Are you curious about the capabilities and limitations of facial imagery recognition systems? These systems have the capability to analyze key fingerprints in mugshot images. The NIST FRVT (Face Recognition Vendor Test) is a technology evaluation that provides valuable insights on facial imagery. It involves participants who are evaluated using fmr technology. This comprehensive evaluation program conducts comparisons and benchmarks of face recognition algorithms using test data. It allows us to assess the performance and effectiveness of the participants.
The NIST FRVT aims to answer critical questions about the accuracy of face recognition technologies. This recognition performance test is essential for face recognition developers as it provides comparisons and insights into the accuracy of these technologies. Can they handle various scenarios and demographics? By evaluating different algorithms against standardized datasets, NIST FRVT offers objective measurements and benchmarks for developers and users alike in recognition performance tests. These tests allow for comparisons and validation of algorithms, measuring factors such as false match rate (FMR). It’s like having a litmus test for face recognition systems to determine the threshold of accuracy and validation. This test ensures that the system can successfully perform mated searches and display the results in a gallery format.
So buckle up as we embark on this journey to uncover the truth behind face recognition technology. In our gallery, we will showcase various fmr submissions and present them in a table for easy comparison.
Understanding the FRVT and FRTE
The NIST FRVT (Face Recognition Vendor Test) and FRTE (Face Recognition Technology Evaluation) are two important evaluations conducted by the National Institute of Standards and Technology (NIST) to assess the performance of face recognition technology. These evaluations help measure the accuracy and effectiveness of face recognition systems in various scenarios, such as identifying individuals in a crowded gallery or determining the threshold for matching faces. The NIST evaluations play a crucial role in advancing the capabilities of face recognition technology, ensuring its reliability and accuracy for applications like identifying twins or enhancing security measures. Let’s delve into these recognition performance tests to understand their purpose and focus. These evaluations involve setting a threshold for mated searches and analyzing the submissions.
FRVT: Evaluating Identification Performance
The FRVT primarily focuses on evaluating the identification performance of face recognition algorithms for mated searches. It sets a threshold for submission. In other words, the submission assesses how well these algorithms can accurately match a face image to a specific identity. This evaluation is crucial in determining the effectiveness and reliability of face recognition technologies in real-world scenarios.
During the evaluation, participants submit their algorithms for testing against large datasets containing millions of face images. The performance metrics used in the evaluation include accuracy, speed, storage requirements, and resource consumption. By analyzing these metrics, NIST aims to provide insights into the capabilities and limitations of different face recognition systems.
FRTE: Assessing Verification Performance
On the other hand, the FRTE assesses the verification performance of face recognition technologies. Verification involves confirming whether a given individual is who they claim to be by comparing their facial features with stored templates or reference images. This evaluation helps determine how well these technologies can accurately verify an individual’s identity.
Similar to the FRVT, participants in the FRTE submit their algorithms for testing against standardized datasets provided by NIST. These datasets consist of both genuine matches (where images belong to the same person) and impostor matches (where images belong to different people). The goal is to evaluate how well each algorithm can distinguish between genuine and impostor matches.
By conducting this evaluation, NIST provides valuable information about false acceptance rates (FAR), false rejection rates (FRR), precision-recall curves, and other relevant metrics. These metrics help quantify the accuracy and reliability of different face recognition technologies.
Both evaluations play a crucial role in advancing the field of face recognition technology. They help researchers, developers, and policymakers gain a deeper understanding of the strengths and weaknesses of various algorithms and systems. This knowledge is essential for making informed decisions about implementing face recognition technologies in different applications, such as security systems, law enforcement, and access control.
Delving into NIST FRVT’s Verification Performance
NIST FRVT, which stands for the National Institute of Standards and Technology Face Recognition Vendor Test, plays a crucial role in evaluating the accuracy and efficiency of face recognition systems. By conducting comprehensive tests, NIST FRVT provides objective measures of system effectiveness through its verification performance metrics.
The verification performance metrics used by NIST FRVT are designed to assess how well face recognition technologies can verify whether a person is who they claim to be. These metrics include the False Non-Match Rate (FNMR), which measures the rate at which an individual is falsely rejected by the system. A lower FNMR indicates a higher level of accuracy in correctly verifying individuals.
Another important metric evaluated by NIST FRVT is recognition performance test. This test focuses on assessing how well recognition algorithms perform in real-world scenarios. It helps identify areas where face recognition technologies excel or struggle.
By analyzing these metrics, NIST FRVT provides valuable insights into the strengths and weaknesses of different face recognition systems. For example, if a particular system consistently achieves low FNMR scores and performs well in real-world scenarios, it demonstrates a high level of accuracy and efficiency in verifying individuals’ identities.
On the other hand, if a system exhibits high FNMR scores or struggles with recognizing individuals accurately in various scenarios, it highlights areas for improvement. This information allows developers and researchers to refine their algorithms and enhance the overall performance of face recognition systems.
NIST FRVT’s evaluation process not only benefits developers but also ensures that end-users can have confidence in the reliability and effectiveness of face recognition technologies. The rigorous testing conducted by NIST enables users to make informed decisions about implementing these technologies for identity verification purposes.
For instance, government agencies responsible for border control or law enforcement can rely on NIST’s evaluations to select reliable face recognition systems that meet their specific needs. This helps in enhancing security measures and streamlining identity verification processes.
The Comprehensive Guide to Participating in FRVT
Step-by-Step Guide for Vendors
If you’re a vendor and want to participate in the NIST FRVT, here’s a step-by-step guide to help you get started.
Understand the Protocols: Familiarize yourself with the protocols and guidelines set by NIST for participation in the FRVT. These protocols ensure fair evaluation and comparison of face recognition algorithms.
Submit Your Algorithm: Prepare your face recognition algorithm according to the specifications provided by NIST. Ensure that your algorithm is compatible with the required formats and standards.
Participation Agreement: Fill out the participation agreement form provided by NIST. This agreement outlines your commitment to follow the rules and guidelines of the FRVT.
Submit Your Algorithm for Evaluation: Submit your algorithm to NIST for evaluation in the FRVT ongoing test series. Be sure to meet all submission deadlines specified by NIST.
Benchmarking Your Technology: By participating in the FRVT, you have an opportunity to benchmark your face recognition technology against other vendors in the industry. This allows you to assess its performance and identify areas for improvement.
Stay Updated: Join the mailing list provided by NIST to receive updates on important announcements, changes, and future test series of the FRVT.
Benefits of Participation
Participating in the NIST FRVT offers several benefits for vendors:
Industry Recognition: By having your algorithm evaluated in a reputable test series like FRVT, you gain industry recognition and credibility.
Performance Comparison: The FRVT allows you to compare your face recognition technology’s performance against other algorithms from various vendors. This comparison helps you understand how well your solution performs relative to others.
Identifying Strengths and Weaknesses: Through participation, you can identify both strengths and weaknesses of your algorithm. This insight helps you focus on improving the weaker areas and enhancing the overall performance of your technology.
Feedback from Experts: The evaluation process in FRVT involves expert analysis and feedback on your algorithm’s performance. This feedback can provide valuable insights for refining your face recognition solution.
Improving Customer Confidence: By participating in a rigorous evaluation like FRVT, you demonstrate your commitment to delivering reliable and accurate face recognition technology. This helps build trust and confidence among potential customers.
Driving Innovation:
Exploration of NIST’s Related Projects
NIST’s Involvement in Biometrics
NIST, the National Institute of Standards and Technology, plays a crucial role in evaluating and advancing biometric technologies. While the previous section focused on the FRVT (Face Recognition Vendor Test), it is important to note that NIST is involved in various other projects related to biometrics as well.
Evaluating Fingerprint and Iris Recognition
In addition to the FRVT, NIST conducts evaluations for fingerprint and iris recognition technologies. These evaluations help assess the performance of different algorithms and systems used for these biometric modalities. By analyzing large datasets and conducting rigorous testing, NIST provides valuable insights into the accuracy, reliability, and effectiveness of these technologies.
Other Evaluation Programs by NIST
Alongside the FRVT, NIST carries out several other evaluation programs that contribute to advancements in biometric technologies. One such program is the NIST Interagency Report (NIR) series, which focuses on evaluating algorithms for various biometric modalities.
Another notable project is the Iris Exchange (IREX) evaluation series, which specifically evaluates iris recognition algorithms. This program helps researchers and developers understand the strengths and limitations of different iris recognition systems.
Furthermore, NIST also conducts evaluations related to DNA matching technologies through its Forensic Science Program. These evaluations assist law enforcement agencies in accurately identifying suspects based on DNA evidence.
Broader Perspective on Advancements
Understanding NIST’s involvement in multiple projects related to biometrics provides us with a broader perspective on advancements in this field. The evaluations conducted by NIST not only ensure that these technologies meet certain standards but also drive innovation by encouraging researchers and developers to enhance their algorithms and systems.
By collaborating with various stakeholders including government agencies, academic communities, industry partners, and international organizations, NIST fosters an environment where ideas are exchanged freely. This collaboration facilitates knowledge sharing and encourages continuous improvement in biometric technologies.
For example, NIST’s evaluations have led to the development of more accurate and efficient fingerprint recognition algorithms, enabling law enforcement agencies to solve crimes more effectively. Similarly, advancements in iris recognition technologies have enhanced security measures at airports and other high-security facilities.
Investigating the Impact of Demographics and Masks in FRTE
How Demographic Factors Influence Face Recognition Performance
Demographic factors such as age, gender, and race can have a significant impact on the performance of face recognition systems. Researchers have found that certain demographics may be more accurately recognized than others due to variations in facial features and characteristics.
For instance, studies have shown that face recognition algorithms tend to perform better on younger individuals compared to older ones. This could be attributed to factors such as changes in skin elasticity and appearance that occur with aging. Similarly, gender can also influence face recognition accuracy, with some algorithms exhibiting higher error rates when identifying faces of one gender over the other.
Race is another important demographic factor that affects face recognition performance. Research has revealed that certain algorithms may exhibit lower accuracy rates when recognizing faces from racial minority groups compared to those from majority groups. This disparity highlights the need for continuous improvement and evaluation of these technologies to ensure fairness across different racial backgrounds.
The Challenges Faced by Face Recognition Systems with Masks
The widespread use of masks or other facial coverings poses unique challenges for face recognition systems. These technologies typically rely on capturing detailed facial imagery for accurate identification. However, when individuals wear masks, a significant portion of their face is obscured, making it difficult for the algorithms to extract key features necessary for identification.
This challenge becomes particularly pronounced when multiple faces are present in an image or video frame. The presence of masks can hinder the system’s ability to correctly identify each individual within a group setting. As a result, negative identification rates may increase, leading to potential misidentifications or false positives.
To address this issue, researchers and developers are actively exploring ways to enhance face recognition technology’s capability to handle masked faces effectively. Solutions include developing new algorithms that can adapt and recognize partially covered faces or leveraging additional contextual information such as body posture or gait analysis.
Improving Fairness and Accuracy in Face Recognition Technologies
Understanding the impact of demographics and masks is crucial for improving the fairness and accuracy of face recognition technologies. By identifying and addressing biases associated with age, gender, race, and facial coverings, developers can work towards creating more inclusive systems that perform consistently across different populations.
Efforts are underway to collect diverse datasets that encompass a wide range of demographic factors to ensure better representation during algorithm development.
FATE Projects and Their Evaluation Methods
Ethical Concerns Addressed by FATE Projects
FATE (Fairness, Accountability, Transparency, and Ethics) projects are dedicated to addressing the ethical concerns surrounding face recognition technologies. These projects recognize the potential biases and risks associated with facial recognition algorithms and strive to ensure that these technologies are developed and deployed responsibly. By focusing on fairness, accountability, transparency, and ethics, FATE projects aim to create a more equitable and trustworthy environment for the use of face recognition systems.
Evaluating Fairness and Transparency
One of the key aspects discussed in this section is the evaluation methods employed by FATE projects to assess the fairness and transparency of face recognition algorithms. These evaluation methods play a crucial role in determining how well these algorithms perform in real-world scenarios.
To evaluate fairness, FATE projects consider various demographic factors such as age, gender, race, and ethnicity. By analyzing how well an algorithm performs across different demographic groups, they can identify any disparities or biases that may exist. This evaluation helps ensure that face recognition technology does not disproportionately impact certain individuals or communities.
Transparency is another important aspect evaluated by FATE projects. They examine how transparent an algorithm’s decision-making process is by assessing its documentation, model architecture, training data sources, and disclosure of potential limitations. This evaluation ensures that users have a clear understanding of how the algorithm operates and can trust its outcomes.
Algorithm Submissions for Evaluation
FATE projects encourage algorithm submissions from researchers and developers worldwide to participate in their evaluations. These submissions provide valuable insights into the performance of different face recognition algorithms under diverse conditions. By evaluating multiple algorithms from various sources, FATE projects can gain a comprehensive understanding of the strengths and weaknesses within existing technologies.
During the evaluation process, match rates and error rates are carefully analyzed to determine algorithm performance. Match rates measure how accurately an algorithm matches faces against a database or other images provided. Error rates, on the other hand, assess the algorithm’s ability to correctly identify or reject faces. These metrics help evaluate the effectiveness and reliability of face recognition algorithms.
Ensuring Responsible Development and Deployment
FATE projects play a crucial role in ensuring responsible development and deployment of face recognition systems. By evaluating fairness and transparency, these projects aim to address biases and promote accountability within the field of facial recognition technology. They provide valuable insights into algorithm performance while considering demographic factors, ultimately contributing to more equitable and trustworthy face recognition systems.
Breaking Down FRVT Results and Performance Metrics
The NIST FRVT evaluations provide valuable insights into the performance of face recognition systems. By analyzing the results and understanding the performance metrics used by NIST, we can identify areas for improvement in these technologies.
Analysis of Results
The NIST FRVT evaluations involve testing numerous face recognition algorithms to measure their accuracy and efficiency. These evaluations assess various aspects of system performance, such as identification accuracy, verification accuracy, and speed. The results obtained from these evaluations help researchers and developers gain a better understanding of how well their systems perform compared to others in the field.
One important metric that is commonly used in evaluating face recognition systems is the false match rate (FMR). The FMR measures the likelihood of a system incorrectly matching two different individuals. A lower FMR indicates a higher level of accuracy in distinguishing between different faces. By analyzing the FMR values obtained during the evaluation process, researchers can gauge how well a particular algorithm performs in terms of false matches.
Another crucial metric used in evaluating face recognition systems is the genuine match rate (GMR). The GMR measures how often a system correctly matches two images of the same individual. A higher GMR indicates better accuracy in recognizing individuals correctly. Evaluating both FMR and GMR provides a comprehensive view of a system’s overall performance.
Performance Metrics Used by NIST
NIST employs several performance metrics to evaluate face recognition systems thoroughly. One commonly used metric is known as rank-1 identification accuracy. This metric measures how often an algorithm correctly identifies an individual among multiple candidates when presented with their image. Higher rank-1 identification accuracy signifies better overall performance.
Another important metric utilized by NIST is verification accuracy, which measures how accurately a system verifies whether two images belong to the same person or not. High verification accuracy ensures that only legitimate matches are accepted while minimizing false positives.
Speed is yet another critical aspect evaluated by NIST. Face recognition systems need to perform efficiently, especially in real-time applications. By measuring the speed at which a system processes and matches images, NIST can assess the efficiency of different algorithms.
Identifying Areas for Improvement
Understanding the FRVT results and performance metrics allows us to identify areas where face recognition technologies can be improved. For instance, if a system exhibits a high false match rate or low identification accuracy, developers can focus on refining their algorithms to reduce errors and enhance overall performance.
Paperless Travel Initiatives and Their Evaluation in FRVT
Utilization of Face Recognition Technologies in Paperless Travel Initiatives
In recent years, face recognition technologies have been increasingly utilized in paperless travel initiatives to enhance airport security and streamline the passenger experience. These initiatives leverage the power of biometric data, specifically facial images, to automate various processes throughout the travel journey.
By capturing and analyzing visa images or other biometric data at different checkpoints, such as check-in counters, security screening areas, and immigration controls, airports can expedite the verification process while maintaining robust security measures. This technology enables passengers to move through these checkpoints seamlessly without the need for physical documents or manual identification checks.
NIST’s Evaluation of Face Recognition Technologies
The National Institute of Standards and Technology (NIST) plays a crucial role in evaluating the effectiveness of face recognition technologies used in paperless travel initiatives. NIST conducts evaluations through its Face Recognition Vendor Test (FRVT) program, which assesses the performance and accuracy of various algorithms and systems.
Through comprehensive testing protocols, NIST evaluates how well these technologies perform across different scenarios, such as varying lighting conditions, pose variations, age differences, and image quality. The goal is to ensure that face recognition technologies are reliable and effective in real-world applications.
NIST’s evaluations provide valuable insights into the strengths and limitations of different face recognition systems. This information helps policymakers, airport authorities, and technology developers make informed decisions about deploying these technologies within paperless travel initiatives.
Contributions to Streamlining Airport Processes
Paperless travel initiatives evaluated by NIST FRVT contribute significantly to streamlining airport processes and improving border control. By leveraging face recognition technologies at various stages of the travel journey, airports can achieve several benefits:
Enhanced Security: The use of biometric data ensures a high level of accuracy in identifying individuals compared to traditional identification methods. This enhances security by reducing instances of identity fraud and unauthorized access.
Efficient Passenger Experience: Paperless travel initiatives eliminate the need for passengers to present physical documents repeatedly, reducing wait times and enhancing the overall travel experience. Passengers can move through checkpoints swiftly, leading to improved efficiency and reduced congestion.
Increased Automation: By automating identification processes using face recognition technologies, airports can achieve higher levels of automation in their operations. This reduces the reliance on manual interventions, resulting in cost savings and improved resource allocation.
Improved Border Control:
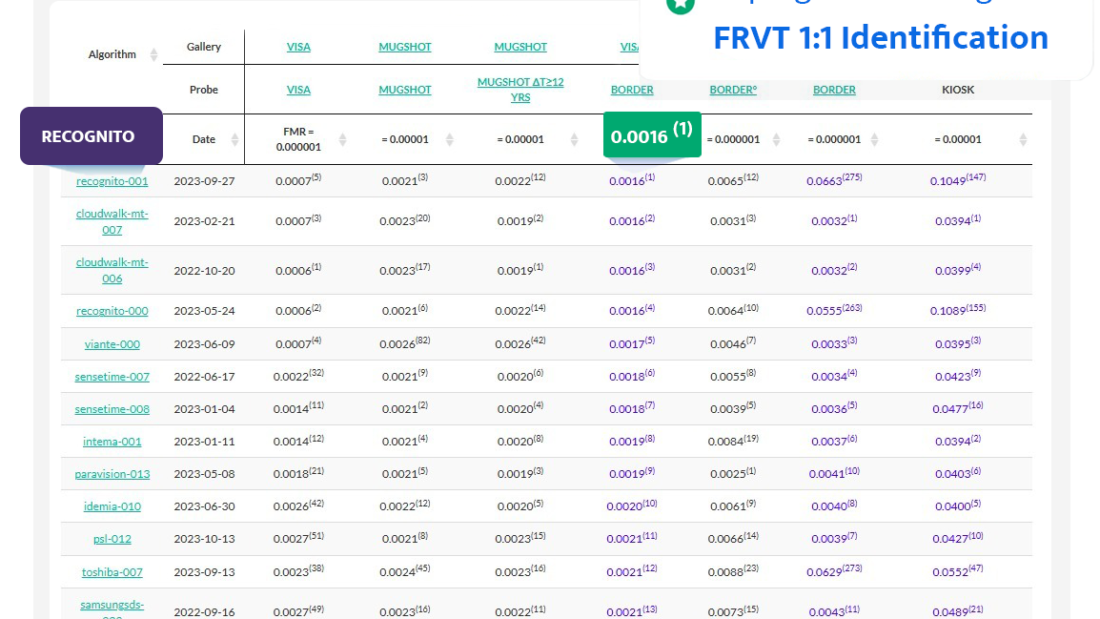
Recognito is NIST FRVT Top 1 Algorithm Provider
Recognito: A Leading Algorithm Provider
Recognito has established itself as the top algorithm provider in the National Institute of Standards and Technology (NIST) Face Recognition Vendor Test (FRVT). This prestigious recognition highlights the exceptional capabilities and performance of Recognito’s facial recognition technology.
NIST FRVT: The Standard for Evaluation
The NIST FRVT serves as the benchmark for evaluating facial recognition algorithms. It rigorously tests various algorithms against a set of standardized metrics, ensuring accuracy, efficiency, and reliability. Being recognized as the top algorithm provider in this evaluation demonstrates Recognito’s commitment to excellence and innovation.
Unparalleled Accuracy and Performance
Recognito’s achievement as the NIST FRVT Top 1 Algorithm Provider can be attributed to its unparalleled accuracy and performance. The algorithm consistently delivers outstanding results in terms of identification accuracy, speed, and robustness. Its advanced features enable it to handle diverse scenarios with ease, making it a reliable choice for various applications.
Robust Against Challenging Conditions
One of the key strengths of Recognito’s algorithm is its ability to perform well under challenging conditions. It excels in scenarios involving low-quality images, occlusions, variations in lighting conditions, or changes in facial expressions. This robustness ensures that Recognito’s technology can effectively handle real-world situations where other algorithms may struggle.
Versatile Applications
Recognito’s algorithm finds applications across a wide range of industries and sectors. Its versatility allows it to be used for identity verification in airports, access control systems for secure facilities, surveillance systems for public safety, or even customer authentication in financial institutions. The reliability and accuracy provided by Recognito make it an invaluable tool for organizations seeking robust facial recognition solutions.
Ethical Considerations
While recognizing Recognito’s achievements in the field of facial recognition technology, it is crucial to address ethical considerations associated with its use. As facial recognition becomes more prevalent, it is essential to ensure that privacy and data protection are upheld. Recognito is committed to adhering to strict ethical guidelines, prioritizing user consent, and implementing secure data management practices.
Continued Innovation
Recognito’s success as the NIST FRVT Top 1 Algorithm Provider serves as a testament to its dedication to continuous innovation. The company remains at the forefront of research and development in facial recognition technology, constantly striving to improve accuracy, efficiency, and user experience.
Conclusion
Congratulations! You have now gained a comprehensive understanding of the NIST FRVT and its various aspects. From exploring the verification performance to delving into related projects, you have witnessed the power and potential of facial recognition technology. The results and performance metrics have shed light on the capabilities and limitations of different algorithms, while the evaluation methods have provided insights into the fairness and transparency of these systems.
As you reflect on the impact of demographics and masks in FRTE, as well as the evaluation of paperless travel initiatives, you realize the far-reaching implications of this technology in our society. Facial recognition has the potential to revolutionize security measures, streamline processes, and enhance convenience. However, it also raises important ethical considerations that must be addressed to ensure fairness, privacy, and accountability.
Now armed with this knowledge, it is up to you to engage in further exploration and critical thinking. Consider how facial recognition technology can be responsibly utilized in various domains. Advocate for policies that prioritize transparency, accountability, and inclusivity. By actively participating in discussions surrounding facial recognition technology, you can contribute to shaping a future where this powerful tool is used for the greater good.
Frequently Asked Questions
FAQ
What is NIST FRVT?
NIST FRVT stands for National Institute of Standards and Technology Face Recognition Vendor Test. It is a benchmarking program that evaluates the performance of face recognition algorithms provided by different vendors.
How does NIST FRVT assess verification performance?
NIST FRVT assesses verification performance by measuring the accuracy of face recognition algorithms in correctly verifying whether two images belong to the same person or not.
Can I participate in FRVT?
Yes, you can participate in FRVT as a vendor by following the guidelines provided by NIST. The comprehensive guide to participating in FRVT will provide you with all the necessary information and steps to join the evaluation.
What are FATE projects in relation to NIST FRVT?
FATE projects refer to evaluations conducted under Fairness, Accountability, Transparency, and Ethics considerations. These projects aim to ensure that face recognition technologies are unbiased, transparent, and ethical.
Is Recognito the top algorithm provider for NIST FRVT?
Yes, Recognito is recognized as one of the top algorithm providers in NIST FRVT. Their face recognition algorithm has demonstrated exceptional performance and accuracy in various evaluations conducted by NIST.