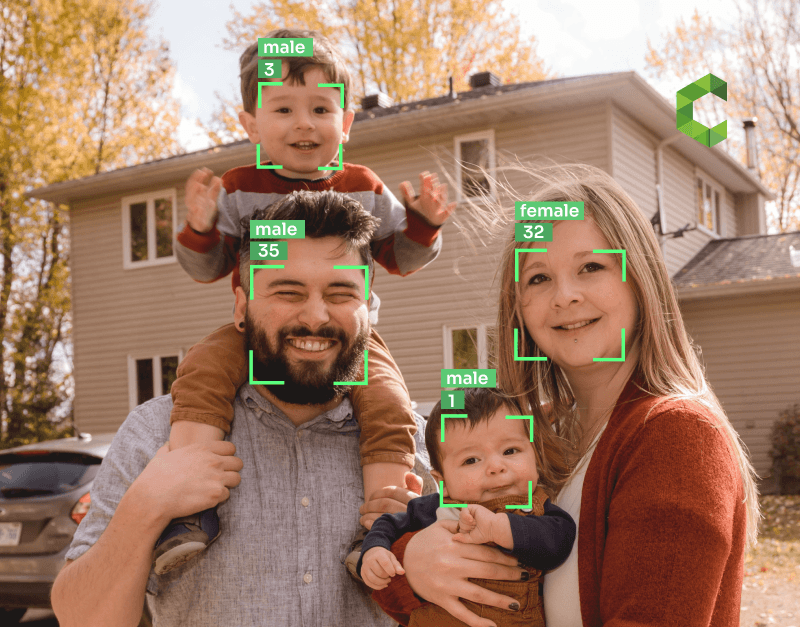
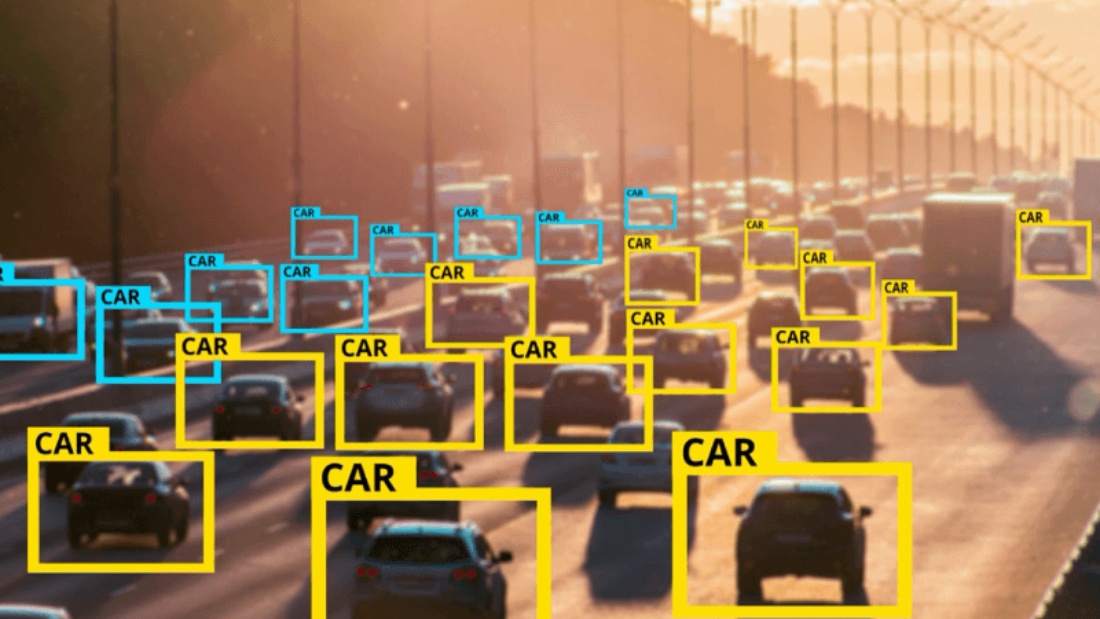
In the ever-evolving landscape of video analytics, face images and presentation attack detection play a critical role in safeguarding the integrity and security of facial recognition systems. Liveness detection is essential to prevent photo-based spoofing. With advancements in technology, video analytics has revolutionized the way we analyze and interpret visual data. Now, with the use of dataset testing and intellivision, we can enhance the accuracy of our classifiers and delve deeper into 3D visual analysis. This has led to significant improvements in anti-spoofing techniques, aimed at detecting and preventing fraudulent attempts using protocols, RF technology, valid user authentication, and classifiers.
This article provides an overview of the methods and technologies used in anti-spoofing within video analytics, including liveness detection, testing, IR cameras, and reflection. In this blog post, we will explore various approaches that have been developed for testing classifiers in order to tackle the challenge of recognizing only genuine faces. These approaches involve reflection and the identification of spoof images. From state-of-the-art classifiers to innovative data analysis methods, we will delve into the art of distinguishing between real faces and spoofed ones. In this blog post, we will explore the use of datasets, reflection, and figure in achieving accurate classification.
Join us as we dive into the world of anti-spoofing in video analytics, reflecting on its importance and examining practical examples of how it enhances system performance. We will explore various protocols and analyze datasets to replay real-world scenarios. Stay tuned for valuable insights and information on this crucial aspect of modern security systems. We will provide reflection and reference on the changes and results.
Fundamentals of Anti-Spoofing
Video Analytics Overview
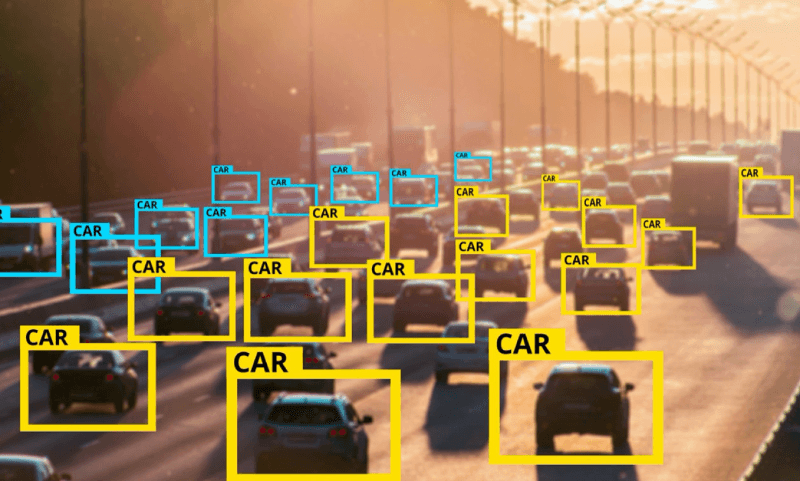
Video analytics is a powerful technology that automates the analysis of video content to extract meaningful information. This technology utilizes image quality features, datasets, intellivision, and classifiers to enhance its capabilities. It enables real-time monitoring using classifiers, object detection, tracking, and behavior analysis based on image quality features. This can be applied to various datasets and even video clips. In the context of anti-spoofing, video analytics plays a vital role in detecting presentation attacks by analyzing replays and referencing protocols to ensure image quality features are not compromised.
With video analytics, security systems can analyze video footage and identify suspicious activities or individuals. This is particularly important in detecting face spoofing attacks. By utilizing a comprehensive dataset and advanced algorithms, the system can accurately distinguish between genuine and fake faces. Additionally, image quality features play a crucial role in ensuring the effectiveness of such systems. With the integration of Intellivision technology, security systems can enhance their capabilities and provide more robust protection against face spoofing incidents. It allows for efficient monitoring of large areas and enhances the overall security level by providing valuable insights into potential threats. The image quality features of the dataset ensure accurate detection, while also preventing spoof attempts. This reference dataset is essential for maintaining a high level of security.
Anti-Spoofing Significance
Anti-spoofing is an essential component in preventing unauthorized access, identity fraud, and replay attacks. It helps to ensure the security and integrity of the system by verifying the authenticity of the reference signals (RF). Without effective anti-spoofing measures, facial recognition systems can be easily deceived by spoofing attacks. These attacks can manipulate the rf signals and distort the dataset used for recognition. As a result, the system may incorrectly match a spoofed reference image with a genuine figure.
Spoofing attacks involve presenting fake representations such as photos or videos to trick the system into recognizing them as genuine faces. This can be seen in the dataset, where the figure shows examples of spoofed images. It is important to reference these examples when discussing the impact of spoofing attacks on face recognition systems. Additionally, replay attacks, which involve replaying pre-recorded videos or images, are another form of spoofing that can be harmful to the system. This poses a significant threat to security systems that rely on facial recognition for access control or identification purposes, especially when faced with a spoof attack using a dataset as a reference.
The significance of anti-spoofing lies in its ability to ensure the authenticity of biometric data captured by video analytics systems. This is achieved by analyzing image quality features from the dataset and replaying them to obtain accurate results. By implementing robust anti-spoofing techniques, organizations can enhance their security measures and protect against fraudulent activities, such as replay attacks. These techniques help organizations defend against attackers attempting to exploit vulnerabilities in their RF systems. To develop effective anti-spoofing techniques, organizations need access to a comprehensive dataset that includes examples of various attack scenarios.
Spoofing Detection Methods
Spoofing detection methods aim to differentiate between genuine facial features and fake representations used in spoofing attacks. These methods utilize the rf algorithm to analyze the dataset and assess image quality. By applying the mfsd technique, they can accurately identify and classify spoofing attempts. These methods employ various techniques to analyze different characteristics of the face and identify signs of manipulation or presentation attacks, such as image quality features and dataset. The results obtained from these methods help in detecting spoof attempts.
Texture analysis is one common method used in spoofing detection to identify attack patterns. It involves analyzing image quality features in a dataset and applying the rf algorithm for accurate detection. The analysis of patterns within the face image is crucial for distinguishing between real skin texture and artificial textures present in printed images or masks. This is important for ensuring the quality features of the dataset and obtaining accurate results in detecting spoof attempts.
Motion analysis is another technique that focuses on detecting unnatural movements within a face image. This technique is particularly useful in identifying spoof attempts and ensuring the quality features of the dataset. The results obtained from motion analysis provide valuable insights into the authenticity of the face image. By examining facial dynamics such as blinking or head rotation, motion analysis algorithms can identify signs of spoofing attempts. This analysis is crucial for accurately assessing the image quality features of the dataset and detecting any potential attacks. The results of this analysis provide valuable insights into the security of facial recognition systems.
Frequency-based analysis is a method of analyzing frequency components present in an image to identify quality features. This analysis can be performed using the rf dataset, and the results obtained are valuable for evaluating the image’s quality. The dataset helps in identifying discrepancies between genuine faces and spoofing materials, such as printed images that may exhibit different frequency patterns. This is possible due to the quality features of the dataset, which are used in the rf algorithm to generate accurate results.
Computer Vision and Liveness Detection
Role of Computer Vision
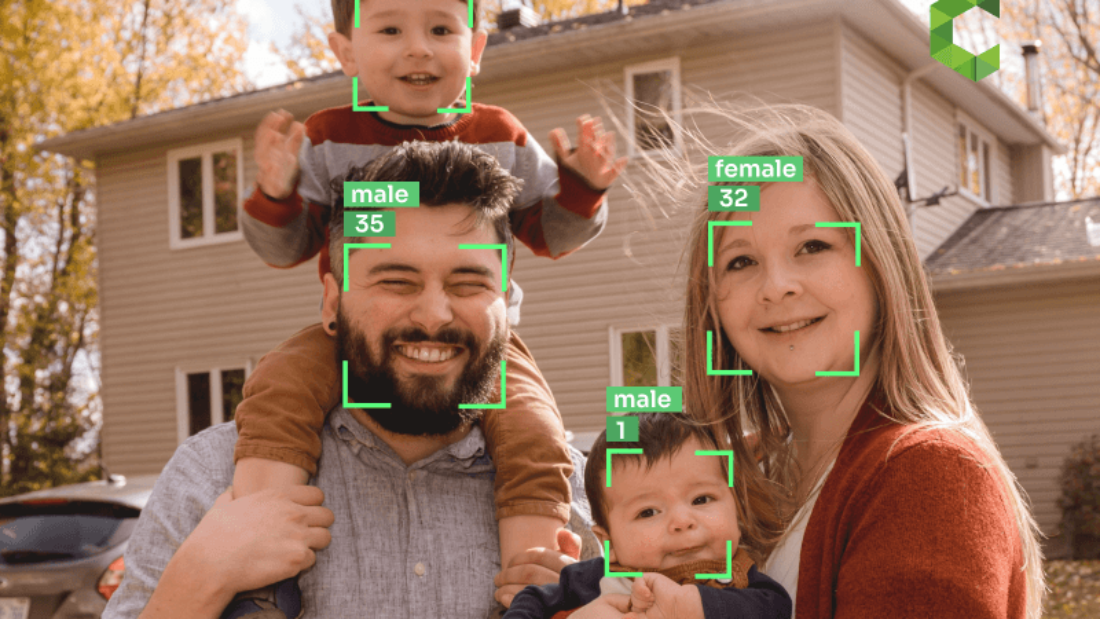
Computer vision plays a crucial role in anti-spoofing by enabling machines to understand and interpret visual data, including image quality features, dataset, attack, and rf. The dataset enables the extraction of high-quality results from images or videos, helping to distinguish between real faces and spoofed ones. This is made possible by extracting meaningful features using the MFSd algorithm. By leveraging computer vision techniques, anti-spoofing algorithms can detect anomalies and irregularities in facial patterns, improving image quality features and providing robust defense against attacks. These algorithms yield reliable results, making them essential in the field of Multimodal Facial Spoofing Detection (MFSD).
Liveness Indicators
Liveness indicators are used to determine whether a face is live or a static representation. These indicators rely on image quality features, such as the clarity and sharpness of the image, as well as equation-based calculations. The results generated by these indicators help identify and differentiate between live faces and spoof attempts. These indicators, such as eye blinking, head movement, or response to challenges, can provide results and help detect spoof attacks. Additionally, they are essential for evaluating image quality features. Analyzing liveness indicators ensures the authenticity of facial recognition by allowing anti-spoofing systems to identify presentation attacks and produce accurate results. This helps maintain high image quality and utilize advanced features.
One common liveness indicator is eye blinking. A live person will naturally blink their eyes, while a static image or video will not exhibit this behavior. This distinction in blinking behavior is an important indicator of the quality and authenticity of the results, as it helps to identify potential spoofs and differentiate real features. Head movement is another important indicator of image quality and features, as it demonstrates the presence of a real person interacting with the system, which helps prevent spoof and attack. Challenging the user with tasks like smiling or following prompts further validates their liveliness and helps prevent spoof attacks. Additionally, it ensures the image quality and features are accurately assessed.
Deep Learning Applications
Deep learning techniques have revolutionized anti-spoofing by enabling more accurate and robust detection of image quality and features, while also defending against potential attacks. Convolutional Neural Networks (CNNs) and Recurrent Neural Networks (RNNs) are commonly used in deep learning-based anti-spoofing models, which enhance features, defend against attacks, and improve image quality.
CNNs excel at extracting spatial features from images, making them well-suited for analyzing facial characteristics relevant to quality and anti-spoofing attack. They can learn complex patterns within an image hierarchy, allowing them to discern between genuine faces and spoofed ones based on distinctive visual cues. These features ensure the quality of their ability to detect and prevent an attack.
On the other hand, RNNs are effective at modeling temporal dependencies in sequential data such as videos. These models have features that allow them to capture the image quality and detect potential spoof attacks. They can capture long-term dependencies across frames, helping detect subtle changes indicative of real human presence compared to static representations often found in spoofing attempts. This capability improves the image quality and features of the system, making it more resistant to attack.
Biometric Verification Techniques
Voice Biometrics
Voice biometrics, an image, has powerful features that can be integrated with video analytics to enhance anti-spoofing capabilities and protect against attack. By combining facial and voice recognition features, image spoof attack systems can verify the identity of an individual more securely. This additional layer of authentication features makes it harder for spoofing attacks to succeed. The image feature adds an extra level of security to prevent spoofing attacks.
In voice biometrics, the unique characteristics and features of an individual’s voice image are analyzed and compared against a stored database to detect and prevent spoof attacks. These features and characteristics include factors such as pitch, tone, rhythm, and image. Additionally, we will explore how these elements can be utilized to create a spoof. By capturing and analyzing these features, voice biometric systems can accurately identify individuals.
Integrating voice biometrics with video analytics features allows for real-time verification during video surveillance. When someone approaches a security checkpoint or access point, their face is captured by the camera system while their voice is recorded simultaneously. These features ensure accurate identification and enhanced security measures. The facial features are extracted from the image or video and compared against a database of known individuals using face recognition algorithms. At the same time, the person’s voice is analyzed using voice biometric technology to ensure consistency with their registered profile. This analysis includes evaluating the various features of their voice.
This combination of facial and voice recognition features significantly strengthens anti-spoofing measures. It adds another layer of security by verifying both visual and auditory cues associated with an individual’s identity, enhancing the features. Spoofers attempting to deceive the system by presenting fake faces or voices would find it much more challenging to bypass this dual verification process with its enhanced features.
Face Recognition
Face recognition is a fundamental component of anti-spoofing systems in video analytics. The features of face recognition play a crucial role in detecting and preventing spoofing attempts. It involves comparing facial features extracted from images or videos against a database of known individuals.
Sophisticated face recognition algorithms with advanced features play a crucial role in identifying potential presentation attacks and ensuring the authenticity of faces captured by surveillance cameras. These algorithms analyze various aspects such as shape, texture, and landmarks on the face to create unique templates for each individual in the database.
When an unknown face is detected by a camera system, its features are extracted and compared against these templates for a potential match. If a match is found, the system can authenticate the individual’s identity and take appropriate action based on predefined rules.
Advanced Anti-Spoofing Technologies
3D Camera Utilization
3D cameras play a crucial role in enhancing anti-spoofing capabilities in video analytics systems. Unlike traditional cameras that capture only visual data, 3D cameras also capture depth information. This additional dimension allows for better analysis of facial structure and geometry, making it much harder for spoofing attacks to deceive the system.
By incorporating depth information into the analysis, video analytics systems can more accurately detect presentation attacks. For example, when someone tries to fool the system with a printed image or a mask, the lack of realistic depth cues will be evident to the 3D camera. This enables the system to differentiate between real faces and fake ones, significantly improving overall security.
The use of 3D cameras in anti-spoofing technology has proven to be highly effective. They provide an extra layer of protection against sophisticated spoofing techniques and ensure that only genuine individuals are granted access or identified correctly within video surveillance applications.
IR Camera Integration
Integrating infrared (IR) cameras into video analytics systems is another powerful way to enhance anti-spoofing capabilities. IR cameras have the ability to detect temperature differences on the face, which can help distinguish between real faces and various types of presentation attacks such as masks or printed images.
When an individual presents their face to an IR camera, it captures not only the visual appearance but also thermal patterns emitted by different parts of their face. This thermal data provides valuable insights that aid in determining whether a presented face is genuine or a result of a spoofing attempt.
Face Recognition Anti-Spoofing Methods
Presentation Attack Prevention
Presentation attack prevention techniques play a crucial role in the field of anti-spoofing in video analytics. These methods are designed to deter and prevent spoofing attempts, ensuring the integrity and reliability of face recognition systems. One common approach is to implement random challenges that require specific actions or gestures from the user. By introducing these challenges, such as blinking or smiling, video analytics systems can verify the presence of a real person and minimize the risk of successful spoofing attacks.
The use of presentation attack prevention measures adds an extra layer of security to face recognition systems. It increases the complexity for potential attackers attempting to deceive the system with fake identities or manipulated images or videos. By requiring users to perform specific actions, it becomes more challenging for malicious actors to replicate human behavior accurately.
Cross-Dataset Testing
To ensure the effectiveness and robustness of anti-spoofing algorithms, cross-dataset testing is essential. This evaluation technique involves training and testing anti-spoofing models on different datasets representing various scenarios and conditions. The goal is to assess how well these algorithms generalize across different environments, lighting conditions, camera angles, and other factors that may impact their performance.
Cross-dataset testing helps identify potential vulnerabilities in anti-spoofing systems by exposing them to diverse datasets. It allows researchers and developers to evaluate if their algorithms can detect spoofing attempts consistently across different scenarios beyond those used during training. This process enhances the overall reliability and accuracy of anti-spoofing technologies.
Image Quality in Anti-Spoofing
Image Quality Evaluation
Image quality evaluation is a critical component of anti-spoofing in video analytics. It involves assessing the quality and authenticity of captured facial images to ensure accurate detection and prevent spoofing attacks. By analyzing various metrics such as sharpness, noise level, and resolution, anti-spoofing systems can determine if an image has been manipulated or tampered with.
When evaluating image quality, sharpness is an important factor to consider. A sharp image contains clear and well-defined edges, making it easier for the system to extract relevant features for analysis. On the other hand, a blurry or distorted image may hinder accurate feature extraction and compromise the effectiveness of anti-spoofing algorithms.
Another metric used in image quality evaluation is noise level. Noise refers to random variations in pixel values that can affect the overall clarity of an image. High levels of noise can make it challenging for anti-spoofing systems to accurately detect facial features and distinguish between genuine faces and spoofed ones.
Resolution is also a crucial aspect when evaluating image quality. Higher resolution images generally provide more detailed information about facial features, enabling better discrimination between real faces and fake ones. Lower resolution images, on the other hand, may lack sufficient detail for accurate analysis, potentially leading to false positives or negatives in anti-spoofing detection.
By considering these metrics during image quality evaluation, anti-spoofing systems can enhance their ability to detect signs of manipulation or tampering in captured facial images. This ensures that only authentic faces are recognized while minimizing the risk of falling victim to spoofing attacks.
Optimal Feature Selection
Optimal feature selection plays a vital role in improving the performance of anti-spoofing algorithms by identifying the most relevant and discriminative facial features. This process aims to reduce computational complexity while maximizing detection accuracy.
In face recognition-based anti-spoofing, various facial features such as texture, color, and shape are extracted from the captured images. However, not all features contribute equally to the detection process. Some features may be more informative in distinguishing between genuine faces and spoofed ones.
By selecting the optimal set of features, anti-spoofing algorithms can focus on the most discriminative aspects of a face. This reduces computational overhead by eliminating irrelevant or redundant information during the analysis process. As a result, the system can achieve faster and more accurate detection of spoofing attacks.
To determine the optimal feature set, researchers often employ feature selection techniques such as principal component analysis (PCA) or linear discriminant analysis (LDA). These methods help identify the most informative features that contribute significantly to differentiating between real and fake faces.
Classifier Fusion for Enhanced Security
Fusing Classifier Results
Fusing classifier results is a technique that combines the outputs from multiple classifiers to make a final decision in anti-spoofing. Instead of relying on a single classifier, this fusion approach leverages the strengths of individual classifiers to improve overall accuracy.
By fusing classifier results, video analytics systems can achieve better performance in detecting presentation attacks. Each classifier may focus on different aspects of spoof detection, such as analyzing facial features, motion patterns, or texture variations. Combining their outputs allows for a more comprehensive assessment of whether a face is genuine or being presented through a spoofing attack.
For example, one classifier might excel at identifying texture irregularities associated with printed images or masks, while another might specialize in detecting unnatural facial movements indicative of video playback. By combining these different insights, the system can enhance its ability to distinguish between genuine users and presentation attacks.
Secure Face Recognition
In addition to fusing classifier results, implementing secure face recognition measures is crucial for protecting against spoofing attacks during the recognition process. Validating the identity of individuals accurately and securely is essential for maintaining security and preventing unauthorized access or identity fraud.
One approach to secure face recognition involves multi-factor authentication. This means requiring additional forms of verification beyond just facial recognition alone. For example, users may be prompted to provide a fingerprint scan or enter a unique code sent to their mobile device alongside their facial biometrics.
Continuous monitoring of liveness indicators is another important aspect of secure face recognition. Liveness indicators refer to dynamic characteristics that can help determine if the captured face belongs to a live person or if it has been manipulated through spoofing techniques. These indicators could include factors like blinking patterns, head movement analysis, or even asking the user to perform specific actions like smiling or speaking certain words.
IntelliVision’s Approach to Fraud Protection
Fraud Protection Enhancement
Anti-spoofing in video analytics is a crucial aspect of fraud protection. By preventing spoofing attacks, it adds an extra layer of security to ensure the integrity and authenticity of biometric data. This enhancement plays a vital role in safeguarding against identity theft and fraudulent activities.
Spoofing attacks involve the use of fake or manipulated biometric data to deceive authentication systems. With anti-spoofing measures in place, video analytics systems can detect and prevent these attacks effectively. By analyzing various factors such as facial expressions, eye movements, or voice patterns, these systems can differentiate between genuine individuals and impostors.
The integration of anti-spoofing techniques enhances the overall security posture of video analytics solutions. It ensures that only legitimate users are granted access to sensitive areas or valuable assets. For example, financial institutions can utilize anti-spoofing in their surveillance systems to protect against fraudulent transactions by verifying the authenticity of customers’ identities.
Advanced Recognition Technologies
To further enhance anti-spoofing capabilities, video analytics systems can leverage advanced recognition technologies. These technologies offer additional biometric modalities that complement traditional methods like fingerprint recognition or face detection.
One such technology is iris recognition, which analyzes unique patterns within the iris for identification purposes. Iris recognition provides a highly accurate and secure form of authentication since each individual’s iris pattern is distinct and difficult to counterfeit.
Another advanced recognition technology is gait analysis, which focuses on analyzing an individual’s walking style or pattern. Gait analysis takes into account factors such as stride length, foot angle, and body movement characteristics. This method can be particularly useful for identifying individuals at a distance or in situations where other biometric features may not be easily captured.
Achieving Comprehensive Security
Deep Learning in Anti-Spoofing
Deep learning has revolutionized the field of anti-spoofing, providing a more accurate and efficient way to detect fraudulent activities. By utilizing deep neural networks, video analytics systems can learn complex patterns and features from large datasets, enhancing their ability to distinguish between real and fake faces.
Traditionally, anti-spoofing techniques relied on simple rule-based algorithms that were easily fooled by sophisticated spoofing attacks. However, with the integration of deep learning techniques, the effectiveness of anti-spoofing in video analytics has significantly advanced.
Deep neural networks are designed to mimic the human brain’s ability to process information and recognize patterns. By training these networks on vast amounts of data, they can learn intricate details that are crucial for identifying spoofed faces accurately.
The advantage of using deep learning in anti-spoofing is its capability to automatically extract relevant features from raw input data. This eliminates the need for manual feature engineering and allows the system to adapt and improve over time. As a result, video analytics systems equipped with deep learning models can achieve higher accuracy rates in detecting presentation attacks.
AI-Driven Liveness Detection
AI-driven liveness detection takes advantage of artificial intelligence algorithms to analyze liveness indicators and identify potential presentation attacks. By employing machine learning models, these systems can learn from extensive datasets containing various examples of live faces.
Through this process, AI algorithms can identify patterns associated with genuine facial movements that are absent or distorted in spoofed faces. These patterns may include subtle eye movements, skin texture changes caused by blood flow, or even micro-expressions that indicate liveliness.
The use of AI-driven liveness detection enhances the accuracy of anti-spoofing in video analytics systems. It enables them to differentiate between real individuals and imposters attempting to deceive the system with fake biometric data.
Conclusion
Congratulations! You’ve now gained a comprehensive understanding of anti-spoofing in video analytics. By exploring the fundamentals of anti-spoofing, computer vision, liveness detection, biometric verification techniques, advanced technologies, face recognition methods, image quality considerations, classifier fusion, and IntelliVision’s approach to fraud protection, you are equipped with the knowledge to enhance security and protect against fraudulent activities.
Now it’s time to put this knowledge into action. Consider implementing these anti-spoofing techniques in your own video analytics systems or recommending them to others in need of robust security measures. Stay up-to-date with the latest advancements in anti-spoofing technologies and continue to explore new solutions as they emerge. By doing so, you will not only safeguard your organization but also contribute to the broader fight against fraud and deception.
Remember, the world of video analytics is constantly evolving, and it’s up to us to stay one step ahead. Together, let’s create a safer and more secure future.
Frequently Asked Questions
What is anti-spoofing in video analytics?
Anti-spoofing in video analytics refers to the techniques and technologies used to detect and prevent fraudulent activities, such as spoofing or impersonation, in video-based security systems. It ensures that only legitimate users are granted access by verifying their liveness and authenticity.
How does computer vision contribute to anti-spoofing?
Computer vision plays a crucial role in anti-spoofing by analyzing visual data from videos or images to distinguish between real human faces and fake representations. By leveraging advanced algorithms, computer vision enables the detection of facial movements, texture variations, and other cues that indicate liveness.
What are biometric verification techniques?
Biometric verification techniques involve using unique physical or behavioral characteristics of individuals for identification purposes. In the context of anti-spoofing, biometrics like fingerprint recognition, iris scanning, voice recognition, and face recognition are employed to ensure the authenticity of users and prevent spoofing attacks.
How do advanced anti-spoofing technologies enhance security?
Advanced anti-spoofing technologies leverage sophisticated algorithms and machine learning models to detect increasingly sophisticated spoofing attempts. These technologies analyze various factors like facial dynamics, depth perception, thermal imaging, or even multispectral analysis to provide robust protection against spoofing attacks.
What is classifier fusion in anti-spoofing?
Classifier fusion combines multiple classification models or algorithms to improve the accuracy and reliability of anti-spoofing systems. By integrating the outputs of different classifiers into a unified decision-making process, classifier fusion enhances security measures by reducing false positives and increasing overall system performance.