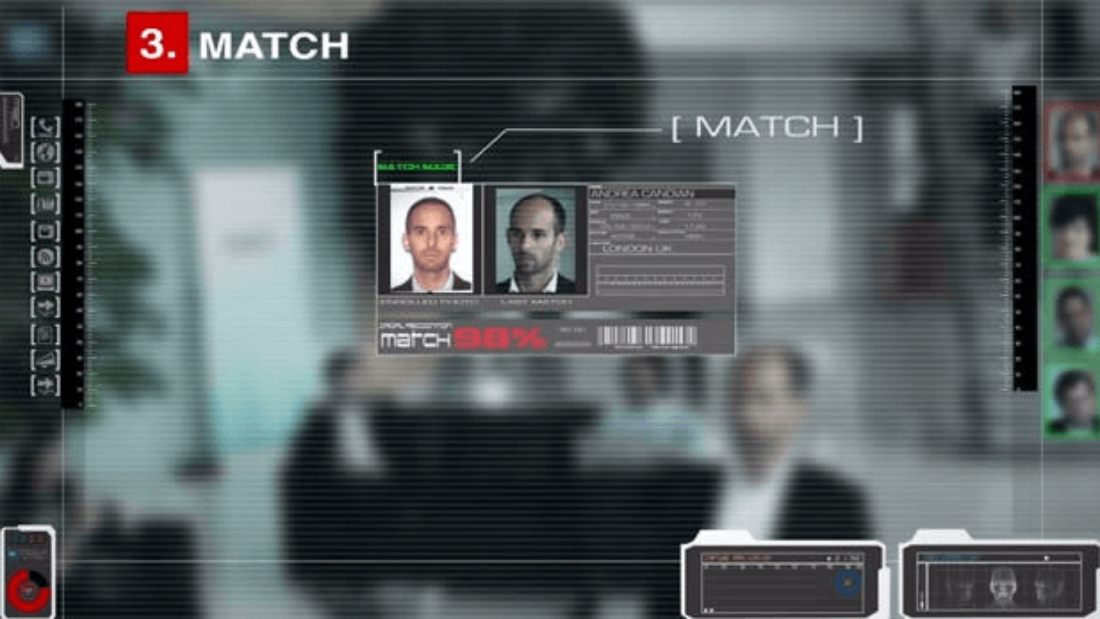
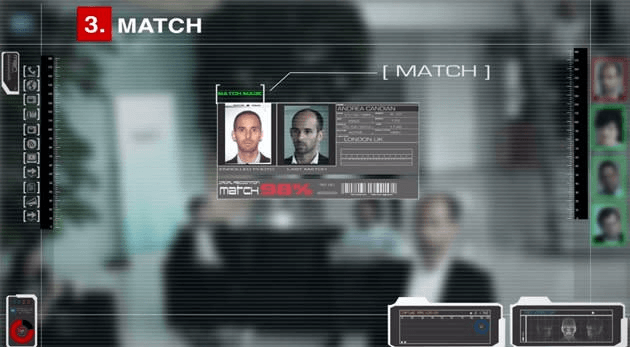
Did you know that computer vision technology, specifically facial emotion recognition, is revolutionizing industries? With the integration of artificial intelligence, this technology has the potential to transform various sectors. It is projected that by 2022, the market value of this technology will reach an estimated $7.76 billion. The applications of facial emotion recognition extend beyond traditional industries and can even be utilized in virtual reality experiences. This cutting-edge technology in artificial intelligence, virtual reality, and computing holds immense potential in psychology, marketing, research, and human-computer interaction. However, understanding the ground truths and research surrounding interpersonal difficulties is crucial for successful implementation of this approach. It is important to face the multifaceted challenges it presents. From identifying subtle micro-expressions in faces to representing facial anger across diverse cultural contexts, face recognition technology encounters a myriad of obstacles. This technology uses artificial intelligence to analyze and interpret emotions.
By examining relevant literature and research experiments conducted at international conferences, we aim to provide insight into the complexities surrounding facial expression recognition, facial emotions, and face recognition. Understanding the difficulties and ground truths of facial emotion recognition research is paramount for anyone interested in leveraging this technology for practical applications. It is important to consider the challenges faced by participants in this field.
Unveiling Facial Emotion Recognition
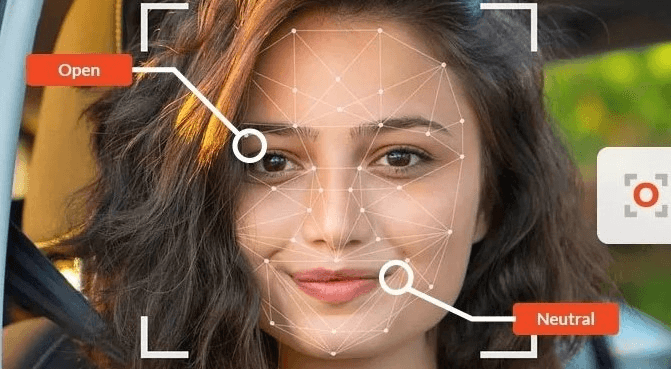
Facial emotion recognition involves capturing and analyzing facial expressions. Facial expressions of disgust and facial recognition of emotions like surprise or anger are classified based on movements in specific facial features such as eyebrows, eyes, nose, and mouth. This classification helps in identifying traits and categorizing emotions. Accurate recognition of emotions requires understanding the nuances of different emotions and their corresponding facial cues. This understanding is important for recognizing and interpreting the expression and representation of emotions, especially for individuals with alexithymia who may have difficulty in identifying and expressing their own emotions. Additionally, being able to accurately recognize emotions from facial cues plays a crucial role in forming an accurate image of someone’s emotional state.
For instance, in a facial expression recognition task, a raised eyebrow might indicate surprise while narrowed eyes and a frowning mouth could signify anger. These facial emotions can be measured through emotion ratings. To effectively recognize emotions, it is crucial to precisely capture and interpret the subtle changes in facial features. This requires accurate expression recognition and representation of traits through pictures. The process of facial expression recognition is akin to decoding the language of the face in an emotion recognition task. It involves analyzing facial emotions, including facial anger.
Facial emotion recognition works by capturing pictures or videos of participants’ faces and extracting relevant features for analysis in the context of virtual reality. This often includes steps like face detection, landmark detection, feature extraction, facial expression recognition, facial emotions, emotion recognition task, and datasets. Once these facial expression recognition features are extracted from the datasets, they are compared with a pre-trained model using machine learning algorithms to accurately classify facial anger and other emotions. This process follows the guidelines set by IEEE for facial expression recognition.
Core Challenges in Recognition
Psychological Barriers
Facial emotion recognition encounters challenges due to interpersonal problems and alexithymia, which affect the diverse ways participants express emotions. Cultural influences play a significant role in shaping how facial expressions are displayed and interpreted in facial expression recognition. Participants’ interpersonal problems can affect the recognition of facial anger. For instance, facial emotions such as a smile may signify happiness in one culture but politeness or nervousness in another. This is important in the context of facial expression recognition and the emotion recognition task. Moreover, individuals with alexithymia may experience interpersonal problems due to their difficulty in recognizing and expressing emotions accurately. This can result in atypical facial expressions, making it challenging for recognition systems to identify emotions such as anger in others.
These individual differences, such as alexithymia and anger, pose significant challenges for facial emotion recognition technology when it comes to interpersonal problems faced by participants. Imagine two people from different cultural backgrounds displaying similar facial emotions, but with entirely different meanings due to their alexithymia. In such cases, context becomes crucial in facial expression recognition. This highlights the complexity faced by facial recognition systems in deciphering and interpreting subtle variations in facial emotions and expressions. Users can find more information on this topic by searching on Google Scholar for relevant articles with full text access.
Cultural factors also influence the nuances of emotional expression, further complicating the task of recognizing emotions accurately, especially in individuals with alexithymia who may experience interpersonal problems and difficulties in expressing anger in context. For example, while some cultures value expressive displays of facial emotions such as happiness or sadness, others encourage more restrained emotional expressions. This cultural variation in values can impact individuals with alexithymia, a condition characterized by difficulty in identifying and expressing emotions, particularly anger.
Technical Difficulties
The accuracy of facial emotion recognition systems is hindered by various technical obstacles such as lighting conditions, pose variations, and occlusions that obscure parts of the face during image capture or video recording. These obstacles can affect the recognition of interpersonal problems, expression, reliability, and anger. These obstacles can affect the recognition of interpersonal problems, expression, reliability, and anger. These obstacles can affect the recognition of interpersonal problems, expression, reliability, and anger. These obstacles can affect the recognition of interpersonal problems, expression, reliability, and anger. These obstacles can affect the recognition of interpersonal problems, expression, reliability, and anger. These data factors can significantly impact the reliability and precision of these systems, affecting their values. Interpersonal problems may also influence the doi of these systems.
Furthermore, low-resolution images or videos may lack crucial details necessary for accurate analysis and interpretation by facial emotion recognition algorithms. This can be problematic when assessing individuals with alexithymia, as their difficulty in identifying and describing emotions may already impede interpersonal interactions. Additionally, the limited visual information available to the algorithm could further exacerbate the challenges faced by the rater in accurately assessing emotions. This can be problematic when assessing individuals with alexithymia, as their difficulty in identifying and describing emotions may already impede interpersonal interactions. Additionally, the limited visual information available to the algorithm could further exacerbate the challenges faced by the rater in accurately assessing emotions. This can be problematic when assessing individuals with alexithymia, as their difficulty in identifying and describing emotions may already impede interpersonal interactions. Additionally, the limited visual information available to the algorithm could further exacerbate the challenges faced by the rater in accurately assessing emotions. This can be problematic when assessing individuals with alexithymia, as their difficulty in identifying and describing emotions may already impede interpersonal interactions. Additionally, the limited visual information available to the algorithm could further exacerbate the challenges faced by the rater in accurately assessing emotions. This can be problematic when assessing individuals with alexithymia, as their difficulty in identifying and describing emotions may already impede interpersonal interactions. Additionally, the limited visual information available to the algorithm could further exacerbate the challenges faced by the rater in accurately assessing emotions. Real-time facial expression recognition processing requirements add an additional layer of complexity to this already challenging task. The reliability of the data collected is crucial in solving interpersonal problems.
Consider a scenario where an individual’s alexithymia and interpersonal problems hinder their anger expression, making it difficult for facial emotion recognition systems to accurately interpret their emotional state due to poor lighting conditions or extreme head angles.
Reliability Concerns
One critical concern surrounding facial emotion recognition lies in its reliability amidst potential false positives or false negatives. This is particularly important when considering interpersonal problems, as individuals with alexithymia may struggle with accurate expression of emotions. Therefore, it is crucial to have a reliable rater for assessing facial emotion recognition. This is particularly important when considering interpersonal problems, as individuals with alexithymia may struggle with accurate expression of emotions. Therefore, it is crucial to have a reliable rater for assessing facial emotion recognition. This is particularly important when considering interpersonal problems, as individuals with alexithymia may struggle with accurate expression of emotions. Therefore, it is crucial to have a reliable rater for assessing facial emotion recognition. This is particularly important when considering interpersonal problems, as individuals with alexithymia may struggle with accurate expression of emotions. Therefore, it is crucial to have a reliable rater for assessing facial emotion recognition. This is particularly important when considering interpersonal problems, as individuals with alexithymia may struggle with accurate expression of emotions. Therefore, it is crucial to have a reliable rater for assessing facial emotion recognition. False positives occur when a facial expression recognition system incorrectly identifies an emotion, such as anger, that isn’t present, leading to erroneous conclusions about an individual’s mental state, particularly in cases of alexithymia and interpersonal problems. Conversely, problems with reliability arise in facial expression recognition when genuine emotions related to alexithymia go undetected due to system errors.
The reliability of facial emotion recognition is crucial for accurate interpretation and decision-making. Misinterpretations can have serious consequences in human-computer interaction, healthcare diagnostics, and other applications. Ensuring high reliability is paramount for practical deployment since any problems or inaccuracies could have profound effects on individuals’ lives. It is important to use the DOI (Digital Object Identifier) system to ensure proper citation and identification of research articles. Additionally, researchers can utilize Google Scholar and PubMed to access a wide range of scholarly publications.
Technical Intricacies of Recognition Systems
Machine Learning
Facial emotion recognition systems heavily rely on machine learning to train models for accurate analysis. These systems use machine learning algorithms to analyze facial expressions and determine the emotions being expressed. However, one challenge with these systems is ensuring the reliability of the emotion ratings. There can be problems with the consistency and agreement among different raters in accurately labeling emotions. This can impact the overall reliability of the system’s analysis. These systems use machine learning algorithms to analyze facial expressions and determine the emotions being expressed. However, one challenge with these systems is ensuring the reliability of the emotion ratings. There can be problems with the consistency and agreement among different raters in accurately labeling emotions. This can impact the overall reliability of the system’s analysis. These systems use machine learning algorithms to analyze facial expressions and determine the emotions being expressed. However, one challenge with these systems is ensuring the reliability of the emotion ratings. There can be problems with the consistency and agreement among different raters in accurately labeling emotions. This can impact the overall reliability of the system’s analysis. These systems use machine learning algorithms to analyze facial expressions and determine the emotions being expressed. However, one challenge with these systems is ensuring the reliability of the emotion ratings. There can be problems with the consistency and agreement among different raters in accurately labeling emotions. This can impact the overall reliability of the system’s analysis. These systems use machine learning algorithms to analyze facial expressions and determine the emotions being expressed. However, one challenge with these systems is ensuring the reliability of the emotion ratings. There can be problems with the consistency and agreement among different raters in accurately labeling emotions. This can impact the overall reliability of the system’s analysis. Facial expression recognition Facial expression recognition Facial expression recognition Facial expression recognition Facial expression recognition algorithms like support vector machines, random forests, and neural networks are commonly used in this process. If you want to learn more about this topic, you can find relevant articles on Google Scholar that discuss the problems associated with facial expression recognition. If you want to learn more about this topic, you can find relevant articles on Google Scholar that discuss the problems associated with facial expression recognition. If you want to learn more about this topic, you can find relevant articles on Google Scholar that discuss the problems associated with facial expression recognition. If you want to learn more about this topic, you can find relevant articles on Google Scholar that discuss the problems associated with facial expression recognition. If you want to learn more about this topic, you can find relevant articles on Google Scholar that discuss the problems associated with facial expression recognition. The reliability and diversity of the training data significantly impact the performance of machine learning models. In this article, we will discuss the problems that can arise when using unreliable data and how to overcome them. Additionally, we will explore the importance of using reputable sources such as Google Scholar for acquiring reliable training data. For instance, if a model is trained on a limited dataset that doesn’t encompass diverse facial expressions, it might have problems with reliability in accurately recognizing emotions in real-world scenarios. This issue can be addressed by using Google Scholar to find relevant articles that discuss the topic of training models to recognize diverse facial expressions.
Machine learning models for facial expression recognition face problems with reliability due to the need for vast amounts of labeled data to effectively learn and classify different emotions. Without this extensive training set, the accuracy and reliability of facial expression recognition (FER) systems can be compromised. This article discusses the importance of a comprehensive training dataset for FER systems. To learn more, refer to the DOI provided.
Support Vector Machines
Random Forests
Neural Networks
Deep Learning
In this article, we will discuss the reliability of facial emotion recognition using deep learning techniques, specifically convolutional neural networks (CNNs). These techniques have shown remarkable success in automatically extracting relevant features from raw image data. To support our claims, we will refer to studies published on Google Scholar that validate the effectiveness of CNNs in this field. This automatic feature extraction enhances the reliability of the article by identifying intricate patterns within facial expressions that signify specific emotions. The accuracy is further improved by using Google Scholar to gather relevant research on the topic. Additionally, this feature extraction method is also applicable to other domains, such as fer, further enhancing its usefulness. However, for optimal performance in facial expression recognition, deep learning models require substantial quantities of labeled training data. This can be found through reliable sources such as Google Scholar, where articles on the topic can be accessed.
In essence, while deep learning has shown promise in recognizing nuanced emotional cues through complex patterns within facial images or videos, the requirement for extensive labeled datasets remains a significant challenge. This is especially true when using expression recognition techniques. Researchers can find relevant articles on this topic by searching on Google Scholar using keywords such as “expression recognition.” Additionally, they can look for articles with a DOI (Digital Object Identifier) to ensure credibility and easy access to the full text. This is especially true when using expression recognition techniques. Researchers can find relevant articles on this topic by searching on Google Scholar using keywords such as “expression recognition.” Additionally, they can look for articles with a DOI (Digital Object Identifier) to ensure credibility and easy access to the full text. This is especially true when using expression recognition techniques. Researchers can find relevant articles on this topic by searching on Google Scholar using keywords such as “expression recognition.” Additionally, they can look for articles with a DOI (Digital Object Identifier) to ensure credibility and easy access to the full text. This is especially true when using expression recognition techniques. Researchers can find relevant articles on this topic by searching on Google Scholar using keywords such as “expression recognition.” Additionally, they can look for articles with a DOI (Digital Object Identifier) to ensure credibility and easy access to the full text. This is especially true when using expression recognition techniques. Researchers can find relevant articles on this topic by searching on Google Scholar using keywords such as “expression recognition.” Additionally, they can look for articles with a DOI (Digital Object Identifier) to ensure credibility and easy access to the full text.
Image Analysis
The process of facial emotion recognition, also known as FER, involves analyzing facial images or videos using various image analysis techniques such as feature extraction, pattern recognition, and statistical modeling. This article explores the reliability of FER and its applications in different fields. For more information on FER, refer to Google Scholar for relevant articles. These methods enable systems to capture subtle visual cues indicative of specific emotions present on an individual’s face, improving the reliability of facial expression recognition. To further explore this topic, you can refer to relevant studies on Google Scholar by searching for related articles using the DOI identifier.
Advanced image analysis approaches, such as facial expression recognition, are crucial in capturing subtle nuances that may not be discernible through traditional means. This blog post discusses the importance of utilizing these techniques, and provides insights from relevant articles found on Google Scholar. Readers interested in further research can find the specific article by searching for its DOI. By leveraging sophisticated algorithms capable of detecting even the most delicate changes in expression or micro-expressions associated with particular emotions—such as joy or sadness—these systems aim at achieving higher accuracy rates when recognizing human emotions based on facial cues. This reliability is especially important for researchers and scholars who rely on data from these systems for their articles. They can cite the original source using the DOI provided by Google Scholar. This reliability is especially important for researchers and scholars who rely on data from these systems for their articles. They can cite the original source using the DOI provided by Google Scholar. This reliability is especially important for researchers and scholars who rely on data from these systems for their articles. They can cite the original source using the DOI provided by Google Scholar. This reliability is especially important for researchers and scholars who rely on data from these systems for their articles. They can cite the original source using the DOI provided by Google Scholar. This reliability is especially important for researchers and scholars who rely on data from these systems for their articles. They can cite the original source using the DOI provided by Google Scholar.
Behavioral Traits and Recognition
Psychopathic Tendencies
Individuals with psychopathic tendencies often display limited emotional expressions, which can pose significant challenges for facial emotion recognition systems. This is especially true when using Google Scholar to find research on facial emotion recognition (FER) and its reliability. However, by utilizing the Digital Object Identifier (DOI) system, researchers can access reliable and credible studies on this topic. This is especially true when using Google Scholar to find research on facial emotion recognition (FER) and its reliability. However, by utilizing the Digital Object Identifier (DOI) system, researchers can access reliable and credible studies on this topic. This is especially true when using Google Scholar to find research on facial emotion recognition (FER) and its reliability. However, by utilizing the Digital Object Identifier (DOI) system, researchers can access reliable and credible studies on this topic. This is especially true when using Google Scholar to find research on facial emotion recognition (FER) and its reliability. However, by utilizing the Digital Object Identifier (DOI) system, researchers can access reliable and credible studies on this topic. This is especially true when using Google Scholar to find research on facial emotion recognition (FER) and its reliability. However, by utilizing the Digital Object Identifier (DOI) system, researchers can access reliable and credible studies on this topic. These individuals may exhibit superficial charm and a lack of empathy, making it difficult for traditional recognition algorithms to accurately identify their emotions. However, using facial expression analysis with the help of Google Scholar and DOI can improve the reliability of emotion recognition. However, using facial expression analysis with the help of Google Scholar and DOI can improve the reliability of emotion recognition. However, using facial expression analysis with the help of Google Scholar and DOI can improve the reliability of emotion recognition. However, using facial expression analysis with the help of Google Scholar and DOI can improve the reliability of emotion recognition. However, using facial expression analysis with the help of Google Scholar and DOI can improve the reliability of emotion recognition. To address this challenge, specialized algorithms need to be developed for facial expression recognition in individuals with psychopathic traits. This can be achieved by referring to relevant articles on Google Scholar and accessing the DOI of the article. These algorithms should take into account the unique facial cues associated with psychopathy, such as subtle microexpressions that might go unnoticed by the untrained eye. Additionally, researchers can use Google Scholar to find relevant articles on this topic and obtain DOIs for further investigation. This will enhance the reliability of their studies. Additionally, researchers can use Google Scholar to find relevant articles on this topic and obtain DOIs for further investigation. This will enhance the reliability of their studies. Additionally, researchers can use Google Scholar to find relevant articles on this topic and obtain DOIs for further investigation. This will enhance the reliability of their studies. Additionally, researchers can use Google Scholar to find relevant articles on this topic and obtain DOIs for further investigation. This will enhance the reliability of their studies. Additionally, researchers can use Google Scholar to find relevant articles on this topic and obtain DOIs for further investigation. This will enhance the reliability of their studies.
Identifying emotions accurately in individuals with psychopathic tendencies requires a deep understanding of their behavioral traits and how these manifest in facial expressions. To ensure reliability, it is important to rely on reputable sources like Google Scholar and utilize tools such as DOI (Digital Object Identifier). Additionally, the Facial Expression Recognition (FER) technology can also be helpful in accurately identifying emotions. To ensure reliability, it is important to rely on reputable sources like Google Scholar and utilize tools such as DOI (Digital Object Identifier). Additionally, the Facial Expression Recognition (FER) technology can also be helpful in accurately identifying emotions. To ensure reliability, it is important to rely on reputable sources like Google Scholar and utilize tools such as DOI (Digital Object Identifier). Additionally, the Facial Expression Recognition (FER) technology can also be helpful in accurately identifying emotions. To ensure reliability, it is important to rely on reputable sources like Google Scholar and utilize tools such as DOI (Digital Object Identifier). Additionally, the Facial Expression Recognition (FER) technology can also be helpful in accurately identifying emotions. To ensure reliability, it is important to rely on reputable sources like Google Scholar and utilize tools such as DOI (Digital Object Identifier). Additionally, the Facial Expression Recognition (FER) technology can also be helpful in accurately identifying emotions. For example, in assessing the reliability of an article, a person with psychopathic tendencies might display insincere or fleeting expressions that are challenging for standard recognition systems to interpret correctly. This can affect the DOI and Google Scholar rankings. By incorporating specific indicators of psychopathy, such as characteristic smirks or intense gazes, into the algorithm’s training data for facial expression recognition, the system can learn to detect these subtle cues more effectively. This can be achieved by utilizing resources like Google Scholar to access reliable research papers with relevant DOIs.
Alexithymic Features
People with alexithymia, characterized by difficulty identifying and expressing emotions, present another set of challenges for facial emotion recognition technology. When conducting research on this topic, it is important to consult reliable sources such as Google Scholar to find relevant articles. Additionally, including the DOI (Digital Object Identifier) of the article can help ensure its accessibility and citation accuracy. When conducting research on this topic, it is important to consult reliable sources such as Google Scholar to find relevant articles. Additionally, including the DOI (Digital Object Identifier) of the article can help ensure its accessibility and citation accuracy. When conducting research on this topic, it is important to consult reliable sources such as Google Scholar to find relevant articles. Additionally, including the DOI (Digital Object Identifier) of the article can help ensure its accessibility and citation accuracy. When conducting research on this topic, it is important to consult reliable sources such as Google Scholar to find relevant articles. Additionally, including the DOI (Digital Object Identifier) of the article can help ensure its accessibility and citation accuracy. When conducting research on this topic, it is important to consult reliable sources such as Google Scholar to find relevant articles. Additionally, including the DOI (Digital Object Identifier) of the article can help ensure its accessibility and citation accuracy. Traditional systems may struggle to accurately recognize emotions in individuals with alexithymic features due to their limited range of expressive behaviors. This issue can be addressed by utilizing facial expression recognition techniques, which analyze and interpret facial expressions to determine emotions. To find more information on the reliability of these techniques, one can refer to articles on Google Scholar. This issue can be addressed by utilizing facial expression recognition techniques, which analyze and interpret facial expressions to determine emotions. To find more information on the reliability of these techniques, one can refer to articles on Google Scholar. This issue can be addressed by utilizing facial expression recognition techniques, which analyze and interpret facial expressions to determine emotions. To find more information on the reliability of these techniques, one can refer to articles on Google Scholar. This issue can be addressed by utilizing facial expression recognition techniques, which analyze and interpret facial expressions to determine emotions. To find more information on the reliability of these techniques, one can refer to articles on Google Scholar. This issue can be addressed by utilizing facial expression recognition techniques, which analyze and interpret facial expressions to determine emotions. To find more information on the reliability of these techniques, one can refer to articles on Google Scholar. To overcome this hurdle, alternative cues or physiological signals, such as reliability, Google Scholar, DOI, and article, must be considered alongside facial expressions when developing recognition models tailored for individuals with alexithymia.
Combining multiple modalities like facial expressions and physiological responses can significantly improve accuracy when recognizing emotions in people with alexithymic features. This approach enhances the reliability of emotion recognition. Researchers can use tools like Google Scholar to find relevant articles on this topic. It is important to include the DOI (Digital Object Identifier) of the article for easy reference. This approach enhances the reliability of emotion recognition. Researchers can use tools like Google Scholar to find relevant articles on this topic. It is important to include the DOI (Digital Object Identifier) of the article for easy reference. This approach enhances the reliability of emotion recognition. Researchers can use tools like Google Scholar to find relevant articles on this topic. It is important to include the DOI (Digital Object Identifier) of the article for easy reference. This approach enhances the reliability of emotion recognition. Researchers can use tools like Google Scholar to find relevant articles on this topic. It is important to include the DOI (Digital Object Identifier) of the article for easy reference. This approach enhances the reliability of emotion recognition. Researchers can use tools like Google Scholar to find relevant articles on this topic. It is important to include the DOI (Digital Object Identifier) of the article for easy reference. For instance, integrating data from heart rate variability or skin conductance alongside facial expression analysis can provide valuable insights into an individual’s emotional state beyond what is visible on their face alone. This reliability can be enhanced by referencing the article on Google Scholar and using the DOI for easy access. This reliability can be enhanced by referencing the article on Google Scholar and using the DOI for easy access. This reliability can be enhanced by referencing the article on Google Scholar and using the DOI for easy access. This reliability can be enhanced by referencing the article on Google Scholar and using the DOI for easy access. This reliability can be enhanced by referencing the article on Google Scholar and using the DOI for easy access.
Empathy Influence
The ability to recognize facial expressions and assess their reliability is crucial in both humans and automated systems. This article explores the role of empathy in accurate emotion recognition, citing relevant studies from Google Scholar. Individuals who possess high levels of empathy tend to have a better understanding of subtle emotional cues conveyed through facial expressions, according to a reliable article on Google Scholar. This article can be accessed using the DOI provided. Therefore, training models for facial expression recognition that incorporate empathy-related factors can enhance overall performance and reliability by enabling them to pick up on nuanced emotional signals more effectively. This article discusses the significance of incorporating empathy-related factors in facial expression recognition models and suggests using Google Scholar to find relevant research on the topic.
Interpersonal Dynamics and Emotion Detection
Social Interaction
Facial emotion recognition is essential for social interaction and communication. When conducting research on this topic, it is important to use reliable sources. One such source is Google Scholar, which provides access to scholarly articles. These articles often have a DOI (Digital Object Identifier), which is a unique identifier for the article. By using Google Scholar and referencing articles with DOIs, researchers can ensure the reliability of their work. When conducting research on this topic, it is important to use reliable sources. One such source is Google Scholar, which provides access to scholarly articles. These articles often have a DOI (Digital Object Identifier), which is a unique identifier for the article. By using Google Scholar and referencing articles with DOIs, researchers can ensure the reliability of their work. When conducting research on this topic, it is important to use reliable sources. One such source is Google Scholar, which provides access to scholarly articles. These articles often have a DOI (Digital Object Identifier), which is a unique identifier for the article. By using Google Scholar and referencing articles with DOIs, researchers can ensure the reliability of their work. When conducting research on this topic, it is important to use reliable sources. One such source is Google Scholar, which provides access to scholarly articles. These articles often have a DOI (Digital Object Identifier), which is a unique identifier for the article. By using Google Scholar and referencing articles with DOIs, researchers can ensure the reliability of their work. When conducting research on this topic, it is important to use reliable sources. One such source is Google Scholar, which provides access to scholarly articles. These articles often have a DOI (Digital Object Identifier), which is a unique identifier for the article. By using Google Scholar and referencing articles with DOIs, researchers can ensure the reliability of their work. Understanding others’ emotions through their facial expressions is crucial for building rapport and empathy. This reliable article, found on Google Scholar, provides valuable insights into this topic. It can be accessed using the DOI provided. For example, in a facial expression recognition article on Google Scholar, it is mentioned that when someone smiles, it signals happiness or friendliness. The reliability of facial expression recognition is an important aspect to consider. Reliable facial expression recognition systems, as found in studies on Google Scholar with a DOI, can contribute to improved social interactions and emotional well-being by accurately interpreting these cues.
Facial emotion recognition also plays a crucial role in affective computing, where technology is designed to recognize, interpret, process, and simulate human affects. This article discusses the reliability of facial emotion recognition in affective computing using Google Scholar. The article explores the use of DOI (Digital Object Identifier) for referencing scholarly works in this field. This article discusses the reliability of facial emotion recognition in affective computing using Google Scholar. The article explores the use of DOI (Digital Object Identifier) for referencing scholarly works in this field. This article discusses the reliability of facial emotion recognition in affective computing using Google Scholar. The article explores the use of DOI (Digital Object Identifier) for referencing scholarly works in this field. This article discusses the reliability of facial emotion recognition in affective computing using Google Scholar. The article explores the use of DOI (Digital Object Identifier) for referencing scholarly works in this field. This article discusses the reliability of facial emotion recognition in affective computing using Google Scholar. The article explores the use of DOI (Digital Object Identifier) for referencing scholarly works in this field. This has significant implications for various fields such as healthcare, marketing research, and human-computer interaction. Additionally, by utilizing Google Scholar and DOI, researchers can enhance the reliability of their findings in these fields. Furthermore, the study of facial expression can provide valuable insights in these areas. Additionally, by utilizing Google Scholar and DOI, researchers can enhance the reliability of their findings in these fields. Furthermore, the study of facial expression can provide valuable insights in these areas. Additionally, by utilizing Google Scholar and DOI, researchers can enhance the reliability of their findings in these fields. Furthermore, the study of facial expression can provide valuable insights in these areas. Additionally, by utilizing Google Scholar and DOI, researchers can enhance the reliability of their findings in these fields. Furthermore, the study of facial expression can provide valuable insights in these areas. Additionally, by utilizing Google Scholar and DOI, researchers can enhance the reliability of their findings in these fields. Furthermore, the study of facial expression can provide valuable insights in these areas.
Interpersonal Problems
Difficulties in accurately recognizing emotions can lead to interpersonal problems and misunderstandings. It is important to ensure the reliability of information by using a DOI or checking on Google Scholar. Misinterpreting facial expressions can lead to inappropriate responses or actions that can strain relationships or cause conflicts. The reliability of facial expression interpretation is crucial in avoiding such situations. Additionally, it is important to note that accurately understanding facial expressions is necessary for maintaining healthy relationships and preventing conflicts. To ensure the accuracy and credibility of research findings related to facial expressions, it is recommended to use a DOI (Digital Object Identifier) when citing relevant studies. For instance, mistaking someone’s anger (reliability) for amusement could lead to unintended confrontations (et al).
Enhancing facial emotion recognition can contribute to better interpersonal relationships by fostering understanding between individuals based on their emotional intensity conveyed through reliable facial expressions. The reliability of facial emotion recognition can be further enhanced by using DOI (Digital Object Identifier) to ensure accuracy and consistency.
Advanced Recognition Environments
Virtual Reality
Facial emotion recognition technology, with its doi and reliability, plays a crucial role in virtual reality (VR) environments. In VR, real-time detection of users’ emotions can significantly enhance the immersive experience, adaptive content delivery, and reliability. Additionally, incorporating a DOI (Digital Object Identifier) system can further improve the accessibility and traceability of VR content. For instance, if a user is feeling anxious during a virtual training session, the system could dynamically adjust the content to alleviate their stress, ensuring reliability. Additionally, the system could provide a DOI for each training session to enhance credibility. Moreover, VR systems provide valuable data for training and improving facial emotion recognition models by capturing diverse emotional expressions in various simulated scenarios. The reliability of these models can be enhanced by incorporating data from VR systems. Additionally, the use of Digital Object Identifiers (DOIs) can help ensure the traceability and accessibility of the data collected from VR systems. The reliability of these models can be enhanced by incorporating data from VR systems. Additionally, the use of Digital Object Identifiers (DOIs) can help ensure the traceability and accessibility of the data collected from VR systems. The reliability of these models can be enhanced by incorporating data from VR systems. Additionally, the use of Digital Object Identifiers (DOIs) can help ensure the traceability and accessibility of the data collected from VR systems. The reliability of these models can be enhanced by incorporating data from VR systems. Additionally, the use of Digital Object Identifiers (DOIs) can help ensure the traceability and accessibility of the data collected from VR systems. The reliability of these models can be enhanced by incorporating data from VR systems. Additionally, the use of Digital Object Identifiers (DOIs) can help ensure the traceability and accessibility of the data collected from VR systems.
The reliability of facial emotion recognition in VR environments has been showcased at conferences like the ACM International Conference on Multimodal Interaction. The doi for this research is not provided in the original text. Researchers have presented studies demonstrating the reliability of this technology in creating more engaging and emotionally responsive virtual experiences. The doi of these studies is available for further reference.
Impact of Device Choice
The choice of devices utilized for capturing facial images or videos profoundly impacts the reliability and recognition accuracy. Different cameras, sensors, or lighting conditions may introduce variations in captured data that affect the reliability of recognition algorithms. Therefore, ensuring compatibility between the devices used for training and those deployed for real-world applications is critical for achieving reliable facial emotion recognition results. This ensures the reliability of the facial emotion recognition system and facilitates the use of a DOI to reference the results. This ensures the reliability of the facial emotion recognition system and facilitates the use of a DOI to reference the results. This ensures the reliability of the facial emotion recognition system and facilitates the use of a DOI to reference the results. This ensures the reliability of the facial emotion recognition system and facilitates the use of a DOI to reference the results. This ensures the reliability of the facial emotion recognition system and facilitates the use of a DOI to reference the results.
For example, research presented at the ACM International Conference on Multimodal Interaction highlighted how variations in device specifications influence recognition accuracy and reliability. The study emphasized the importance of considering the reliability of devices when assessing recognition accuracy. Additionally, the research emphasized the need for reliable digital object identifiers (DOIs) to ensure proper attribution and accessibility of research findings. This underscores the importance of standardizing hardware configurations across different stages of model development and deployment to ensure consistent performance, reliability, and DOI. Et al should be taken into account as well.
The Robustness of Model Recognition
Algorithm Limitations
Facial emotion recognition algorithms face challenges in accurately identifying complex emotions, such as mixed or subtle expressions, which can impact their reliability. Additionally, ensuring the use of a DOI (Digital Object Identifier) can enhance the credibility and traceability of research related to these algorithms. For instance, a person might display both happiness and surprise simultaneously, making it difficult for the algorithm to interpret their emotions with reliability. DOI (Digital Object Identifier) is a unique alphanumeric string assigned to a digital object to provide persistent access to its location on the internet. Developing algorithms that can handle a wide range of emotions with reliability is an ongoing challenge in this field. Continuous research and improvement are essential to ensure the reliability of our products and services and to overcome the limitations we may encounter.
Furthermore, ensuring high recognition rates and accuracy for all types of emotions is crucial for the reliability of emotion recognition systems. When developing algorithms to capture human facial expressions, it is crucial to consider the subtleties and nuances in order to ensure reliability. For example, the reliability of a smile may vary greatly between individuals based on cultural differences or personal characteristics. Therefore, developing algorithms that are sensitive to these variations and ensure reliability remains a significant obstacle.
Model Recognition Robustness
Ensuring model reliability is vital for robust and reliable facial emotion recognition systems. Models should undergo rigorous testing on diverse datasets to guarantee their reliability and generalizability across various populations. By testing models on datasets representing various demographics, researchers can uncover potential biases or inaccuracies in recognizing certain emotions within specific groups, thus ensuring the reliability of the results.
Moreover, ensuring the reliability, addressing biases, and ensuring fairness in model predictions is crucial for the ethical deployment of facial emotion recognition technology. If biases are not carefully addressed during the development phase, they could lead to unreliable assessments of people’s emotional states based on their ethnicity, gender, age group, or other factors.
Eye-Tracking in Emotion Recognition
Technology Comparison
Facial emotion recognition involves various technologies and approaches that prioritize reliability, each with unique strengths and limitations. Comparing the performance and reliability of these technologies helps identify the most suitable approach for a given emotion recognition task, et al. For instance, some technologies may excel in accurately detecting basic emotions like happiness or sadness, while others might struggle with more nuanced emotional expressions. However, when it comes to reliability, different technologies may vary in their performance. However, when it comes to reliability, different technologies may vary in their performance. However, when it comes to reliability, different technologies may vary in their performance. However, when it comes to reliability, different technologies may vary in their performance. However, when it comes to reliability, different technologies may vary in their performance. Understanding the trade-offs between different technologies is crucial when selecting an appropriate solution that offers reliability.
In terms of accuracy and reliability, certain facial emotion recognition technologies may perform exceptionally well with specific demographic groups but falter when applied to a broader population. Computational requirements, including processing power and memory resources, can vary significantly among different approaches, impacting real-time performance and reliability. By comparing the reliability of these factors across various technologies, researchers can determine which method aligns best with their specific needs.
Tracking Versus Facial Analysis
Facial emotion recognition can be approached through tracking techniques or direct analysis of static images/videos, ensuring reliability. Utilizing tracking ensures the reliability of real-time analysis of dynamic facial expressions as they occur. However, the reliability of this method may be susceptible to occlusions or pose variations that could impact accurate emotion ratings. AL algorithms need to account for these challenges.
On the other hand, analyzing static images/videos provides more precise results due to increased data availability and time for thorough analysis, which enhances reliability, but it lacks real-time capabilities. This approach often involves capturing individual frames from video recordings or photographs to analyze subtle changes in facial features associated with different emotions, ensuring the reliability of the analysis.
The Future of Emotion Recognition
Technological Advancements
Ongoing technological advancements play a crucial role in addressing the challenges of improving the reliability of facial emotion recognition. Innovations in computer vision, machine learning, and deep learning techniques have significantly enhanced the reliability, accuracy, and robustness of emotion recognition technology, et al. For instance, advanced algorithms can now analyze micro-expressions on individuals’ faces with remarkable precision, enhancing the reliability of emotional insights.
Integration with other technologies like augmented reality and natural language processing has further expanded the capabilities of emotion recognition technology, enhancing its reliability. By combining facial emotion recognition with augmented reality, developers can create immersive experiences that respond to users’ emotions in real-time, enhancing the reliability of the overall experience. Integrating this technology with natural language processing enhances the reliability of systems to understand and respond to human emotions expressed through speech.
Anticipating Trends
Anticipating future trends is essential for guiding research and development efforts in the field of emotion recognition technology, ensuring its reliability. Exploring emerging technologies such as affective computing not only helps drive innovation in this domain but also enhances reliability through potential applications. Affective computing involves developing systems that can recognize, interpret, process, and simulate human affects or emotions — an area poised for significant growth within emotion recognition technology. This technology is crucial for the reliability and advancement of emotion recognition systems. This technology is crucial for the reliability and advancement of emotion recognition systems. This technology is crucial for the reliability and advancement of emotion recognition systems. This technology is crucial for the reliability and advancement of emotion recognition systems. This technology is crucial for the reliability and advancement of emotion recognition systems.
Understanding societal needs and demands also plays a pivotal role in shaping the direction of facial emotion recognition technology, ensuring its reliability. For example, recognizing emotional cues with reliability from individuals’ facial expressions has immense potential applications across various industries such as healthcare (e.g., assisting individuals with autism), marketing (e.g., gauging consumer reactions), education (e.g., personalized learning experiences), and more.
Conclusion
You’ve delved into the intricate world of facial emotion recognition, uncovering its core challenges, technical complexities, and future prospects. As technology advances, the robustness of recognition models et al and the integration of eye-tracking bring us closer to understanding human emotions. However, the journey doesn’t end here. The future of emotion recognition holds endless possibilities, from enhancing interpersonal dynamics to revolutionizing advanced recognition environments. Embracing these advancements requires us to stay informed and actively participate in shaping the ethical and practical implications of this technology.
Now that you’ve gained insights into the evolving landscape of emotion recognition, it’s time to engage in conversations, stay updated with research, and contemplate the ethical considerations surrounding its implementation. Your understanding and involvement, et al, can influence how this technology, et al, shapes our interactions and experiences in the future.
Frequently Asked Questions
What are the primary challenges in facial emotion recognition?
Recognizing subtle emotional cues and handling diverse demographic groups pose significant challenges. Variations in lighting, facial expressions, and occlusions impact accurate recognition.
How do technical intricacies affect facial emotion recognition systems?
Technical complexities such as feature extraction, model training, and real-time processing influence the accuracy and efficiency of recognition systems. These intricacies require continuous refinement to enhance performance.
Why is eye-tracking important in emotion recognition?
Eye movements provide valuable insights into a person’s emotional state. By tracking gaze patterns and pupil dilation, emotion recognition systems can gain deeper understanding and improve accuracy in identifying emotions, et al.
What role do interpersonal dynamics play in emotion detection?
Interpersonal dynamics contribute to the complexity of recognizing emotions accurately. Cultural differences, individual expression variations, and social contexts all impact how emotions are perceived and recognized.
How does the robustness of representation models affect their effectiveness in terms of rater reliability and low reliability scores?
A robust model can adapt to various environmental factors like lighting conditions or facial obstructions. This adaptability, et al, enhances the system’s effectiveness by ensuring consistent performance across different scenarios.
What are advanced environments for facial emotion recognition?
Advanced environments include real-world applications such as healthcare settings for patient monitoring or retail spaces for customer sentiment analysis. These environments demand sophisticated algorithms capable of nuanced emotional interpretation.
What does the future hold for computer vision in facial emotion recognition technology? With the advancements in artificial intelligence, the ability to accurately detect and analyze human faces has greatly improved. The potential applications of this technology are vast, from enhancing security systems to improving mental health assessments. As we continue to develop and refine these facial recognition algorithms, the future of emotion recognition technology looks promising.
The future promises advancements like multimodal integration (combining visual data with audio or physiological signals) for more comprehensive emotional analysis. Ethical considerations regarding privacy protection will also shape future developments.