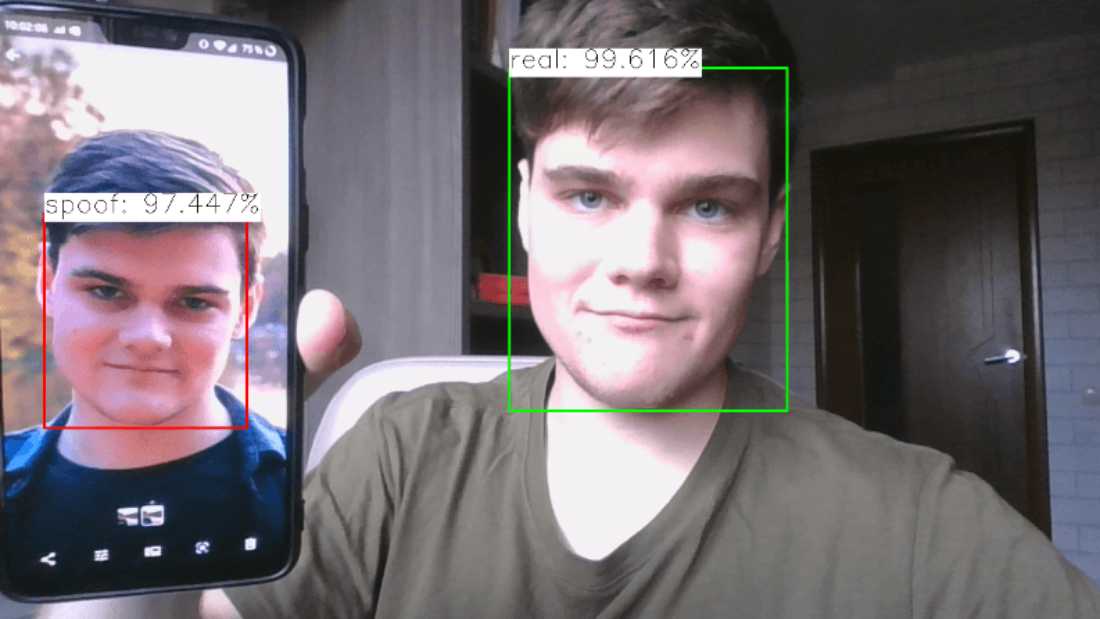
Facial recognition technology, powered by machine learning and deep learning algorithms, has revolutionized the field of demographic studies, providing a novel approach to gather data and analyze populations. This innovative technology combines social psychology principles with human review to enhance accuracy and efficiency. This article delves into the world of demographic studies using facial recognition, exploring its advantages, limitations, and impact on research methodologies. It also examines the role of deep learning in reducing racial bias in human review and how social psychology plays a part in understanding these dynamics. It also examines the role of deep learning in reducing racial bias in human review and how social psychology plays a part in understanding these dynamics.
In recent years, deep learning has gained significant interest in various areas of study due to its ability to extract valuable insights from images of human faces. Facial recognition technology has become visually prominent and is now being used to analyze personal information and even predict aspects of a person’s personality. By analyzing facial features and characteristics using face recognition technology, researchers can gain a deeper understanding of participants’ demographics, personality traits, and more. This analysis is done through the use of face recognition technologies and incorporates principles from social psychology. Additionally, the data collected through this process may undergo human review for further analysis. However, it is crucial to note that the use of facial recognition in demographic analysis raises ethical concerns regarding privacy and consent. This is especially important when dealing with personal information collected through surveys or included in datasets used for deep learning. This is especially important when dealing with personal information collected through surveys or included in datasets used for deep learning.
This article will delve into the nature of demographic studies using facial recognition technology, examining different research methods employed in this area. The survey dataset used in these studies often contains personal information. The survey dataset used in these studies often contains personal information. In this blog post, we will delve into the challenges faced by researchers when conducting surveys and working with large-scale datasets. We will also examine potential biases that may arise during analysis, as well as study and sample predictions.
Exploring Facial Recognition in Demographics
Facial recognition technology has revolutionized various fields, including demographic analysis. It utilizes deep image features and basic face metrics to identify individuals and extract personal information from specific areas of their faces. It utilizes deep image features and basic face metrics to identify individuals and extract personal information from specific areas of their faces. By analyzing face recognition technologies, this technology provides valuable insights into demographic effects and trends based on basic face metrics. Additionally, it can also offer insights into personality characteristics and trends. Let’s delve deeper into the role of facial recognition in demographic studies, specifically focusing on face metrics and the study of personal information and personality.
Demographic analysis involves studying population characteristics, including personal attributes and trends, to understand social dynamics. This analysis may include the collection and analysis of personal information and face metrics to gain insights into the sample population. Traditionally, this sample study relied on surveys, questionnaires, and other methods that can be time-consuming and costly. These methods are used to gather personal information and examine the demographic effects. However, with facial recognition technology, researchers can now gain valuable insights by analyzing facial images. This technology allows for the identification and analysis of a person’s face, which can provide significant personal information and enable accurate predictions. The National Institute of Standards and Technology (NIST) has been instrumental in setting the standards for facial recognition algorithms and ensuring their accuracy and reliability. This technology allows for the identification and analysis of a person’s face, which can provide significant personal information and enable accurate predictions. The National Institute of Standards and Technology (NIST) has been instrumental in setting the standards for facial recognition algorithms and ensuring their accuracy and reliability.
One crucial aspect of demographic analysis is the availability of diverse datasets that accurately represent different populations and include personal information, fitness data, facial images, and utilize face recognition technology. Native American datasets are particularly important for accurate demographic analysis of this specific group, especially when it comes to personal information and face recognition technology using facial images. The inclusion of Native American datasets helps in complying with the guidelines set by NIST. To ensure accurate facial recognition algorithms, it is crucial to train them on diverse datasets that encompass a wide range of images, including those of Native American faces. This helps to account for demographic effects and leverage deep image features. The National Institute of Standards and Technology (NIST) recognizes the importance of this approach in developing robust facial recognition technology. This helps prevent biased results in facial analysis and ensures fair representation across different ethnicities, considering the demographic effects of face recognition technology on facial images.
False positive differentials refer to variations in the accuracy of face recognition across different demographic groups, based on deep image features. These variations can affect the prediction of images. Understanding the effects of demographics on facial recognition technology is crucial as it allows us to address biases that may exist within the technology. By analyzing deep image features and considering the impact of different demographic factors, we can gain a better understanding of how these biases may be present in the recognition of faces. By utilizing facial analysis and face recognition technology, we can accurately identify and reduce false positive differentials in demographic studies. This ensures fair and unbiased analysis of facial images and contributes to the advancement of facial recognition technology (FMR).
While facial recognition technology offers significant potential in demographic analysis, it also has limitations that need to be considered. In this article, we will explore the face prediction capabilities of this technology and how it can analyze images. In this article, we will explore the face prediction capabilities of this technology and how it can analyze images. For instance, the accuracy of face recognition algorithms can vary based on factors such as lighting conditions or changes in appearance (e.g., aging or facial hair). These algorithms use images to predict and analyze information, taking into account variables like lighting and appearance changes. These algorithms use images to predict and analyze information, taking into account variables like lighting and appearance changes. These limitations should be taken into account when conducting demographic studies using facial recognition technology. The accuracy of the system depends on the quality of the face images, as well as the variables that can affect the results. Therefore, it is important to consider these factors when utilizing FMR for demographic research.
Moreover, it is important to carefully evaluate the implications of using facial recognition technology in demographics, as it can provide valuable information about individuals based on their face and images. As with any technological advancement, there are ethical considerations surrounding face recognition technology, privacy concerns, potential biases, and the use of information obtained from facial images. Researchers must consider the implications of utilizing facial recognition technology for demographic purposes, specifically in predicting demographics based on face images using FMR.
Demographic Effects on Facial Recognition Systems
Facial recognition technology has become increasingly prevalent in various fields, including demographic studies. This technology uses face images to make predictions using FMR (False Match Rate) algorithms. This technology uses face images to make predictions using FMR (False Match Rate) algorithms. However, it is crucial to evaluate the performance of facial recognition algorithms to ensure accurate and reliable results for predicting faces in images and extracting information.
Performance evaluation is crucial in assessing the strengths and weaknesses of facial recognition systems, particularly in predicting faces from images. The evaluation process involves analyzing the system’s performance using the Face Match Rate (FMR) as a key metric. By continuously monitoring and improving the performance of face recognition technology, researchers can enhance the accuracy of demographic analysis by predicting information based on facial images. Evaluating the performance of face recognition technology involves measuring its ability to correctly identify individuals based on their facial features in images. This evaluation includes predicting the accuracy using metrics such as AUC. This evaluation process helps identify any biases or limitations that may exist within the facial analysis and face recognition technology system. It analyzes variables and facial images to ensure accuracy and fairness.
Disparities in the reliability of demographic studies using facial recognition systems can be significantly impacted by variables such as images and AUC. Each face recognition system may exhibit variations in accuracy and performance due to differences in algorithms, training data, hardware capabilities, variables, and facial images. These disparities can lead to inconsistent and biased results when analyzing demographic information, particularly in the context of facial analysis and face recognition using facial images. The presence of various variables further complicates the accuracy and reliability of these analyses.
Addressing disparities across facial recognition systems is crucial for ensuring consistent and unbiased outcomes. This includes examining the variables that affect the accuracy of the system, such as the quality of images used and the use of automated algorithms. Additionally, conducting an analysis of the auc (area under the curve) can provide valuable insights into the overall performance of the system. By addressing these factors, we can work towards creating more reliable and fair facial recognition technology. This includes examining the variables that affect the accuracy of the system, such as the quality of images used and the use of automated algorithms. Additionally, conducting an analysis of the auc (area under the curve) can provide valuable insights into the overall performance of the system. By addressing these factors, we can work towards creating more reliable and fair facial recognition technology. Researchers need to carefully select or develop algorithms for face recognition and facial analysis that minimize biases related to age, gender, race, or other demographic variables in facial images. Efforts should be made to improve algorithmic fairness in face recognition and facial analysis by reducing false positives/negatives for different demographics based on variables such as facial images.
To achieve more accurate results in demographic studies using facial recognition technology, it is essential to consider factors such as dataset diversity, representativeness, and the use of images and variables. The training datasets used for developing face recognition systems should include a wide range of individuals from diverse backgrounds to avoid underrepresentation or overrepresentation of specific groups in facial images. This ensures accurate facial analysis and accounts for variables in the data.
Moreover, continuous monitoring and improvement of facial recognition systems are necessary throughout the development and deployment stages. This includes monitoring variables and optimizing images. Regular updates and refinements can help mitigate any emerging biases or inaccuracies in face recognition and facial analysis that may arise due to changes in demographics or societal shifts. These updates are crucial for maintaining accuracy and fairness in the analysis of variables present in facial images.
The Role of Demographics in Face Recognition Technology
Facial recognition technology has gained significant attention in recent years, with its applications ranging from security systems to social media filters. These applications often rely on the use of images and variables to accurately identify and analyze faces. These applications often rely on the use of images and variables to accurately identify and analyze faces. However, the use of face recognition and facial analysis technology for studying demographics raises important considerations related to the analysis of facial images and variables.
Racial Discrimination Concerns
One of the primary concerns surrounding facial recognition technology is the potential for racial discrimination. This concern arises due to the use of images and variables in the technology. This concern arises due to the use of images and variables in the technology. Studies have shown that certain algorithms used in facial analysis technologies can exhibit biases towards specific racial groups. These biases can be observed in the recognition of facial images and are influenced by various variables. This bias in facial analysis and face recognition can lead to inaccurate results and unfair treatment of individuals belonging to certain races. The accuracy of facial images and the variables involved can significantly impact the outcomes.
To ensure fairness and address concerns related to demographic studies using facial recognition technology, it is crucial to take proactive measures by incorporating images and variables. Efforts should be made to identify and mitigate any biases present in the face recognition and facial analysis algorithms or datasets used for analyzing facial images. This can involve diversifying training data to include a wide range of racial backgrounds and regularly evaluating the performance of the face recognition system across different demographics. Facial analysis is crucial in accurately analyzing facial images and identifying variables.
Moreover, transparency and accountability are essential in addressing racial discrimination concerns related to face recognition and facial analysis. These variables play a crucial role in analyzing and recognizing individuals based on their facial images. Researchers and developers should make efforts to clearly communicate how their facial recognition systems work, including any potential biases or limitations. This includes providing detailed explanations of the algorithms used, the role of images in training the system, and the variables considered during the recognition process. This includes providing detailed explanations of the algorithms used, the role of images in training the system, and the variables considered during the recognition process. Engaging with communities affected by face recognition and facial analysis technologies can also provide valuable insights into addressing concerns related to these technologies effectively. These insights can help in understanding the impact of these technologies on individuals’ privacy and security, as well as identifying the variables that need to be considered for better implementation.
Gender and Population Density Interactions
In addition to racial considerations, understanding how gender, population density, images, and variables interact with facial recognition technology is crucial for accurate interpretation of demographic studies. Both gender, variables, and population density can influence the outcomes of facial analysis on facial images.
Gender plays a role in determining various facial features, such as bone structure and texture, which may affect the accuracy of face recognition algorithms differently for men and women. These algorithms rely heavily on analyzing images and variables to identify and distinguish between individuals. These algorithms rely heavily on analyzing images and variables to identify and distinguish between individuals. Therefore, it is important to account for gender differences when conducting demographic studies using facial recognition technology. These studies can analyze images of individuals and use variables such as gender to gather data accurately. These studies can analyze images of individuals and use variables such as gender to gather data accurately.
Population density refers to the concentration of people within a given area, and can be analyzed using variables such as facial analysis and facial images. Facial analysis of densely populated areas often faces challenges in accurate face recognition due to occlusion and variations in lighting conditions. These factors can affect the performance of facial images. When analyzing demographic data using facial recognition technology, researchers should consider the impact of population density on the reliability of results. This includes taking into account how variables such as images can affect the accuracy of the findings. This includes taking into account how variables such as images can affect the accuracy of the findings.
Advancing Equitable Recognition in Demographic Studies
Creating a fair landscape, especially when it comes to facial images, is crucial. It involves considering various variables to ensure fairness. It involves addressing biases in facial images and ensuring equal representation across different demographic groups by considering variables. By analyzing facial images, we can obtain accurate insights that reflect the diversity within society. This analysis takes into account various variables.
To achieve fairness in facial recognition algorithms, it is important to acknowledge and address any biases that may exist in the variables used for analyzing images. These biases can stem from various factors such as imbalanced training data, inherent limitations of the technology itself, or issues related to facial images and variables. Efforts should be made to mitigate biases in facial image algorithms through rigorous testing, ongoing research, and continuous improvement of the variables.
Equal representation is essential in demographic studies. This means ensuring that all demographic groups are adequately represented in the datasets used for analysis, including facial images and variables. By including diverse facial images in our samples, we can avoid skewed results and ensure that findings are applicable to a wide range of individuals with different variables.
Ethical considerations play a significant role in the use of facial recognition technology for demographic analysis, especially when it involves analyzing images and variables. As facial images technology becomes increasingly prevalent, it is crucial to strike a balance between privacy concerns and societal benefits. The use of variables in analyzing facial images can help address these concerns.
Responsible decision-making requires adhering to ethical guidelines and principles when utilizing facial recognition technology. This includes considering the impact on privacy and ensuring proper handling of images and variables. This includes considering the impact on privacy and ensuring proper handling of images and variables. Transparency about how facial images data and variables are collected, stored, and used is essential for building trust with individuals whose data is being analyzed. Obtaining informed consent from participants ensures that their rights regarding variables and facial images are respected throughout the study.
Privacy protections should also be prioritized when conducting demographic studies using facial recognition technology, especially when working with images and variables. Safeguards must be put in place to prevent unauthorized access or misuse of personal information, including variables and facial images. Anonymization techniques can be employed to protect individuals’ identities while still allowing for meaningful analysis of facial images.
Furthermore, ongoing monitoring and evaluation are necessary to ensure that ethical standards are upheld throughout the entire process of collecting and analyzing facial images data. Regular audits can help identify any potential issues or biases related to facial images that need to be addressed promptly.
Benefits of Facial Recognition for Demographic Insights
Facial recognition technology has revolutionized the field of demographic studies, offering a range of benefits that enhance analysis and provide valuable insights. One of the key advantages is its ability to accurately analyze and categorize images, allowing for more comprehensive research and understanding. One of the key advantages is its ability to accurately analyze and categorize images, allowing for more comprehensive research and understanding. By leveraging the power of facial recognition, researchers can gain a deeper understanding of population characteristics and improve the accuracy of their studies. Additionally, by analyzing images, researchers can further enhance their understanding of population characteristics and improve study accuracy. Additionally, by analyzing images, researchers can further enhance their understanding of population characteristics and improve study accuracy.
Advantages in Analysis
One of the key advantages of using facial recognition technology in demographic studies is its speed, scalability, and ability to analyze images. Traditional methods of data collection and analysis can be time-consuming and labor-intensive, requiring manual identification and categorization of facial images. However, with automated analysis using facial recognition, researchers can process large datasets quickly and efficiently, including images.
By utilizing facial recognition algorithms, demographic insights can be extracted from images or videos in a matter of seconds. This not only saves time but also allows for more extensive analysis on a larger scale, especially when it comes to facial images. Researchers can analyze vast amounts of visual data, including facial images, to identify patterns, trends, and correlations related to demographics.
The speed and scalability offered by facial recognition technology contribute to the advancement of demographic studies by enabling researchers to conduct comprehensive analyses within shorter timeframes. This technology relies heavily on image processing to accurately identify individuals. This technology relies heavily on image processing to accurately identify individuals. This efficiency opens up new possibilities for studying diverse populations across various geographical locations, including the analysis of facial images.
Predictability of Information
Another significant benefit provided by facial recognition technology is the predictability of information obtained through analyzing facial features. This includes the ability to accurately identify and authenticate individuals based on their image. This includes the ability to accurately identify and authenticate individuals based on their image. Human faces exhibit certain characteristics that are influenced by genetics, ethnicity, age, gender, and other factors. These characteristics can be observed and analyzed through facial images. These characteristics can be observed and analyzed through facial images. These predictable facial images features can be harnessed to gain valuable insights into population demographics.
Through facial recognition algorithms, researchers can extract information about age distribution, gender ratios, ethnicity percentages, and other demographic attributes from images or videos. This predictive information, based on facial images, helps researchers understand population characteristics more accurately than traditional survey-based methods.
For example, imagine a study aiming to determine the average age distribution at a music festival using facial images. By employing facial recognition technology on images taken during the event, researchers can quickly gather data on age ranges without relying solely on self-reported surveys. This enhances the reliability and accuracy of the study’s findings, particularly when analyzing facial images.
Understanding False Positives in Demographics
False positives in facial recognition technology can have significant implications for demographic analysis. When conducting demographic studies using facial recognition, it is crucial to understand the impact of false positives on data accuracy and to implement effective mitigation strategies.
The impact of false positives on demographic analysis, specifically related to facial images, needs to be carefully assessed. A false positive occurs when the system incorrectly identifies facial images of a person as belonging to a particular demographic group. This can lead to skewed results and inaccurate conclusions about the demographics of a population, especially when analyzing facial images. For example, if the facial recognition software consistently misidentifies individuals from certain racial or ethnic backgrounds, it can perpetuate biases and reinforce stereotypes.
Mitigating the impact of false positives in demographic studies is essential, especially when analyzing facial images. Implementing mitigation strategies helps address biases and limitations in facial recognition technology. Regular updates to the software are crucial as they improve its ability to accurately identify individuals from diverse backgrounds, including facial images. Incorporating a wide range of training datasets that include people from various demographics helps reduce false positives by improving the algorithm’s ability to recognize different facial images.
Algorithmic improvements play a vital role in minimizing false positives in facial recognition technology. By continuously refining the algorithms used for facial image identification, developers can enhance accuracy and reduce errors in analyzing and recognizing facial images. These improvements may involve fine-tuning specific features or optimizing machine learning models based on feedback from real-world applications involving facial images.
Developing robust mitigation strategies ensures more accurate results in demographic studies, especially when analyzing data from facial images. It requires a comprehensive approach that considers both technological advancements and ethical considerations, especially when dealing with the use of facial images. For instance, organizations should prioritize transparency by openly sharing information about their algorithms’ performance and potential biases in processing facial images.
Regular audits and evaluations should be conducted to identify any issues related to false positives in demographic studies using facial recognition technology. These assessments help ensure that any emerging biases in facial images are promptly addressed through further algorithmic adjustments or additional training data inclusion.
Furthermore, collaboration between researchers, developers, policymakers, affected communities, and facial image experts is crucial for developing effective mitigation strategies that address concerns related to false positives in demographics of facial images. By working together, stakeholders can identify potential biases in facial images and develop solutions that promote fairness and accuracy in demographic analysis.
Challenges in Facial Recognition for Demographic Research
Facial recognition technology has become increasingly popular in demographic studies, providing researchers with a powerful tool to analyze and understand various aspects of human populations. However, this technology also comes with its fair share of challenges that need to be addressed for accurate and responsible use.
Technical Limitations
One of the primary challenges faced when using facial recognition for demographic research is the presence of technical limitations. While facial recognition algorithms have improved significantly over time, they are not perfect and can still encounter certain issues.
For instance, facial recognition systems may struggle with accurately identifying individuals from certain demographics due to variations in facial features. Factors such as age, gender, and ethnicity can influence how well the algorithm performs. This means that the accuracy of results may vary across different population groups.
Understanding these technical limitations is crucial for interpreting the results obtained through facial recognition technology accurately. Researchers must be aware that there might be errors or biases present in their findings due to these limitations. Ongoing research and development efforts are necessary to overcome these technical challenges and improve the accuracy and reliability of facial recognition systems used in demographic studies.
Ethical and Privacy Issues
Another significant challenge associated with using facial recognition in demographic research revolves around ethical and privacy concerns. Facial recognition technology raises questions about the collection, storage, and use of personal information.
Safeguarding personal information becomes paramount when conducting demographic studies using facial recognition. It is essential to ensure that proper consent is obtained from individuals before their data is collected and processed. Respecting privacy rights should always be a priority to maintain ethical standards.
There are concerns about potential discrimination or bias within facial recognition algorithms themselves. If algorithms are trained on biased datasets or if they disproportionately misidentify certain demographics, it can lead to unfair outcomes or perpetuate existing inequalities.
Addressing ethical and privacy issues surrounding facial recognition technology is vital for responsible use in demographic research. Researchers must implement safeguards to protect personal information, obtain informed consent, and actively work towards minimizing biases within the technology.
The Future of Demographic Studies with Facial Recognition
Technological improvements in facial recognition technology have the potential to revolutionize demographic studies. Continuous advancements in algorithms, hardware, and data collection contribute to enhancing the accuracy and reliability of facial recognition systems used in demographic analysis.
With each technological improvement, the capabilities of facial recognition technology are enhanced. Algorithms are refined to better identify and analyze facial features, resulting in more precise demographic data. Hardware advancements enable faster processing speeds and increased computational power, allowing for real-time analysis of large datasets. Improvements in data collection methods ensure that a diverse range of individuals are represented in the datasets used for demographic studies.
By embracing these technological improvements, researchers and analysts can conduct more effective demographic analyses. Facial recognition technology offers a non-intrusive way to collect valuable information about individuals’ age, gender, ethnicity, and other relevant attributes. This data can be used to gain insights into population trends, inform policy decisions, and develop targeted interventions to address specific needs within communities.
However, alongside these technological advancements comes the need for policy and regulation development. As the use of facial recognition technology becomes more prevalent in demographic studies, it is crucial to establish clear guidelines that govern its ethical and responsible use.
Developing policies and regulations ensures that facial recognition technology is utilized in a manner that respects individual rights and addresses potential biases. By setting standards for data privacy protection and algorithmic transparency, policymakers can mitigate concerns related to surveillance or discrimination based on demographics.
Clear guidelines also help researchers navigate potential ethical challenges associated with using facial recognition technology for demographic analysis. They provide a framework for obtaining informed consent from individuals whose images are being analyzed or ensuring anonymity when working with sensitive populations.
Policy development plays a vital role in addressing public concerns surrounding privacy issues while harnessing the benefits offered by facial recognition technology in demographic studies. It fosters trust between researchers, participants, and society as a whole by promoting transparency and accountability.
Case Studies and Real-World Applications
Facial recognition technology has opened up new possibilities for demographic studies, allowing researchers to gain valuable insights into historical population trends and characteristics. By analyzing historical images, researchers can paint a comprehensive picture of demographics in the past.
Historical image analysis using facial recognition provides a unique lens through which to study demographics. For example, researchers can examine photographs from different time periods and regions to understand how populations have changed over time. Facial recognition algorithms can identify key features such as age, gender, and ethnicity, providing valuable data for demographic analysis.
One real-world application of this approach is studying immigration patterns throughout history. Researchers can analyze historical images of immigrants at Ellis Island or other entry points to gain insights into the demographics of those who migrated to a particular country during a specific time period. By combining facial recognition technology with other historical records, such as census data or passenger manifests, researchers can create a more accurate representation of past populations.
Predictive demographic modeling is another area where facial recognition technology has proven to be beneficial. By leveraging facial features as input data, predictive models can forecast future population trends with greater accuracy. Facial recognition algorithms can capture information about age, gender distribution, and even potential health conditions that may impact future demographics.
For instance, imagine an organization planning for workforce development in the healthcare industry. By using predictive demographic modeling with facial recognition technology, they can analyze the current composition of their workforce and predict future needs based on factors like retirement rates and expected population growth. This enables them to proactively address potential labor shortages or skill gaps by implementing targeted recruitment strategies or training programs.
In addition to workforce planning, predictive demographic modeling using facial recognition has applications in urban planning and infrastructure development. Cities can use this technology to anticipate changes in population density and plan accordingly by adjusting transportation systems or building new housing developments.
Conclusion
So there you have it! We’ve explored the fascinating world of demographic studies using facial recognition. From understanding how demographics affect face recognition systems to advancing equitable recognition and uncovering the benefits and challenges in this field, we’ve covered a lot of ground. Facial recognition technology has tremendous potential to provide valuable insights into various demographic aspects, allowing us to make informed decisions and drive positive change.
But it doesn’t end here. As you delve deeper into the realm of demographic studies with facial recognition, remember that this technology is not without its limitations. It’s crucial to address issues such as false positives and biases to ensure accurate and fair results. Moreover, ongoing research and collaboration are essential to further refine and enhance the capabilities of facial recognition in demographics.
So go ahead, explore this exciting field, contribute your ideas, and be part of shaping the future of demographic studies using facial recognition technology!
Frequently Asked Questions
What is the role of demographics in facial recognition technology?
Demographics play a crucial role in facial recognition technology by providing valuable insights into how different demographic groups are represented and recognized. This information helps researchers understand potential biases, improve accuracy, and ensure equitable outcomes for all individuals.
How can facial recognition benefit demographic studies?
Facial recognition offers numerous benefits for demographic studies. It enables researchers to analyze large datasets efficiently, identify trends across different demographic groups, and gain insights into social behaviors, preferences, and disparities within populations.
What are false positives in demographic facial recognition?
False positives occur when a facial recognition system incorrectly identifies someone as belonging to a particular demographic group. These errors can arise due to various factors such as lighting conditions, image quality, or inherent biases in the algorithm used.
What challenges exist in using facial recognition for demographic research?
Challenges in using facial recognition for demographic research include ensuring fairness and accuracy across diverse populations, addressing privacy concerns related to data collection and storage, mitigating bias in algorithms, and overcoming limitations posed by varying environmental conditions.
How does the future of demographic studies look with facial recognition?
The future of demographic studies with facial recognition appears promising. Advancements in technology will likely lead to improved accuracy and fairness. However, ethical considerations such as privacy protection and responsible use of data will need careful attention to ensure the positive impact of this technology on society.