multiple frames over time. This capability allows for more accurate analysis of facial features and expressions in dynamic scenarios.
Moreover, these algorithms can account for different orientations of faces within an image or video frame. Whether a face is tilted or turned at various angles, the system can still accurately detect and analyze its quality.
Consider a scenario where you are building a surveillance system that needs to monitor individuals in real-time. The face quality detection algorithm can continuously analyze video feeds from multiple cameras and provide insights about the detected faces’ quality irrespective of their orientation or movement.
Next Steps for Implementation
Once developers have understood the fundamentals of face quality detection through API documentation, they can proceed with implementing this technology in their applications.
The first step involves selecting suitable algorithms or APIs based on specific requirements. There are several options available in the market today, each with its own set of advantages and limitations. Developers should carefully evaluate these options before making a decision.
After selecting an appropriate algorithm or API, integration and testing should be conducted iteratively to ensure optimal performance. This iterative approach allows developers to identify any issues early on and make necessary adjustments accordingly.
For instance, during the integration and testing phase, you may discover that certain lighting conditions affect the accuracy of face quality detection. By addressing this issue through adjustments in camera settings or algorithm parameters, you can enhance the overall performance of your application.
Community and Expertise in Face Quality Detection
Connecting with Developers
Engaging with other developers working on face quality detection can provide valuable insights and foster collaboration. In the field of computer vision and machine learning, there are numerous online communities, forums, and social media groups dedicated to this specific topic. These platforms offer opportunities to connect with like-minded individuals who share a passion for advancing face quality detection algorithms.
By joining these communities, developers can share their experiences and discuss challenges they have encountered while working on face quality detection projects. This exchange of knowledge can accelerate learning and development in the field. It allows developers to learn from each other’s successes and failures, gaining practical insights that may not be found in textbooks or academic papers.
For example, a developer might encounter difficulties in handling pose variations or occlusions when analyzing face images. By connecting with experienced developers who have faced similar challenges, they can gain valuable advice on how to overcome these obstacles more effectively.
Analyzing Facial Contours
Facial contour analysis is a vital aspect of face quality detection that involves extracting key landmarks from a face image. These landmarks help assess factors such as pose variations, occlusions, or facial expressions. By analyzing facial contours, algorithms can make accurate judgments about the quality of a face image.
The process begins by detecting specific points on the face, known as landmarks or keypoints. These landmarks represent important facial features such as the corners of the eyes, nose tip, mouth corners, etc. Once these keypoints are identified within an image, they can be used to analyze various aspects of the face.
For instance, if a person’s head is tilted at an angle in an image (pose variation), it may affect the overall quality of the image for certain applications such as facial recognition systems. By comparing the relative positions of keypoints against predefined standards or models, algorithms can determine if a particular pose variation falls within an acceptable range or if further adjustments are necessary.
Similarly, occlusions, such as objects obstructing parts of the face (e.g., glasses or hands), can also impact the quality of a face image. By analyzing the facial contours and identifying areas affected by occlusions, algorithms can assess the level of obstruction and its potential impact on subsequent face recognition or analysis tasks.
Conclusion
In conclusion, face quality detection technology has revolutionized the way we interact with digital systems and enhanced our overall security. We have explored the evolution of face detection technology, its various applications, technical aspects, and the importance of data security in implementing these systems. We have delved into the development process and the role of community and expertise in ensuring accurate face detection.
By understanding the advancements in face quality detection, we can harness its potential to improve not only security measures but also user experiences. As this technology continues to advance, it is crucial for developers and researchers to collaborate and stay updated on the latest developments. By doing so, we can ensure that face detection systems are reliable, efficient, and secure.
Now that you have gained insights into face quality detection, consider how this technology can be applied in your own field or industry. Explore its potential benefits and challenges, and engage with experts to stay informed about future advancements. Together, we can continue to shape a world where face detection technology contributes to a safer and more seamless digital experience.
Frequently Asked Questions
FAQ
How does face quality detection work?
Face quality detection uses advanced algorithms to analyze various aspects of a person’s face, such as facial landmarks, symmetry, skin texture, and expressions. By comparing these features against predefined criteria, the system can determine the overall quality of a face image, including factors like lighting conditions, blurriness, occlusions, and pose variations.
What is the importance of face quality detection in facial recognition systems?
Face quality detection plays a crucial role in ensuring accurate and reliable results in facial recognition systems. It helps filter out low-quality images that may hinder proper identification due to poor lighting conditions, blurriness, or other factors. By focusing on high-quality images during the recognition process, it enhances the performance and reliability of facial recognition technology.
Can face quality detection be used for security purposes?
Yes, face quality detection is highly valuable for security applications. By assessing the quality of captured face images in real-time or during enrollment processes, it helps prevent spoofing attempts using low-quality photographs or masks. This ensures that only genuine faces are authenticated, enhancing security measures in access control systems and identity verification processes.
Are there any privacy concerns related to face quality detection?
Face quality detection primarily focuses on technical aspects of an individual’s face image rather than personal information. However, it is essential to implement robust data security measures to protect any collected biometric data from unauthorized access or misuse. Adhering to legal regulations and privacy policies ensures that individuals’ privacy rights are respected while utilizing this technology.
How can businesses benefit from implementing face quality detection systems?
Businesses can leverage face quality detection systems across various industries. For example, in customer service settings with video conferencing capabilities or surveillance applications where accurate identification is crucial. Moreover, by filtering out low-quality images before processing them further for analysis or identification purposes, businesses can optimize their operations and improve overall efficiency.






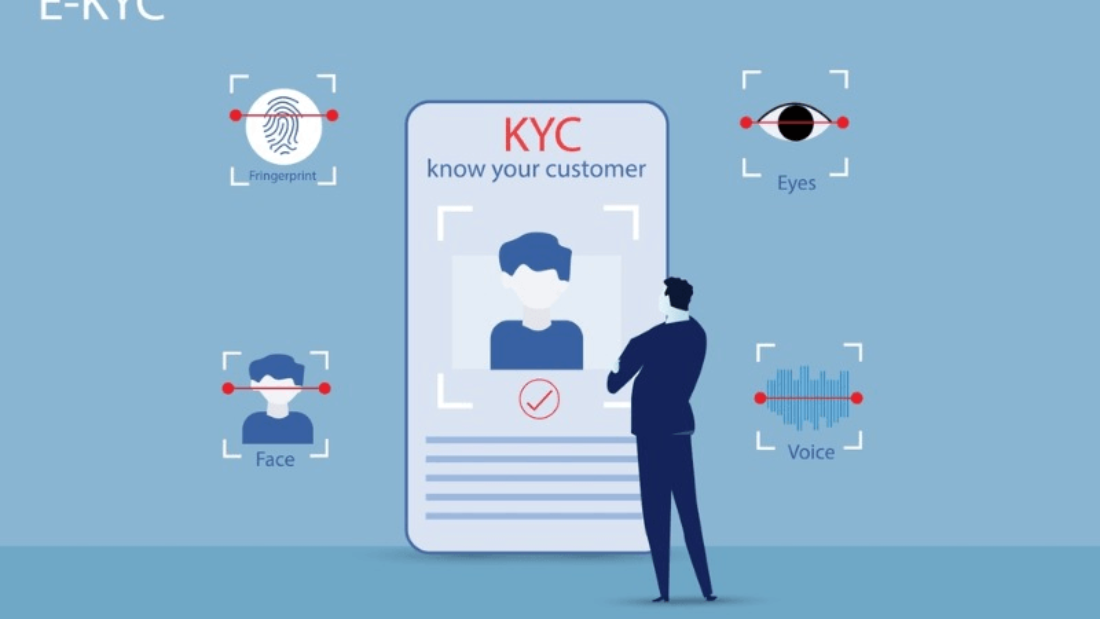
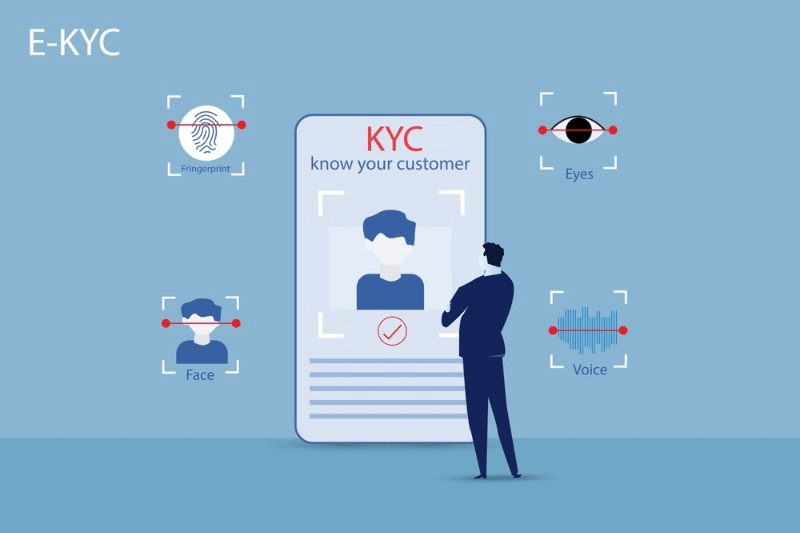



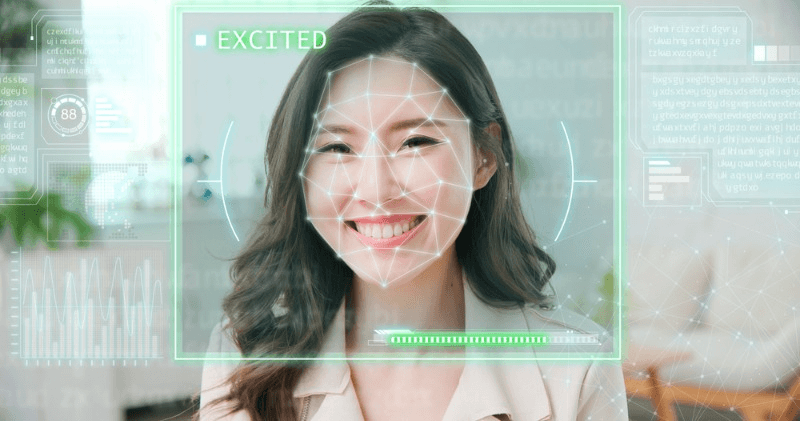

 Advanced facial clocking solutions come equipped with a range of features that further enhance their functionality and usability. These clock systems offer real-time monitoring capabilities that allow employers to track employee attendance instantly. Managers can easily view the attendance status of employees using the time clock system, which eliminates the need for manual processes or waiting for reports.
Advanced facial clocking solutions come equipped with a range of features that further enhance their functionality and usability. These clock systems offer real-time monitoring capabilities that allow employers to track employee attendance instantly. Managers can easily view the attendance status of employees using the time clock system, which eliminates the need for manual processes or waiting for reports.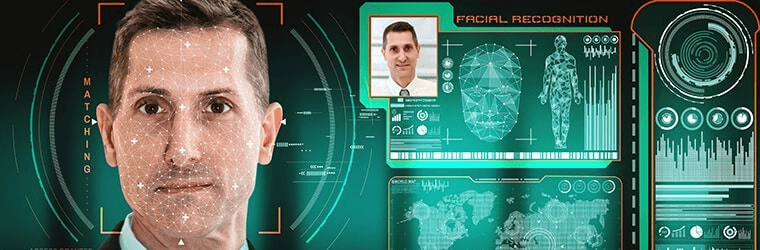



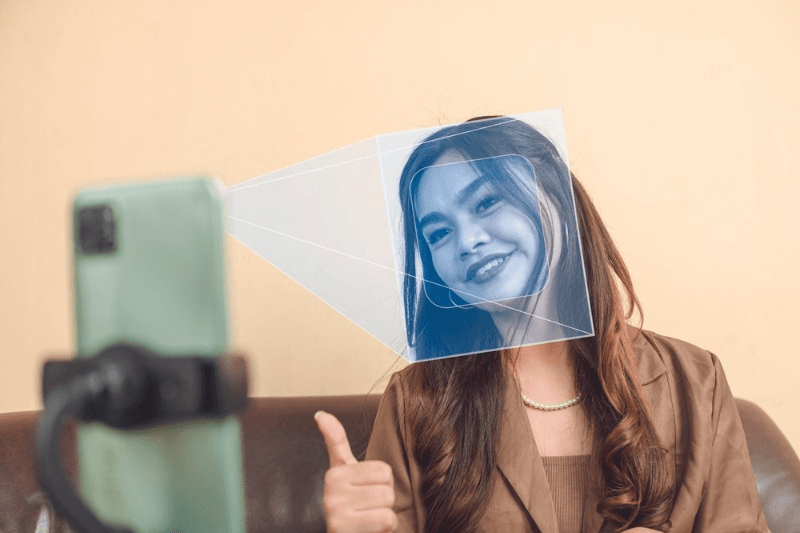 The process begins with high-resolution cameras capturing employee data through facial images on the time clock. These images captured by the time clock are then processed using complex algorithms that analyze unique facial features such as the distance between eyes, nose shape, and jawline structure. This meticulous analysis ensures accurate identification while minimizing false positives or negatives using a time clock.
The process begins with high-resolution cameras capturing employee data through facial images on the time clock. These images captured by the time clock are then processed using complex algorithms that analyze unique facial features such as the distance between eyes, nose shape, and jawline structure. This meticulous analysis ensures accurate identification while minimizing false positives or negatives using a time clock.