What is the significance of liveness detection in face anti-spoofing solutions?
How do technological advancements contribute to improving anti-spoofing solutions?
Can you explain how different types of attacks can be prevented using face anti-spoofing solutions?
How does comparing recognition technologies help in selecting an effective anti-spoofing solution?
What metrics are used to measure the effectiveness of face anti-spoofing solutions?
Ever wondered how biometric security, especially facial recognition, ensures the protection of your identity and detects image spoofing? With its ability to analyze the unique features of the human face, facial recognition technology can effectively identify and prevent spoofing techniques that manipulate images or voices. With the increasing sophistication of spoofing threats, it’s crucial to address challenges related to voice, image, and 3D face recognition in order to effectively target these threats. Biometric security offers a robust defense by leveraging unique physical or behavioral traits for authentication, including 3d face recognition and 2d face recognition. These technologies analyze the distinct features of the human face to ensure accurate identification and prevent spoofing techniques. However, as attackers manipulate data to deceive systems, anti-spoofing measures have become imperative in safeguarding against unauthorized access. This is especially important when dealing with client information and protecting the integrity of the target system. By implementing effective anti-spoofing techniques, organizations can ensure that their voice and image are protected from malicious actors.
Spoofing threats pose significant risks to the integrity of biometric authentication, including 3D face recognition, 2D face recognition, image, and voice. By understanding the relevance and impact of anti-spoofing technologies in enhancing the reliability and effectiveness of 2d face recognition for biometric security, we can address concerns related to image spoofing and ensure accurate identification of human faces as the target. As technology evolves, so do potential vulnerabilities; thus, exploring advanced anti-spoofing solutions for face recognition is essential for ensuring a secure user experience.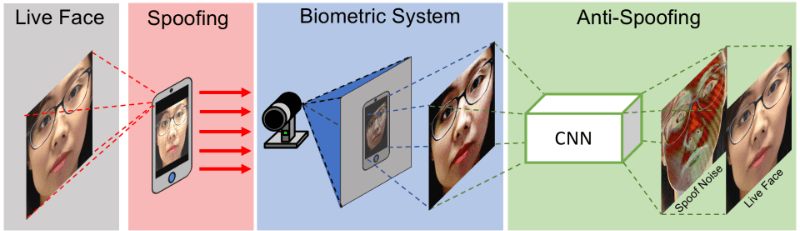
Overview of Anti-Spoofing
Defining Anti-Spoofing
Face anti-spoofing solutions are techniques used to detect and prevent spoofing attacks, ensuring the accuracy and reliability of biometric systems. These solutions work by identifying fake or manipulated biometric data, such as face recognition and image spoofing, during authentication processes. They are designed to detect any attempts of facial spoofing or manipulation of human face images. For instance, when a person tries to use a photograph or video of an authorized individual to gain unauthorized access, face anti-spoofing solutions can detect this fraudulent attempt.
In essence, anti-spoofing serves as a crucial safeguard against malicious activities aimed at undermining the integrity of facial recognition and other biometric security measures. By implementing these solutions, organizations can significantly reduce the risk of unauthorized access through the use of counterfeit identities, as well as protect against facial spoofing and enhance face recognition.
Importance of Liveness Detection
Liveness detection is an integral component within face anti-spoofing solutions as it enables systems to distinguish between live subjects and spoofed attempts effectively. This capability is essential in preventing attackers from using static images or pre-recorded videos to trick facial recognition systems into granting unauthorized access.
By incorporating face recognition and liveness detection into their security protocols, businesses and institutions can add an extra layer of protection against fraudulent activities involving impersonation or identity theft. For example, financial institutions deploying face anti-spoofing technology can ensure that only authentic individuals have access to sensitive accounts or transactions.
Active vs Passive Detection
Two primary methods for face recognition are commonly employed: active face detection and passive face detection.
Active face recognition detection requires user participation in proving liveness by performing specific actions like blinking or smiling during the authentication process.
On the other hand, passive detection analyzes facial features using face recognition technology without requiring any direct interaction from users.
Both active and passive methods have their respective advantages and limitations. While active detection ensures higher confidence in liveness determination due to user involvement, passive detection offers seamless user experience without necessitating explicit actions from individuals undergoing authentication processes.
Liveness Detection Techniques
Eye Blink Detection
Eye blink detection is a crucial liveness detection technique in facial recognition systems. It ensures that the subject is alive and not presenting a static image or video playback to deceive the authentication process. By analyzing eye movement patterns, eye blink detection algorithms can effectively determine liveness. For instance, when a person blinks, their eyes move in specific ways that distinguish them from still images or prerecorded videos.
This method plays a pivotal role in preventing unauthorized access attempts by ensuring that only live individuals are granted access. Moreover, it adds an extra layer of security to biometric systems by verifying the presence of real-time human interaction during authentication.
Challenge-Response Methods
Challenge-response methods are another essential approach for facial liveness verification. This technique involves presenting random challenges to users during the authentication process and analyzing their responses to verify liveness and prevent spoofing attempts effectively. For example, users may be prompted with unexpected tasks such as smiling or nodding during the verification process.
By incorporating these spontaneous challenges into the authentication procedure, challenge-response methods significantly enhance security measures against fraudulent activities like using printed photos or masks for impersonation purposes.
Active Flash Applications
Active flash applications represent an innovative approach to detect spoofing attempts through controlled lighting conditions. These applications utilize distinct reflection patterns on a subject’s face under controlled light exposure to ascertain their facial liveness accurately. By capturing and analyzing these reflection patterns, active flash applications can effectively differentiate between genuine human faces and artificial representations used for fraudulent purposes.
For instance, when exposed to controlled flashes of light, authentic facial features exhibit unique reflective properties compared to static images or masks commonly employed in spoofing attacks.
Technological Advancements in Anti-Spoofing
3D Camera Integration
3D camera integration is a crucial technological advancement in face anti-spoofing solutions. By capturing depth information, it makes it challenging for attackers to spoof using 2D images. This technology enhances the accuracy of facial recognition systems and provides better defense against advanced spoofing techniques. For instance, when a person tries to use a photograph or video of someone else’s face to bypass security measures, the 3D camera integration can detect the lack of depth and prevent unauthorized access.
The incorporation of 3D camera integration into anti-spoofing solutions has significantly bolstered their effectiveness. It adds an extra layer of security by making it harder for malicious actors to deceive facial recognition systems with counterfeit visuals. The ability to capture three-dimensional data enables these systems to discern between real human faces and fake representations more accurately.
Convolutional Neural Networks
Another pivotal element in face anti-spoofing solutions is the utilization of convolutional neural networks (CNNs). These networks are adept at analyzing intricate facial features and patterns, enabling them to differentiate between genuine and fake faces effectively. By leveraging CNN-based anti-spoofing algorithms, organizations can fortify their biometric security measures against fraudulent attempts.
The deployment of CNNs has demonstrated promising results in thwarting various spoofing attacks aimed at breaching facial recognition systems’ liveness detection mechanisms. Through its sophisticated analysis capabilities, this technology plays a vital role in identifying discrepancies that indicate potential spoofing activities within visual data.
Deep Learning Applications
In recent years, deep learning techniques have revolutionized the landscape of anti-spoofing measures employed in biometric security protocols. These applications enable models to learn complex patterns and features associated with liveness detection more comprehensively than traditional methods allow for. Deep learning’s capacity for nuanced pattern recognition empowers anti-spoofing solutions by enhancing their ability to accurately distinguish between authentic human faces and fraudulent representations.
Implementing Anti-Spoofing Solutions
Hardware Approaches
Hardware approaches for face anti-spoofing solutions involve the use of specialized sensors or devices to enhance security measures. These methods employ technologies such as infrared cameras, depth sensors, and multi-modal biometric systems. For instance, infrared cameras can detect temperature variations on a person’s face to distinguish between real faces and printed photos or masks.
These hardware approaches offer robust protection against various spoofing techniques by adding an extra layer of security through physical verification. By incorporating these advanced sensors into existing security systems, organizations can significantly reduce the risk of unauthorized access and fraudulent activities.
Examples:
Infrared cameras can capture unique heat patterns emitted by live human skin.
Depth sensors utilize 3D mapping to verify the spatial dimensions of a user’s face.
Software Strategies
Software strategies play a crucial role in developing algorithms and software-based solutions for anti-spoofing. Leveraging machine learning and computer vision techniques enables these strategies to accurately detect fake biometric data with high precision. With continuous advancements in technology, software-based anti-spoofing solutions are becoming increasingly sophisticated in identifying even the most intricate spoofing attempts.
These software strategies offer flexibility and scalability when implementing anti-spoofing measures across different platforms and devices. Moreover, they enable organizations to adapt quickly to emerging threats by updating their algorithms based on evolving attack patterns.
Examples:
Machine learning algorithms analyze facial features for irregularities associated with spoofed images.
Computer vision techniques identify discrepancies between real-time facial movements and static images used for spoof attacks.
Multi-factor Authentication
Multi-factor authentication (MFA) combines multiple authentication methods to strengthen overall security measures. By integrating facial recognition as one of the factors within MFA frameworks, organizations can enhance identity verification processes while mitigating potential risks associated with single-factor authentication methods. This approach ensures that individuals seeking access undergo more comprehensive scrutiny before being granted entry.
The integration of facial recognition with other authentication factors such as passwords or fingerprint scans provides an additional layer of defense against unauthorized access attempts. As a result, it significantly reduces the likelihood of successful spoof attacks targeting individual components within the multi-factor framework.
Preventing Different Types of Attacks
Presentation Attack Detection
Presentation attack detection is vital for ensuring the reliability of biometric systems. It involves analyzing various characteristics, such as texture, motion, or thermal features to identify and prevent spoofing attempts during presentation attacks. For instance, when a person tries to fool a facial recognition system by presenting a photo or video instead of their actual face, presentation attack detection can recognize this fraudulent attempt.
Robust presentation attack detection helps in preventing replay attacks where an attacker uses recorded biometric data to gain unauthorized access. By analyzing different aspects like texture and motion, the system can distinguish between live facial movements and pre-recorded videos or images.
Injection Attack Safeguards
Injection attacks involve injecting fake biometric data into the system with the intention of bypassing authentication measures. To safeguard against injection attacks in face anti-spoofing solutions, implementing robust techniques such as data validation and anomaly detection is crucial.
For example, if someone tries to inject fake facial features into the system’s database in order to impersonate another individual for unauthorized access, effective injection attack safeguards can detect these anomalies and prevent fraudulent activities from occurring.
Email Authentication Protocols
Email authentication protocols play a pivotal role in preventing email spoofing and phishing attacks. Protocols like DMARC (Domain-based Message Authentication Reporting & Conformance), SPF (Sender Policy Framework), and DKIM (DomainKeys Identified Mail) help verify the authenticity of emails by checking sender information against established records.
Enhancing Security Measures
Avoiding Public Networks
One crucial measure is avoiding public networks. Using secure and private networks ensures the confidentiality of biometric data. Public networks are more vulnerable to spoofing attacks due to their open nature. For example, when individuals use unsecured Wi-Fi in public places like cafes or airports, their biometric data might be intercepted by unauthorized parties.
Furthermore, avoiding public networks reduces the risk of data interception and spoofing attempts. By using a secure network, individuals can minimize the chances of unauthorized access to their biometric information.
Comprehensive Spoofing Defense
Another essential aspect of face anti-spoofing solutions is comprehensive spoofing defense. This involves combining multiple anti-spoofing techniques such as hardware-based, software-based, and behavioral approaches for enhanced security measures. For instance, hardware-based methods may include liveness detection through 3D depth sensing cameras that can distinguish between a real person’s face and a printed photo or mask.
By integrating various anti-spoofing techniques into a comprehensive defense strategy, organizations can ensure robust protection against various types of spoofing threats. These combined approaches provide an additional layer of security that makes it harder for malicious actors to bypass authentication systems.
Collaboration for Advanced Security
Collaboration between researchers, industry experts, and policymakers plays a pivotal role in advancing face anti-spoofing solutions for enhanced security measures against potential attacks. Sharing knowledge and expertise among different stakeholders helps develop more effective countermeasures against evolving spoofing attacks.
Moreover, collaborative efforts lead to continuous improvements in biometric security systems by leveraging diverse perspectives from professionals across various domains. By working together towards common goals—such as enhancing facial recognition technology—experts can address emerging challenges related to identity verification and fraud prevention more effectively.
Comparing Recognition Technologies
3D vs 2D Recognition
The choice between 3D and 2D recognition is crucial. 3D recognition offers superior defense against spoofing compared to its 2D counterpart. By capturing depth information, 3D recognition makes it incredibly challenging for attackers to spoof biometric systems using flat images. Integrating 3D recognition into biometric systems significantly enhances their overall security and accuracy. For instance, a facial recognition system that utilizes 3D technology can accurately distinguish between a live person and a printed photo.
Leveraging the capabilities of 3D face recognition technology, organizations can ensure robust protection against unauthorized access attempts through impersonation or identity theft. Moreover, by incorporating this advanced form of biometric authentication, businesses can bolster their security measures while providing users with seamless and efficient experiences.
Role of Liveness in Biometrics
In the realm of biometrics, liveness detection plays an indispensable role in upholding the authenticity of biometric data. This critical feature prevents attackers from exploiting fake or stolen biometric information for unauthorized access attempts within various systems or facilities. By verifying that the captured data corresponds to a living individual rather than a static image or video recording, liveness detection ensures the integrity and reliability of biometric systems.
Integrating liveness detection into face anti-spoofing solutions is essential for safeguarding sensitive information and securing access control mechanisms across diverse applications such as mobile devices, financial transactions, physical access points, and more. Through rigorous verification processes enabled by liveness detection technologies within facial recognition systems, organizations can fortify their defenses against fraudulent activities while maintaining user trust and confidence in their services.
Measuring Anti-Spoofing Effectiveness
Success Metrics
Face anti-spoofing solutions are evaluated based on success metrics such as the false acceptance rate (FAR) and false rejection rate (FRR). A lower FAR indicates fewer instances of accepting spoofed attempts as genuine, ensuring that only legitimate users are granted access. On the other hand, a lower FRR implies fewer instances of rejecting genuine attempts as spoofed, preventing inconvenience for authorized individuals. These metrics play a crucial role in determining the effectiveness of anti-spoofing technologies.
For instance, if an organization’s face recognition system exhibits a high FAR, it means that there is a significant risk of unauthorized access due to accepting fraudulent attempts. Conversely, a high FRR can lead to frustration among authentic users who are repeatedly denied access. Therefore, by analyzing these success metrics, organizations can identify areas for improvement in their anti-spoofing solutions.
Fraud Prevention Models
Fraud prevention models leverage machine learning algorithms to detect and prevent spoofing attacks effectively. By analyzing patterns, anomalies, and behavioral characteristics associated with facial recognition attempts, these models can identify potential fraudsters attempting to deceive the system using spoofed biometric data. This proactive approach enables organizations across various industries to mitigate the risks associated with face anti-spoofing.
In practical terms, consider a financial institution employing face anti-spoofing technology within its mobile banking application. Through sophisticated fraud prevention models powered by machine learning algorithms, this institution can swiftly differentiate between legitimate user interactions and fraudulent attempts aimed at gaining unauthorized access or conducting illicit transactions. As a result, customers benefit from enhanced security measures while enjoying seamless digital banking experiences.
Conclusion
You’ve now explored the dynamic landscape of face anti-spoofing solutions, delving into liveness detection techniques, technological advancements, implementation strategies, security measures, and effectiveness measurements. As technology continues to evolve, the battle against spoofing attacks intensifies, making it crucial to stay updated with the latest anti-spoofing tools and strategies. Remember, the effectiveness of any anti-spoofing solution relies not just on its technology but also on its seamless integration into your existing security infrastructure. Stay vigilant and proactive in enhancing your security measures to outsmart potential spoofing threats.
In a world where digital security is paramount, staying ahead in the game of anti-spoofing is a continuous journey. Keep exploring new advancements, testing different solutions, and adapting to emerging threats. Your commitment to robust anti-spoofing measures will not only safeguard your systems and data but also contribute to the collective resilience against cyber threats. Stay informed, stay secure.
Frequently Asked Questions
What is the significance of liveness detection in face anti-spoofing solutions using facial recognition software and computer vision? Liveness detection plays a crucial role in ensuring the accuracy and security of biometric verification in a biometric system.
Liveness detection plays a crucial role in face anti-spoofing as it verifies that the biometric traits being captured are from a live person and not from a static image or video. It ensures the authenticity of the facial recognition process, enhancing security.
How do technological advancements contribute to improving anti-spoofing solutions with face recognition systems and facial recognition software? These advancements ensure accurate results and enhance security by incorporating 3d face recognition.
Technological advancements, such as multi-modal biometrics and deep learning algorithms, enhance anti-spoofing solutions by increasing accuracy and robustness. These advancements enable systems to detect sophisticated spoof attacks effectively, providing better protection against unauthorized access.
Can you explain how different types of attacks can be prevented using facial recognition software and face anti-spoofing solutions? This presentation will provide an overview of the computer vision techniques used in these solutions.
Face anti-spoofing solutions prevent various types of attacks including print attack, replay attack, and 3D mask attack by utilizing techniques like texture analysis, motion detection, depth estimation, and behavior analysis. This ensures comprehensive protection against fraudulent attempts.
How does comparing recognition technologies help in selecting an effective anti-spoofing solution? When selecting an effective anti-spoofing solution, it is crucial to compare different recognition technologies to ensure the highest level of security. By evaluating various technologies such as image recognition and network analysis, you can identify the most suitable solution to detect and prevent presentation attacks. This process allows you to target and mitigate potential vulnerabilities, safeguarding your system against unauthorized access.
Comparing recognition technologies allows for evaluating their performance based on factors like accuracy, speed, and resilience to spoof attacks. This comparison aids in choosing an effective solution tailored to specific security needs while considering practical deployment scenarios.
What metrics are used to measure the effectiveness of facial recognition software in detecting and preventing presentation attacks?
The effectiveness of face anti-spoofing solutions is measured using metrics such as false acceptance rate (FAR), false rejection rate (FRR), equal error rate (EER), and area under curve (AUC). These metrics provide insights into the system’s ability to distinguish between genuine users and impostors accurately.
