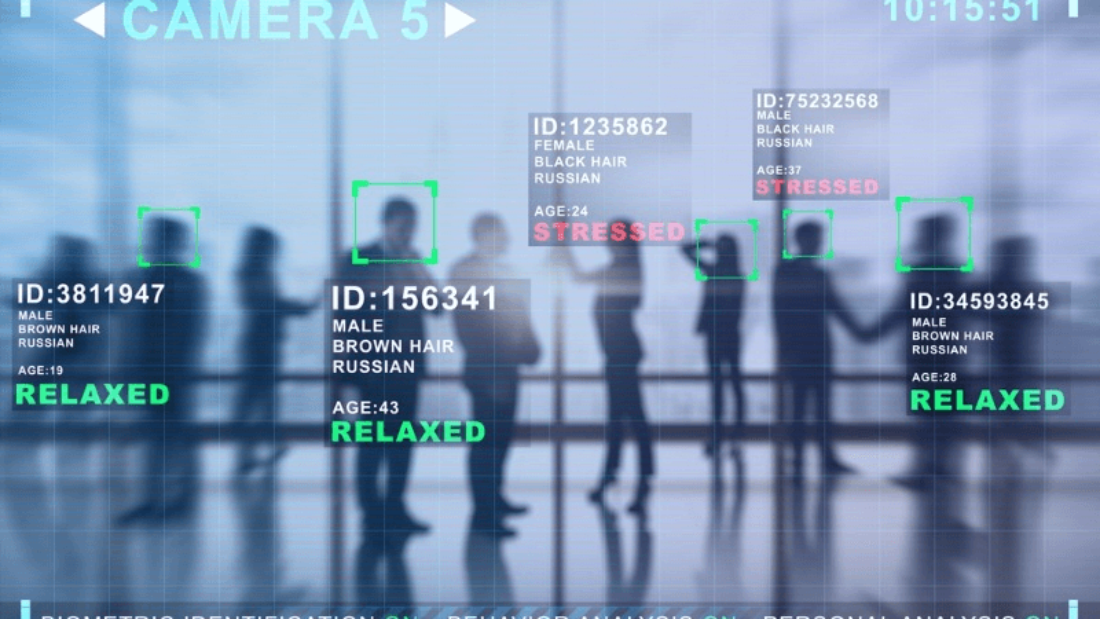
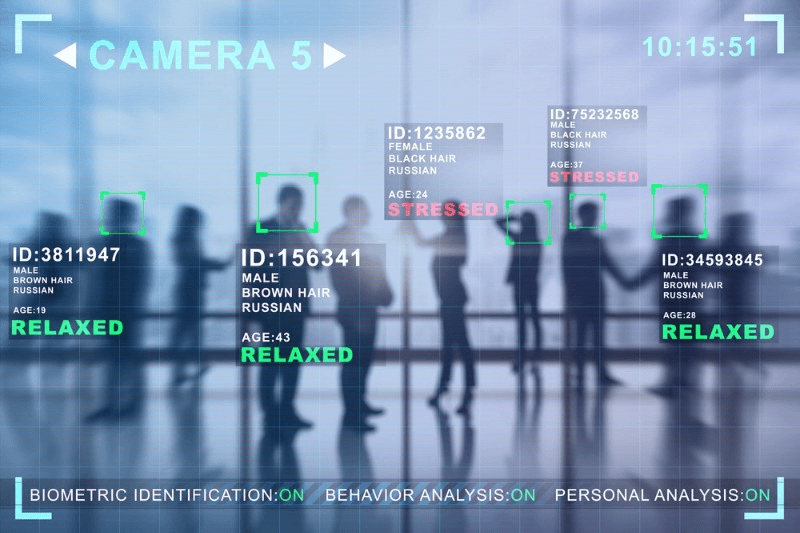
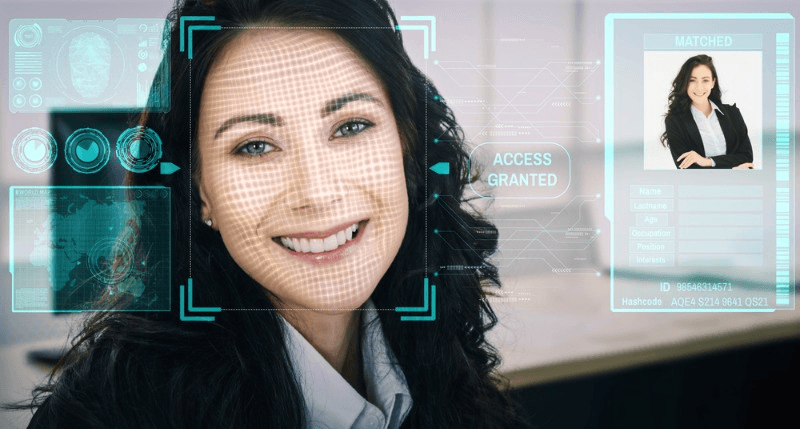
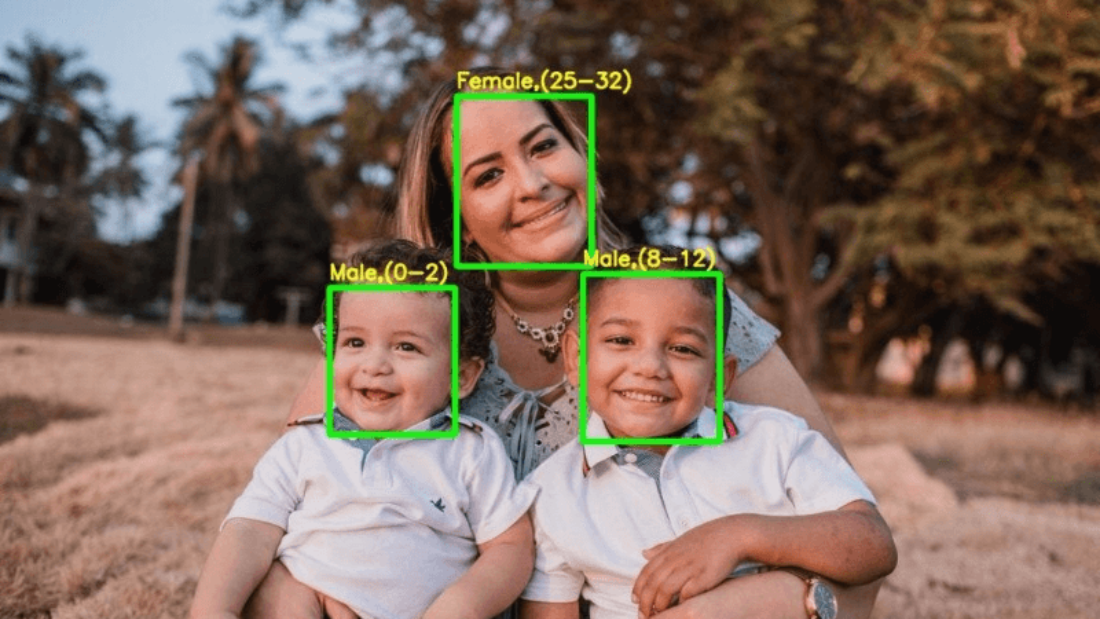
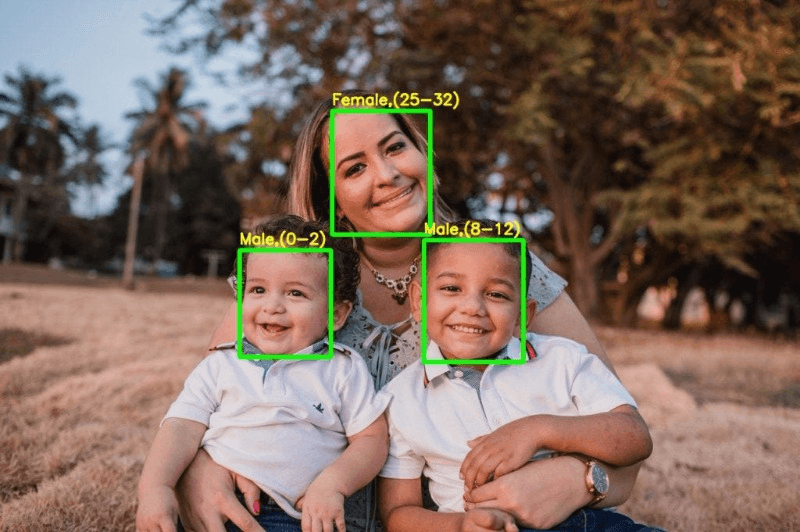
Are you concerned about the growing use of facial biometric tracking technology? Wondering how it works and what impact it may have on your privacy?
Facial recognition is a powerful biometric technology that identifies individuals based on their unique facial features. By analyzing factors such as eye distance, nose shape, and face contours, it creates a digital faceprint for identification purposes. With advancements in artificial intelligence (AI) and machine learning algorithms, facial recognition systems are becoming more accurate, faster, and scalable. Mobile devices and smart cameras now come equipped with this feature to provide seamless user experiences.
However, as with any technology that involves personal data collection, facial recognition raises concerns about privacy. From consent issues to potential misuse of biometric data by both private entities and governments, finding a balance between technological advancements and individual privacy rights is crucial.
Join us as we navigate through the world of facial biometric tracking – its benefits, challenges, and everything in between. Stay tuned for an insightful exploration of this fascinating technology!
Understanding Facial Recognition
History and Evolution
Facial recognition technology has come a long way since its inception in the 1960s. Back then, researchers began exploring pattern recognition techniques to identify faces. However, these early systems were limited in accuracy and reliability.
Over the years, advancements in computer vision, image processing, and artificial intelligence (AI) have significantly improved facial recognition technology. Today’s systems can perform complex tasks like emotion detection and age estimation with remarkable precision.
Core Techniques
Facial recognition employs various techniques to identify individuals. Feature-based methods analyze specific facial landmarks or characteristics to establish someone’s identity. These methods focus on key elements such as the shape of the eyes, nose, and mouth.
Template matching is another technique used in facial recognition systems. It involves comparing an individual’s face with pre-existing templates stored in a database to find a match.
Three-dimensional (3D) modeling is also utilized to capture additional depth information about a person’s face. This technique allows for more accurate identification by considering factors like facial contours and shape.
Deep learning algorithms play a crucial role in modern facial recognition technology. By using neural networks, these algorithms extract high-level features from images to achieve highly accurate identification results.
How It Works
Facial recognition systems follow a series of steps to identify or verify individuals based on their unique faceprints.
Firstly, cameras or video footage capture an individual’s face. This could be from CCTV cameras, smartphones, or any other device equipped with facial recognition capabilities.
Next, the system processes the captured image or video to extract various facial features such as the distance between eyes, shape of the nose, and texture of the skin. These features are then combined into a unique representation known as a faceprint.
The obtained faceprint is compared against a database of known faceprints for identification purposes. If there is a match within the database, it means that the system has successfully identified the individual.
In addition to identification, facial recognition systems can also be used for verification. In this scenario, an individual’s faceprint is compared against a specific template or set of templates to determine if they are who they claim to be.
Facial recognition technology has numerous applications across various industries. It is commonly used for security purposes in airports, government buildings, and other high-security areas. It can also be found in smartphones for unlocking devices using face recognition.
With its continuous advancements and increasing accuracy, facial recognition technology is transforming the way we interact with digital devices and enhancing security measures worldwide.
Applications Across Sectors
Security and Surveillance
Facial recognition technology has become a vital tool in the field of security and surveillance. With its ability to quickly identify individuals in crowded places, it significantly enhances public safety. Law enforcement agencies rely on facial recognition to identify suspects, prevent crime, and ensure the security of the public.
Imagine a scenario where law enforcement is tracking a known criminal in a busy city center. Facial biometric tracking enables real-time identification of the individual as they move through different areas, allowing authorities to stay one step ahead. This technology has proven invaluable in identifying criminals and preventing potential threats.
Retail and Marketing
In the retail sector, facial recognition technology offers valuable insights into customer behavior and preferences. By analyzing facial expressions, retailers can gain an understanding of how customers respond to products or store layouts. This information helps personalize shopping experiences, optimize store layouts, and track footfall patterns.
For example, retailers can use facial recognition cameras to analyze customer reactions as they browse through different sections of a store. By understanding which areas attract more attention or trigger positive emotions, retailers can strategically place popular products or design engaging displays that increase sales.
Furthermore, facial recognition enables targeted advertising based on demographic information. Advertisers can use this technology to display relevant advertisements to specific groups of people passing by digital billboards or screens. By tailoring ads based on age range or gender detected through facial biometric tracking, marketers can improve their advertising effectiveness.
Healthcare Innovations
Facial recognition technology holds great promise for various healthcare applications. It can revolutionize patient identification processes by providing accurate identification quickly and securely. In telemedicine settings, healthcare providers can use facial biometrics to verify patients’ identities remotely before consultations.
This technology has significant potential for monitoring vital signs non-invasively using facial expressions and skin color changes associated with blood flow variations. For instance, researchers have developed algorithms that utilize facial biometrics to detect changes in heart rate, blood pressure, and even stress levels.
Facial recognition can also assist in diagnosing genetic disorders by analyzing facial features and comparing them to known genetic conditions. This technology could potentially identify rare genetic disorders that might otherwise go undiagnosed for years.
Moreover, healthcare facilities rely on facial recognition for access control in secure areas. By using biometric data such as facial features or iris patterns, hospitals can ensure that only authorized personnel have access to sensitive areas like operating rooms or medication storage.
Software and Vendors Overview
Market Leaders
Several companies dominate the facial recognition market, including Amazon Web Services (AWS), Microsoft, NEC Corporation, and Face++. These market leaders have established themselves as key players in the industry by offering robust facial recognition solutions with high accuracy rates and advanced features. Their continuous competition drives innovation and pushes the boundaries of facial recognition technology.
AWS in Facial Recognition
Amazon Web Services (AWS) is a prominent player in the field of facial recognition. Through its Rekognition platform, AWS provides a comprehensive suite of facial recognition services. The platform offers various capabilities such as face detection, analysis, identification, and verification. With its wide adoption across industries, AWS Rekognition is utilized for diverse applications ranging from security to user authentication and content moderation.
One notable advantage of AWS Rekognition is its scalability. It allows businesses to easily scale their facial recognition infrastructure based on their needs without compromising performance or accuracy. This flexibility makes it an attractive choice for organizations of all sizes.
Churchix’s Niche
While many vendors cater to a broad range of industries, Churchix focuses specifically on providing facial recognition software tailored for religious settings. Designed to identify individuals within churches, this specialized software helps streamline attendance management processes while enhancing security measures.
Churchix offers several features that address the unique requirements of religious institutions. For example, it enables automatic face detection during live video streams within church premises. This capability can significantly improve efficiency by automating attendance tracking during services or events.
Integration with existing church management systems is another valuable aspect offered by Churchix. By seamlessly integrating with these systems, the software simplifies administrative tasks and ensures accurate record-keeping across different platforms.
Moreover, Churchix’s facial recognition technology enhances overall security within religious establishments. It can help identify individuals who may pose a threat or are prohibited from entering certain areas due to safety concerns.
Advantages vs Disadvantages
Efficiency Gains
Facial biometric tracking offers numerous advantages that contribute to increased efficiency in various areas. One of the key benefits is the automation of tasks such as attendance management, access control, and identity verification. By using facial recognition technology, businesses and organizations can streamline these processes, eliminating the need for manual intervention. This not only saves time but also reduces administrative burdens.
Imagine a scenario where employees no longer have to swipe cards or sign attendance sheets. Instead, they simply walk into their workplace, and their faces are automatically recognized by the system. This seamless process not only speeds up entry but also eliminates the possibility of human error or fraudulent activities like buddy punching.
Furthermore, facial biometric tracking allows for more effective resource allocation. With automated systems in place, companies can redirect human resources from repetitive administrative tasks to more value-added activities. Employees can focus on core responsibilities instead of spending hours on manual data entry or verifying identities.
Ethical Considerations
As with any emerging technology, facial recognition raises ethical concerns that must be carefully addressed. Privacy is one of the primary considerations. Individuals have a right to know how their personal data is collected and used, necessitating transparency in data collection practices.
Consent is another crucial aspect that needs attention. Users should have control over whether their facial biometric information is collected and stored by organizations. Clear consent mechanisms should be put in place to ensure individuals’ rights are respected.
Bias within facial recognition algorithms also poses ethical challenges. These systems may exhibit racial or gender bias due to biased training data or flawed algorithms. It is essential for developers and policymakers to work together to minimize these biases and ensure fair treatment for all individuals.
Addressing these ethical considerations requires collaboration between technology developers, policymakers, and society as a whole. Regulations must be established to protect individuals’ privacy rights while encouraging innovation in facial recognition technology. A balance must be struck to harness the benefits of this technology while mitigating potential risks.
Misuse Risks
While facial biometric tracking offers significant advantages, there are also risks associated with its misuse. One concern is the potential for unauthorized surveillance or profiling. Governments, law enforcement agencies, or malicious actors could exploit these systems for purposes beyond their intended use, infringing on individuals’ privacy and civil liberties.
To prevent such misuse, robust regulations and safeguards are necessary. Stricter controls should be implemented to govern the collection, storage, and usage of facial biometric data. Compliance audits and oversight mechanisms can help ensure that organizations adhere to ethical standards and protect individual rights.
Public awareness and education about facial recognition technology are crucial in preventing its misuse. By understanding the risks involved, individuals can make informed decisions about how their personal data is used and take steps to protect their privacy.
Legal and Regulatory Landscape
US Privacy Concerns
In the United States, there is a growing concern about the impact of facial recognition technology on privacy rights. Advocacy groups argue that current regulations fail to adequately address the risks associated with facial biometric tracking. They believe that individuals’ rights in the digital age need to be safeguarded through comprehensive privacy legislation.
These concerns arise from the potential misuse of facial recognition data by both private entities and government agencies. The fear is that without proper regulations, personal information collected through facial biometric tracking could be used for surveillance purposes or discriminatory practices. This raises questions about individual autonomy and the protection of personal privacy.
To address these concerns, several states have taken steps towards regulating facial recognition technology. For example, Illinois has enacted the Biometric Information Privacy Act (BIPA), which requires companies to obtain consent before collecting biometric data, including facial scans. Other states are also considering similar legislation to protect their citizens’ privacy.
National Schemes
Some countries have implemented national facial recognition schemes for various purposes such as border control or citizen identification. These schemes aim to enhance security, improve public services, or streamline administrative processes. However, they also raise concerns about mass surveillance and potential infringements on civil liberties.
China’s Social Credit System is one prominent example of a national scheme that utilizes facial recognition technology extensively. While it aims to promote social trust and integrity, critics argue that it poses a significant threat to individual privacy and freedom. The system assigns scores based on citizens’ behavior and can result in rewards or penalties accordingly.
The implementation of such schemes requires careful consideration of ethical implications and ensuring adequate safeguards against abuse or misuse of personal data. Striking a balance between security measures and protecting civil liberties remains a challenge for governments worldwide.
Commercial Use Regulations
Governments worldwide are recognizing the need for regulations governing the commercial use of facial recognition technology. These regulations focus on ensuring transparency, obtaining consent, protecting personal data, and preventing discriminatory practices.
For instance, the European Union’s General Data Protection Regulation (GDPR) sets strict guidelines for the collection and processing of biometric data, including facial recognition. It requires businesses to obtain explicit consent from individuals before using their facial biometrics and provides individuals with the right to access and delete their data.
In the United States, federal law has yet to provide comprehensive regulations specifically addressing commercial use of facial recognition technology. However, some companies voluntarily adopt guidelines like those outlined in the Privacy Principles for Facial Recognition Technology released by the Department of Commerce’s National Telecommunications and Information Administration.
Compliance with these regulations is crucial for businesses utilizing facial recognition technology in their operations. By adhering to transparency requirements, obtaining consent from individuals whose biometric data is collected, and implementing safeguards against discrimination or misuse of personal information, companies can build trust with their customers while ensuring legal compliance.
The Future of Facial Recognition
Emerging Trends
Emerging trends in facial recognition are shaping the future of this technology. One such trend is emotion detection, where facial recognition algorithms can analyze facial expressions to determine a person’s emotions. This has applications in various fields, including marketing and customer experience analysis.
Another significant trend is mask detection, which gained prominence during the COVID-19 pandemic. Facial recognition systems have been adapted to identify individuals wearing masks, ensuring security protocols are upheld while maintaining public health measures.
Facial recognition is also being integrated with other technologies like augmented reality (AR) and virtual reality (VR). This integration opens up new possibilities for immersive experiences, whether it be in gaming or training simulations. By combining facial recognition with AR/VR, developers can create more realistic and interactive virtual environments.
Ongoing research and development continue to push the boundaries of facial recognition applications. As computer vision algorithms advance, the accuracy and speed of face tracking technology improve, enabling real-time identification even in crowded or dynamic environments.
Innovative Use Cases
Facial recognition technology finds innovative use cases across various industries. In airport security, it helps streamline processes by automating passenger identity verification at checkpoints. This not only enhances security but also enables seamless travel experiences for passengers.
In the banking sector, facial recognition ensures secure financial transactions by verifying the user’s identity through their unique facial features. This helps prevent fraud and unauthorized access to accounts while providing a convenient authentication method for customers.
Education is another area where facial recognition has proven beneficial. It allows schools to create personalized learning environments by identifying students’ emotions and engagement levels during classes. Educators can then adapt their teaching methods accordingly to optimize student learning outcomes.
Entertainment industries are leveraging facial recognition technology to enhance gaming experiences. By capturing players’ expressions and movements using cameras or sensors, games can respond dynamically in real-time based on the player’s reactions—creating an immersive gameplay experience that goes beyond traditional controls.
The versatility of facial recognition opens up possibilities for transformative applications across industries. Whether it’s improving security, personalizing experiences, or enhancing entertainment, this technology has the potential to revolutionize numerous sectors.
Hybridized Solutions
To further enhance accuracy and security, facial recognition is often combined with other biometric modalities such as fingerprint or iris recognition. These hybridized solutions offer more robust identification and verification capabilities compared to using a single biometric modality.
In high-security environments or scenarios where a single biometric modality may not be sufficient, hybridized solutions provide an added layer of protection. By combining multiple biometrics, the system can achieve higher confidence levels in identifying individuals accurately.
For instance, in access control systems for sensitive areas like government facilities or research laboratories, a combination of facial recognition and fingerprint scanning ensures only authorized personnel gain entry. This multimodal approach minimizes the risk of unauthorized access and enhances overall security measures.
Biometric Data Protection
Legal Framework Strengthening
Governments worldwide are taking steps to strengthen legal frameworks that regulate facial recognition technology. These efforts involve the development of clear guidelines for the collection, storage, usage, and sharing of biometric data. The aim is to strike a balance between protecting individual privacy rights and enabling responsible deployment of facial recognition systems.
Stricter regulations are being put in place to safeguard sensitive biometric information. By defining specific rules and requirements, governments can ensure that organizations handling such data adhere to strict standards. This helps prevent unauthorized access or misuse of biometric identification.
Protection Landscape
Protecting facial biometric data involves implementing robust security measures throughout its lifecycle. Encryption plays a crucial role in safeguarding this sensitive information from unauthorized access during transmission or storage. Secure data storage practices, including strong access controls and authentication mechanisms, further enhance protection.
Regular audits and vulnerability assessments help identify potential security risks and vulnerabilities within facial recognition systems. By conducting these assessments, organizations can proactively address any weaknesses in their infrastructure or processes before they can be exploited by malicious actors.
Collaboration between technology providers, cybersecurity experts, and regulatory bodies is essential for maintaining a strong protection landscape for facial biometric tracking. This collaboration ensures that best practices are shared across industries and that emerging threats are promptly addressed through proactive measures.
Bans and Restrictions
In response to concerns about privacy and potential abuses, some cities or regions have implemented bans or restrictions on the use of facial recognition technology by government entities or private businesses. These measures aim to strike a balance between reaping the benefits of facial recognition while addressing legitimate privacy concerns.
By imposing limitations on when and how facial recognition can be used, governments seek to prevent unwarranted surveillance or invasion of individuals’ privacy rights. However, it is important to note that outright bans may hinder the development of beneficial applications of this technology in areas such as law enforcement or public safety.
Finding the right balance between leveraging the advantages of facial recognition and respecting privacy considerations remains a key challenge. Striking this balance requires ongoing dialogue between stakeholders, including technology developers, policymakers, civil rights organizations, and the general public.
Challenges and Solutions
Technical Challenges
Facial recognition technology has made significant advancements in recent years, but it still faces several technical challenges. One of the primary obstacles is dealing with variations in lighting conditions. Different lighting environments can affect the quality of facial images, making accurate recognition more difficult. Pose changes and occlusions, such as wearing glasses or hats, can further complicate the process.
To overcome these challenges, researchers and developers are continuously working on advanced algorithms that can adapt to different lighting conditions and handle pose changes effectively. Improvements in hardware capabilities also play a crucial role in enhancing facial biometric tracking accuracy. Ongoing research and development efforts contribute to refining these algorithms and hardware components, making facial recognition technology more robust and reliable.
The field of computer vision and artificial intelligence (AI) is constantly evolving, which helps address many technical limitations faced by facial recognition technology. Advancements in computer vision algorithms enable better feature extraction from images and improve overall accuracy. AI-powered systems can learn from vast amounts of data to enhance their ability to recognize faces accurately.
Strengthening Legal Systems
To ensure responsible use of facial recognition technology, it is essential to strengthen legal systems surrounding its implementation. This involves enacting comprehensive privacy laws that specifically address the use of biometric data like facial images. Existing regulations need to be updated to keep up with technological advancements while providing adequate protection for individuals’ privacy rights.
Collaboration between governments, experts, industry stakeholders, and civil society organizations is crucial in developing effective legal frameworks for facial biometric tracking projects and services. By involving diverse perspectives in the decision-making process, policymakers can strike a balance between public safety concerns and protecting individual privacy rights.
Establishing clear enforcement mechanisms within legal systems is equally important. These mechanisms ensure that any misuse or abuse of facial recognition technology is appropriately addressed through penalties or other consequences. Effective enforcement not only acts as a deterrent but also builds trust among the public, encouraging responsible use of the technology.
Addressing Privacy Rights
Privacy is a fundamental concern. To address privacy rights adequately, transparency in data collection and usage practices is essential. Individuals should have clear information about how their facial biometric data is collected, stored, and used. Service providers must be transparent in their practices and obtain informed consent from individuals before collecting their data.
Furthermore, individuals should have control over their facial biometric data. This includes the right to access, correct, or delete their information whenever they choose. Service providers need to establish mechanisms that allow individuals to exercise these rights easily and effectively.
Privacy-enhancing technologies can also play a significant role in protecting individuals’ identities while still enabling useful analysis through facial recognition technology. Differential privacy is one such technique that adds noise to the collected data, making it challenging to identify specific individuals while preserving overall accuracy for analysis purposes.
Conclusion
In conclusion, facial biometric tracking is a powerful technology that has the potential to revolutionize various industries. From enhancing security measures to improving customer experiences, the applications of facial recognition are vast and diverse. However, it is important to consider both the advantages and disadvantages of this technology, as well as the legal and regulatory landscape surrounding it.
As we move forward, it is crucial to prioritize the protection of biometric data and address the challenges that arise. This includes implementing robust security measures, complying with privacy regulations, and ensuring transparency in the use of facial recognition technology. By doing so, we can harness the benefits of facial biometric tracking while mitigating potential risks.
In a world where technology continues to advance at a rapid pace, it is essential for businesses and individuals alike to stay informed about emerging trends like facial recognition. By understanding its capabilities and limitations, we can make informed decisions and actively participate in shaping its future. So, embrace the possibilities that facial biometric tracking offers, but do so responsibly and ethically.
Frequently Asked Questions
Can facial biometric tracking be used for surveillance purposes?
Yes, facial biometric tracking can be used for surveillance purposes. It allows authorities to monitor individuals in public spaces and track their movements using facial recognition technology.
How does facial recognition software work?
Facial recognition software analyzes unique facial features such as the distance between eyes, shape of the nose, and jawline to create a digital representation of a person’s face. This representation is then compared to a database of known faces to identify or verify an individual.
What are the advantages of facial biometric tracking?
Facial biometric tracking offers several advantages. It provides enhanced security by accurately identifying individuals, helps streamline processes like access control and attendance management, and improves customer experiences through personalized services.
Are there any disadvantages to facial recognition technology?
Yes, there are some disadvantages to consider. Facial recognition technology raises concerns about privacy invasion and potential misuse of personal data. It can also result in false positives or negatives, leading to errors in identification.
How is biometric data protected in facial recognition systems?
Biometric data in facial recognition systems should be securely stored using encryption methods. Access controls and strict user permissions should be implemented to prevent unauthorized access. Compliance with relevant data protection regulations ensures proper handling and storage of biometric information.