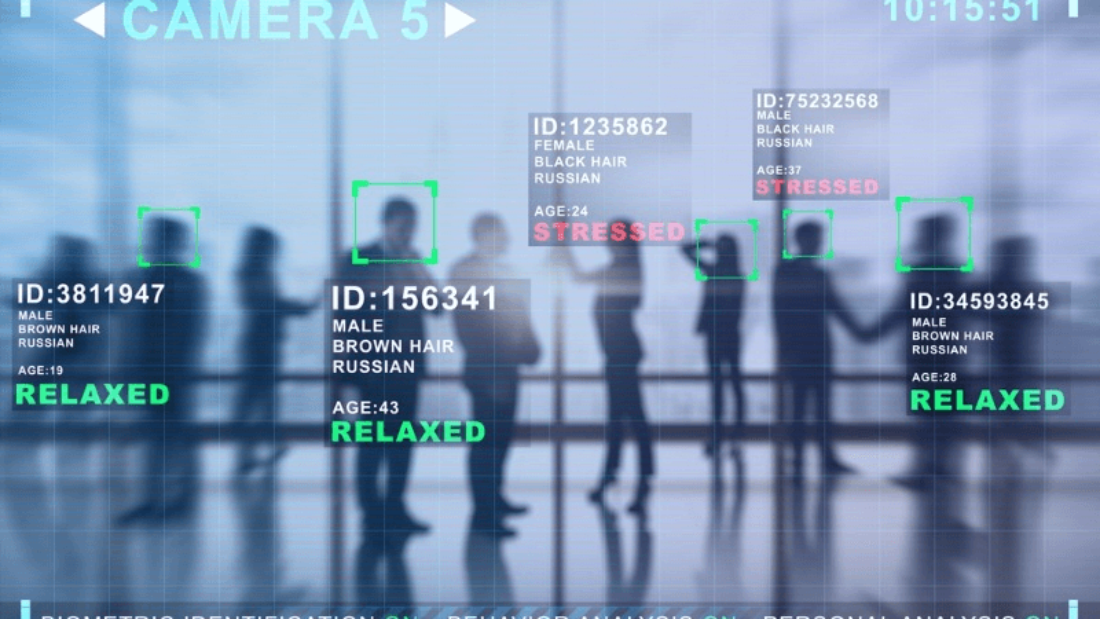
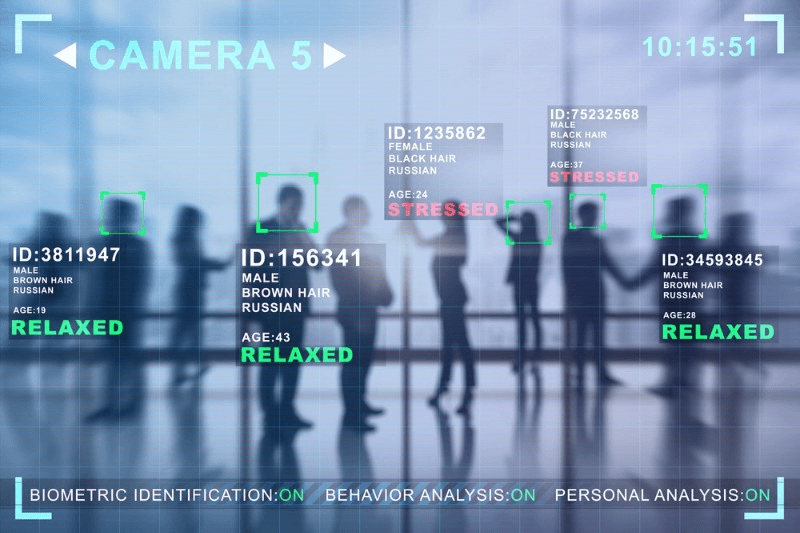
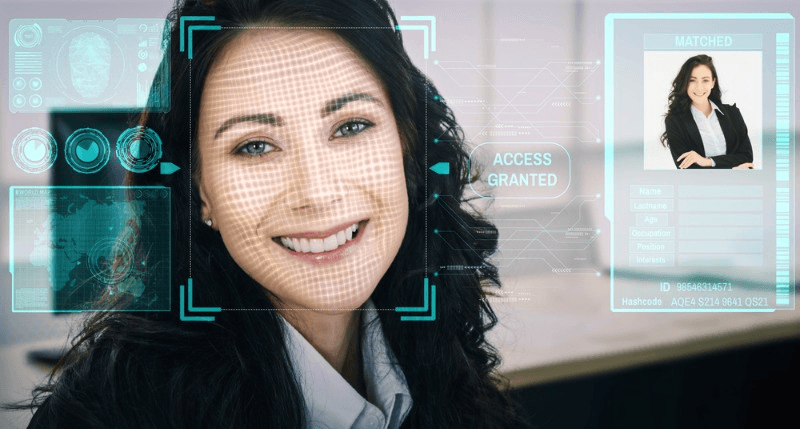
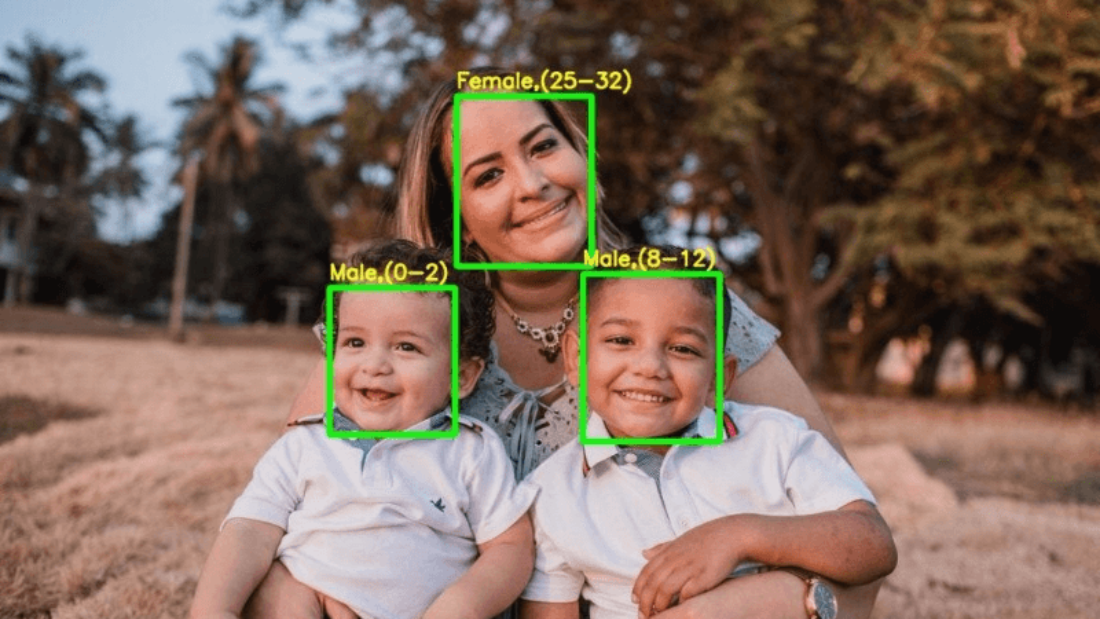
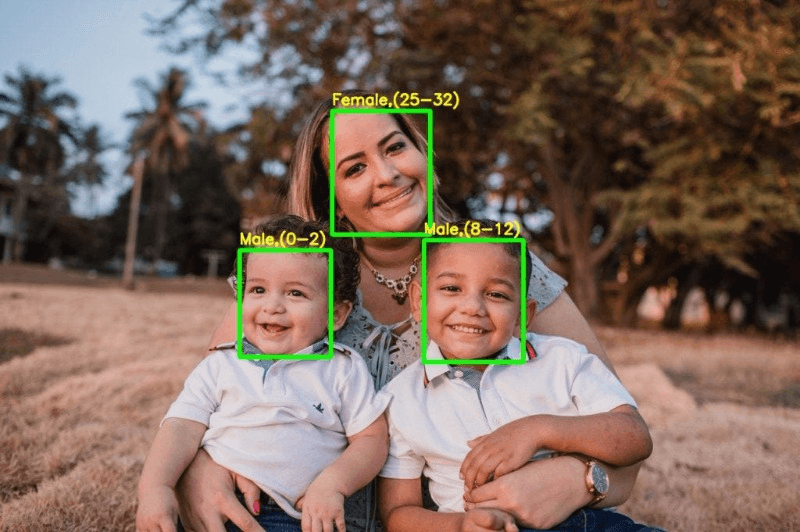
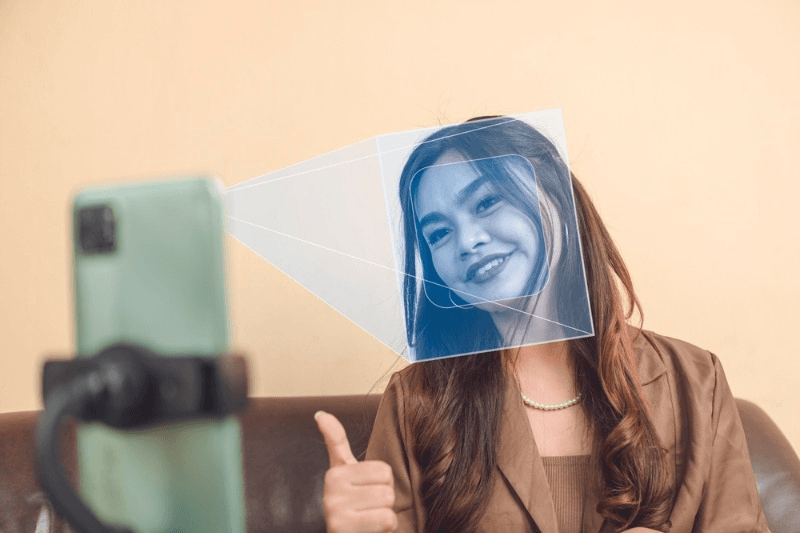
Are you tired of constantly forgetting people’s names or struggling to recognize familiar faces? Imagine a world where technology could effortlessly track and identify individuals based on their facial features. Well, that world is not too far away. Facial identity tracking, a cutting-edge technology powered by advanced algorithms, is revolutionizing the way we perceive and interact with human faces.
Facial identity tracking systems utilize cameras or sensors to capture facial images or videos, which are then analyzed using complex algorithms. These algorithms analyze various facial features such as the distance between eyes and the shape of the nose to create unique patterns for each individual. By comparing these patterns with a database of known faces, these systems can accurately determine someone’s identity in an instant.
From enhancing security measures to enabling personalized customer experiences, facial identity tracking has an array of potential applications across industries.
Technological Advancements in Facial Recognition
Techniques for Identification
Facial identity tracking has seen significant advancements in recent years, thanks to various techniques used for identification. Two commonly employed methods are geometric-based and feature-based approaches.
Geometric-based methods involve measuring specific points on the face to create a unique template for each individual. These points, known as landmarks, include features such as the distance between the eyes, the width of the nose, and the shape of the jawline. By analyzing these measurements, facial recognition systems can accurately identify individuals based on their distinctive facial geometry.
On the other hand, feature-based methods focus on extracting distinctive features from the face to identify individuals. These features can include texture or shape patterns present on different regions of the face. By analyzing these unique characteristics, facial recognition algorithms can match faces against a database and determine an individual’s identity.
Integration with Other Technologies
Facial identity tracking is not limited to standalone applications but can also be integrated with other technologies to enhance its functionality. One common integration is with surveillance cameras deployed in public spaces. By combining facial recognition technology with surveillance cameras, real-time monitoring and identification of individuals can be achieved. This integration has proven invaluable in enhancing security measures and aiding law enforcement agencies in identifying potential threats or criminals.
Furthermore, facial identity tracking can be seamlessly integrated with access control systems to provide secure authentication for restricted areas. Instead of relying solely on traditional methods like keycards or passwords, access control systems equipped with facial recognition capabilities offer a more convenient and reliable solution. Individuals can gain access by simply presenting their face to a camera that verifies their identity within seconds.
Future Trends
As technology continues to advance at a rapid pace, the future of facial identity tracking holds immense promise for further improvements in accuracy and speed.
One area expected to drive advancement is deep learning algorithms. By analyzing multiple layers of facial data using neural networks, deep learning algorithms have shown remarkable potential in enhancing the recognition capabilities of facial recognition systems. This approach allows for more accurate identification, even in challenging scenarios such as low lighting conditions or partial occlusions.
Moreover, with the increasing prevalence of mobile devices, facial recognition is likely to become more integrated into our everyday lives. Mobile applications utilizing facial recognition technology can offer enhanced security features and personalized experiences. For instance, unlocking smartphones using facial recognition has already become a common feature, and we can expect its usage to expand further into various applications like secure payments and augmented reality experiences.
Applications Across Sectors
Security Services
Facial identity tracking technology has found widespread applications in the security services sector. It plays a crucial role in enhancing surveillance and threat detection capabilities. By quickly identifying potential threats or suspects in crowded areas, facial recognition systems enable security personnel to take immediate action.
Integrating facial identity tracking with alarm systems further enhances security measures. Unauthorized access can be instantly detected, triggering alarms and notifying security personnel. This real-time alert system ensures that any potential breach is addressed promptly, minimizing risks.
Retail Stores
Retail stores are increasingly adopting facial identity tracking to improve customer experience and prevent theft. This technology allows for personalized advertising and targeted marketing based on customer demographics. By analyzing facial features, retailers can tailor their advertisements to match individual preferences, creating a more engaging shopping experience.
Facial recognition also plays a vital role in preventing theft within retail stores. Known shoplifters or individuals involved in fraudulent activities can be identified through the system’s database of flagged individuals. This proactive approach not only helps deter potential criminals but also creates a safer environment for both customers and staff.
Healthcare Deployment
The deployment of facial identity tracking technology holds significant promise within the healthcare sector. One key application is patient identification and monitoring, where accurate identification plays a critical role in ensuring patient safety and preventing medical errors.
By using facial recognition systems to verify patients’ identities, healthcare providers can eliminate the risk of misidentification during admission or treatment procedures. This helps ensure that patients receive appropriate care tailored specifically to their needs.
Facial identity tracking has the potential for remote patient monitoring by analyzing changes in facial expressions or vital signs captured via cameras or wearable devices. This could be especially beneficial for patients with chronic conditions who require continuous monitoring but may not always have direct access to healthcare professionals.
Ethical and Legal Considerations
Privacy Rights Impact
Facial identity tracking, while offering various benefits, raises concerns about privacy rights and the collection of personal data without consent. The technology involves capturing and storing facial images, which can make individuals feel that their privacy is being violated. It is important to strike a balance between security needs and privacy rights when implementing facial identity tracking systems.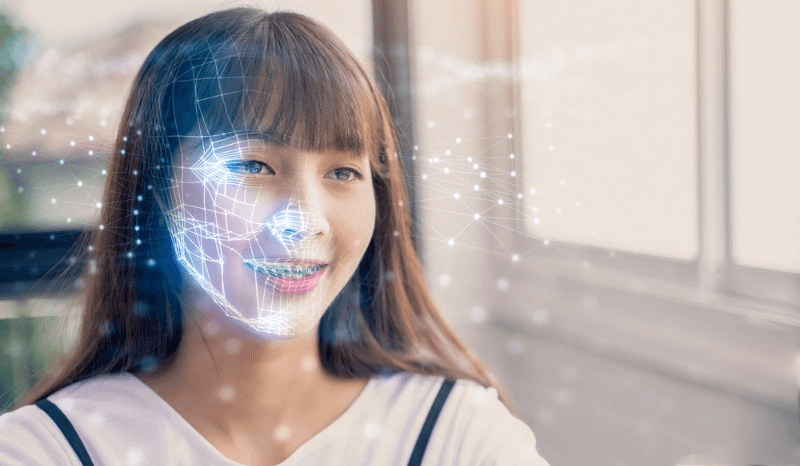
Data Protection Regulations
Data protection regulations play a crucial role in governing the use of facial identity tracking technology. Laws such as the General Data Protection Regulation (GDPR) in Europe aim to protect individuals’ personal data from misuse or unauthorized access. Compliance with these regulations ensures that facial recognition systems adhere to strict privacy standards, safeguarding individuals’ information.
Bans and Controversies
The ethical implications surrounding facial identity tracking have led to bans or restrictions in certain jurisdictions. Concerns over privacy and civil liberties have prompted some cities to implement bans on government use of the technology. These bans are often rooted in fears of potential bias and infringement on individual rights. Moreover, controversies surrounding the accuracy and potential misuse of facial recognition have fueled debates about its ethical implications.
While facial identity tracking has proven beneficial across various sectors, it is imperative to address the ethical and legal considerations associated with its implementation.
One major concern revolves around privacy rights. With facial recognition technology, there is a potential risk of personal data being collected without consent. Individuals may feel uneasy knowing that their facial images are being captured and stored without their knowledge or permission. Striking a balance between security needs and privacy rights becomes paramount to ensure that individuals’ fundamental right to privacy is respected.
To mitigate these concerns, data protection regulations come into play. Laws like GDPR provide guidelines for protecting personal data from misuse or unauthorized access. Adhering to these regulations ensures that facial recognition systems meet strict standards. By complying with such laws, organizations can demonstrate their commitment to safeguarding individuals’ privacy.
Despite the potential benefits of facial identity tracking, controversies and bans have emerged due to ethical concerns. Some cities have implemented bans on government use of the technology, citing fears of bias and infringement on civil liberties. The accuracy and potential misuse of facial recognition systems have also sparked debates about their ethical implications. These controversies highlight the need for careful consideration and regulation when implementing facial identity tracking technology.
Demographic and Emotion Analysis
Accuracy and Bias
Facial identity tracking systems have made significant advancements in recent years, but their accuracy is not without limitations. These systems utilize complex algorithms to analyze facial features and match them with known identities. However, factors such as lighting conditions, facial expressions, and image quality can affect the accuracy of recognition.
It is important to note that some facial identity tracking algorithms have exhibited biases towards certain demographics. This bias can result from a lack of diverse training data or inherent flaws in the algorithm itself. For example, studies have shown that these systems may be less accurate when identifying individuals with darker skin tones or women compared to lighter-skinned individuals or men.
Efforts are being made to improve the fairness and reduce biases in facial identity tracking technology. Researchers are working on developing more inclusive datasets that represent a wide range of demographics. Algorithmic advancements are being explored to ensure equal accuracy across different groups. The goal is to create systems that are unbiased and treat all individuals fairly regardless of their demographic characteristics.
Emotion Recognition
Beyond identifying individuals, facial identity tracking technology can also be used for emotion recognition. By analyzing facial expressions, these systems can determine emotions such as happiness, sadness, or anger. This capability has found applications in various fields including market research, mental health assessment, and human-computer interaction.
In market research, emotion recognition can provide valuable insights into customer satisfaction. By analyzing customers’ emotional responses during product trials or advertisements, companies can gain a deeper understanding of consumer preferences and tailor their offerings accordingly.
In mental health assessment, emotion recognition technology can assist healthcare professionals in evaluating patients’ emotional well-being. It can help detect signs of depression or anxiety by analyzing subtle changes in facial expressions over time. This information enables healthcare providers to intervene early and provide appropriate support.
Furthermore, emotion recognition plays a crucial role in enhancing human-computer interaction. By detecting users’ emotions, computers and virtual assistants can respond in a more personalized manner. For example, if a user appears frustrated or confused, the system can adapt its responses to provide clearer instructions or additional assistance.
Anti-Recognition Systems
As concerns about privacy and surveillance grow, there has been an emergence of anti-recognition systems designed to counter facial identity tracking. These systems employ various techniques to make it difficult for algorithms to identify individuals accurately.
One approach is the use of makeup, accessories, or specialized patterns on clothing that confuse facial recognition algorithms. By strategically applying certain patterns or wearing specific accessories, individuals can alter their appearance enough to evade detection by these systems.
Anti-recognition measures have gained attention as a means to protect privacy in public spaces where facial identity tracking may be prevalent. They offer individuals the ability to control how their personal information is collected and used without completely compromising their freedom of movement.
Biometric Data Protection
Regulations Overview
Facial identity tracking has become a powerful technology that is being used in various industries. However, its implementation is subject to regulations that vary across different jurisdictions. Countries and regions have recognized the need to address concerns related to privacy, data protection, and ethical use of this technology.
To ensure compliance and responsible use, organizations must understand the regulations specific to their location. For example, the European Union’s General Data Protection Regulation (GDPR) places strict guidelines on the collection and processing of biometric data, including facial recognition information. It requires organizations to obtain explicit consent from individuals before collecting their biometric information and outlines strict security measures for its storage and handling.
Similarly, other countries such as the United States have introduced legislation addressing facial recognition technology. For instance, the California Consumer Privacy Act (CCPA) grants consumers certain rights regarding their personal information collected by businesses operating in California. This includes biometric data such as facial recognition information.
Understanding these regulations is crucial for organizations implementing facial recognition systems. By adhering to these laws, organizations can protect individuals’ privacy rights while harnessing the benefits of facial identity tracking.
Commercial Use Landscape
The commercial use of facial identity tracking has expanded rapidly across various industries. Companies are leveraging this technology for a wide range of applications including retail, banking, transportation, and entertainment.
In retail settings, facial recognition enables personalized marketing experiences by identifying customers’ preferences and tailoring offers accordingly. Banks utilize this technology for customer identification purposes to enhance security measures and prevent fraud attempts. Transportation sectors have also adopted facial recognition systems for tasks like automated boarding processes or enhancing passenger safety through real-time monitoring.
The commercial landscape continues to evolve as businesses explore new applications for facial recognition. For instance, some theme parks now use facial identity tracking as an alternative to traditional tickets or access cards.
By embracing this technology responsibly within legal boundaries, companies can improve operational efficiency while enhancing customer experiences.
Federal Legislation Impact
Federal legislation plays a significant role in shaping the use of facial identity tracking at a national level. Governments may enact laws that regulate the deployment of this technology by public agencies or private entities.
The aim of such legislation is to strike a balance between security needs and protecting individual rights. It ensures that facial recognition systems are used responsibly and ethically, without compromising personal privacy.
For example, the U.S. federal government has introduced bills like the Facial Recognition and Biometric Technology Moratorium Act, which aims to halt certain uses of facial recognition technology until proper regulations are in place. This demonstrates the commitment to ensuring transparent and accountable usage of biometric data.
Global Perspectives and Regulations
Commonwealth Guidelines
Commonwealth countries have taken proactive steps to address the ethical use of facial identity tracking technology. In response to the growing concerns surrounding privacy and data protection, these countries have developed guidelines that emphasize transparency, accountability, and respect for privacy rights.
The Commonwealth guidelines provide a comprehensive framework for organizations to ensure responsible and lawful implementation of facial recognition systems. By adhering to these guidelines, organizations can instill public trust by demonstrating their commitment to protecting individual privacy while leveraging the benefits of this technology.
Transparency is a key principle highlighted in the Commonwealth guidelines. Organizations are encouraged to be open about their use of facial identity tracking technology, providing clear information on how it is employed and what purposes it serves. This transparency helps individuals understand how their data is being used and allows them to make informed decisions about their participation.
Accountability is another essential aspect emphasized in the guidelines. Organizations are expected to take responsibility for ensuring that facial recognition systems are used appropriately and within legal boundaries. This includes implementing safeguards against misuse or unauthorized access, as well as regularly assessing the accuracy and reliability of the technology.
Respect for privacy rights is at the core of these guidelines. Organizations must prioritize protecting individuals’ personal information by implementing robust security measures and obtaining explicit consent when collecting biometric data. They should establish mechanisms for individuals to exercise their rights regarding access, correction, deletion, or restriction of their data.
European Union Standards
The European Union has also established stringent standards and regulations pertaining to facial identity tracking in order to safeguard individuals’ privacy and personal data. The General Data Protection Regulation (GDPR) sets forth comprehensive guidelines for the collection, processing, storage, and transfer of personal data within EU member states.
Compliance with GDPR standards is crucial for organizations operating within the European Union. They must ensure that any facial recognition systems they utilize adhere to strict requirements regarding consent, purpose limitation, data minimization, and data retention. Organizations are also obligated to implement appropriate technical and organizational measures to protect personal data from unauthorized access or disclosure.
The GDPR grants individuals a range of rights, including the right to be informed about the collection and use of their personal data, the right to access their data, and the right to request its deletion or rectification. These rights empower individuals with control over their own information and enable them to exercise greater agency.
Challenges in Face Tracking Systems
Ineffectiveness in Law Enforcement
Facial identity tracking has been a subject of criticism due to its effectiveness, or lack thereof, in law enforcement scenarios. While the technology holds promise for identifying individuals based on their facial features, there are several factors that can hinder accurate identification.
One major challenge is the quality of the images used for tracking. Factors such as poor lighting conditions, low-resolution cameras, and variations in camera angles can result in blurry or distorted images. This can make it difficult for face tracking systems to accurately match an individual’s face with a database of known identities.
Moreover, variations in appearance pose another obstacle. People may change their hairstyles, grow facial hair, wear glasses or hats, or undergo plastic surgery. These changes can significantly alter their facial features and make it harder for face tracking systems to recognize them accurately.
Limitations within databases can also impact the accuracy of facial identity tracking. Databases may not contain comprehensive information about all individuals, especially those who have not come into contact with law enforcement before. This limited data availability can lead to false identifications and wrongful arrests if solely relying on facial recognition technology.
Critics argue that relying solely on facial recognition technology without considering other forms of evidence can be problematic. They highlight cases where innocent individuals have been mistakenly identified as criminals based solely on flawed face tracking results. These false identifications not only violate people’s rights but also undermine public trust in the justice system.
Privacy Violations
Another concern surrounding facial identity tracking is the potential violation of privacy when used without proper safeguards. The collection and storage of personal biometric data raise significant privacy concerns if not handled appropriately.
Unauthorized access to facial recognition databases poses a risk to individuals’ privacy. If these databases fall into the wrong hands or are hacked, sensitive information about people’s identities and whereabouts could be exposed. This unauthorized access could potentially lead to identity theft or misuse of personal information.
To address these concerns, it is crucial to implement robust security measures. Strict access controls should be in place to ensure that only authorized personnel can access the facial recognition systems and databases. Encryption techniques should be employed to protect the data from unauthorized interception or tampering. Maintaining comprehensive audit trails can help identify any potential breaches or misuse of the system.
Misuse Protection
Protecting against the misuse of facial identity tracking technology is essential to prevent its abuse for unethical purposes. Organizations utilizing face tracking systems must prioritize cybersecurity and take proactive measures to mitigate risks.
Strict access controls should be implemented to limit who has permission to use the technology and access sensitive data. This ensures that only authorized individuals with a legitimate need can utilize the system, reducing the risk of misuse.
Encryption techniques play a vital role in safeguarding sensitive data. By encrypting facial recognition databases and communication channels, organizations can protect against unauthorized access or interception of information.
Furthermore, maintaining detailed audit trails helps monitor system usage and detect any potential misuse.
Advantages and Disadvantages of Facial Recognition
Security and Safety Benefits
Facial identity tracking technology offers numerous security and safety benefits, enhancing surveillance capabilities in various settings. By analyzing facial features, this technology enables quick identification of individuals involved in criminal activities or security threats. Law enforcement agencies can use facial recognition systems to match faces captured on CCTV footage with their databases of known criminals, aiding in investigations and preventing crimes.
Moreover, facial identity tracking can assist in locating missing persons. When someone goes missing, time is of the essence, and every minute counts. Facial recognition systems can be employed to scan through vast amounts of video footage from different locations, helping authorities identify the individual’s whereabouts more efficiently.
In public spaces such as airports or stadiums, facial recognition technology can play a crucial role in identifying potential risks. By continuously monitoring crowds and comparing faces against watchlists, security personnel can quickly detect individuals who may pose a threat to public safety. This proactive approach allows for timely intervention and prevention of potential incidents.
Weaknesses and Error Reduction
While facial identity tracking systems offer significant advantages, they also have inherent weaknesses that must be addressed to minimize errors or false identifications. One major concern is the accuracy rate of these systems. In some instances, facial recognition algorithms may struggle to correctly identify individuals due to factors such as poor lighting conditions or variations in camera angles.
To reduce errors and improve accuracy rates, ongoing research focuses on advancements in algorithms and hardware technologies. For instance, researchers are developing sophisticated deep learning models that can learn from vast amounts of data to enhance the system’s ability to accurately recognize faces under challenging conditions.
Efforts are being made to address issues related to false positives (incorrectly identifying an individual) and false negatives (failing to identify an individual). These errors could potentially lead to wrongful accusations or missed opportunities for apprehending suspects.
To mitigate these concerns, experts are exploring techniques like liveness detection, which verifies that the person being scanned is physically present and not a photograph or video. By incorporating such measures, facial recognition systems can become more robust and reliable in real-world scenarios.
Conclusion
We have seen how technological advancements in facial recognition have revolutionized industries such as security, marketing, and healthcare. However, as with any powerful technology, there are ethical and legal considerations that must be carefully addressed to ensure the protection of individuals’ privacy and rights.
As facial recognition becomes more prevalent, it is crucial for organizations to prioritize biometric data protection and adhere to global perspectives and regulations. While face tracking systems offer numerous advantages, they also come with challenges that need to be overcome, such as accuracy, bias, and potential misuse. It is essential to weigh the advantages and disadvantages of facial recognition technology carefully.
In conclusion, facial identity tracking has immense potential but requires responsible implementation. As individuals, it is important to stay informed about the implications of this technology and advocate for ethical practices. As organizations and policymakers, it is crucial to establish clear guidelines and regulations that protect individuals’ rights while harnessing the benefits of facial recognition. By working together, we can ensure a future where facial identity tracking contributes positively to society.
Frequently Asked Questions
What is facial recognition technology?
Facial recognition technology is a system that uses artificial intelligence to analyze and identify individuals based on their unique facial features. It compares the captured image or video frame with a database of known faces to determine a person’s identity.
How has facial recognition technology advanced over the years?
Technological advancements in facial recognition have led to improved accuracy, speed, and reliability. Deep learning algorithms, 3D face modeling, and infrared sensors are some of the developments that have enhanced the capabilities of facial recognition systems.
In what sectors is facial recognition being applied?
Facial recognition has found applications across various sectors including law enforcement, surveillance, banking, healthcare, retail, and travel. It is used for access control, fraud prevention, personalized marketing, patient identification, customer service enhancement, and more.
What are the ethical and legal considerations surrounding facial recognition?
Ethical concerns regarding privacy invasion and potential misuse of personal data arise with the widespread adoption of facial recognition technology. Legal frameworks must address issues such as consent requirements for data collection, transparency in usage policies, and protection against discriminatory practices.
Can facial recognition analyze demographic information or emotions?
Yes, facial recognition can be used to analyze demographic information such as age range or gender based on certain visual cues from the face. Emotion analysis algorithms can detect basic emotions like happiness or sadness by analyzing facial expressions captured in images or videos.
How is biometric data protected in facial recognition systems?
To protect biometric data in facial recognition systems, encryption techniques are employed during storage and transmission. Strict access controls and secure databases ensure that only authorized personnel can access this sensitive information.
Are there global regulations governing the use of facial recognition?
Different countries have varying regulations concerning the use of facial recognition technology. Some regions require explicit consent for data collection, while others impose restrictions on the use of facial recognition in certain contexts. Organizations must comply with local laws and regulations when implementing facial recognition systems.