For years, 3D face spoofing was seen as the biggest threat to facial recognition systems. Security teams worried about masks, molded faces, and printed replicas tricking biometric scanners. At the time, those concerns were valid because early systems relied on limited visual checks.
Today, the risk landscape looks very different. Facial recognition technology has matured, and attackers have shifted their focus. The most serious threats are no longer physical masks but digital manipulation, enrollment fraud, and system-level weaknesses that target identity workflows rather than cameras.
This shift is exactly why modern biometric security needs a new way of thinking. Recognito helps organizations move beyond outdated threat models by providing advanced facial recognition and anti spoofing technology built for today’s real risks.
In this blog, we explain what 3D face spoofing is, why it is no longer the primary concern, and what security teams should focus on instead when evaluating facial recognition systems.
What Is 3D Face Spoofing
3D face spoofing refers to attempts to trick facial recognition systems using physical replicas of a person’s face. These attacks aim to mimic depth and structure, making them more convincing than flat photos.
3D Masks
Wearable masks made from silicone or latex that attempt to replicate a real person’s facial features. Early biometric systems struggled to detect them due to limited depth analysis.
3D Printed Faces
Rigid facial models created using 3D printers based on stolen or scraped images. These replicas often fail to replicate natural movement and skin behavior.
Silicone Models
High-quality silicone faces designed to simulate realistic texture and contours. While visually convincing, they lack natural biological responses.
3D spoofing gained attention in early biometric systems because those systems focused mainly on facial shape rather than behavior, motion, or biological signals.
Why 3D Spoofing Is Less Effective Today
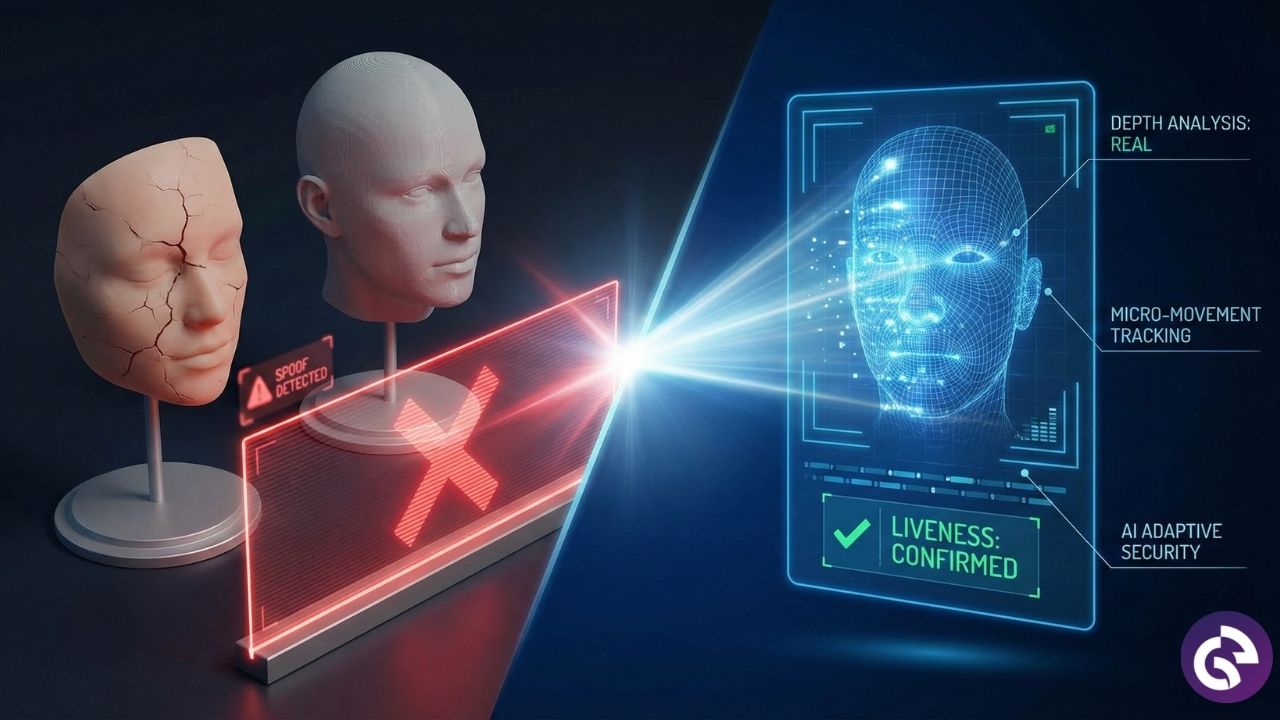
3D spoofing is becoming increasingly difficult as facial recognition technology evolves. Here are some modern techniques that advanced systems use to prevent 3D spoofing.
Advances in Anti Spoofing Technology
Modern anti-spoofing systems now confirm real human presence by analyzing subtle cues like micro-movements, depth variations, and natural facial responses. Liveness detection ensures that only genuine faces are recognized, blocking most mask- or model-based attacks.
Advanced models also perform depth and texture analysis to detect inconsistencies in light reflection, material composition, and skin texture that spoofing attempts cannot replicate. Additionally, motion and behavioral cues, such as facial dynamics, head movement, and response timing, reveal unnatural patterns, further strengthening system security.
Smarter AI Security Models
Facial recognition today relies on adaptive AI rather than static rules. Models are trained on real spoofing attempts and continuously update as new techniques emerge, reducing false acceptance rates and improving detection accuracy over time. Independent testing, like NIST FRVT evaluations, ensures these AI-driven systems remain reliable and robust.
The Real Security Risks Facing Facial Recognition Today
The biggest threats to facial recognition no longer come from physical spoofing. Today, risks arise from digital manipulation and system-level vulnerabilities that can bypass traditional safeguards.
Presentation Attacks Beyond 3D Masks
Attackers are using increasingly sophisticated methods to fool systems. High-resolution video injection attempts to feed manipulated video streams into verification systems, while synthetic media and replay attacks reuse captured biometric data to bypass weak implementations.
Identity Injection and Enrollment Fraud
Many attacks now target the onboarding stage. Fraudulent identities can be injected during enrollment, and weak verification workflows allow fake profiles to become trusted system identities.
Infrastructure and Integration Weaknesses
Even the most accurate algorithms fail if systems are poorly designed. Exposed APIs, misconfigured deployments, and improper handling of biometric data create vulnerabilities that attackers can exploit.
How Modern Facial Recognition Addresses Today’s Risks
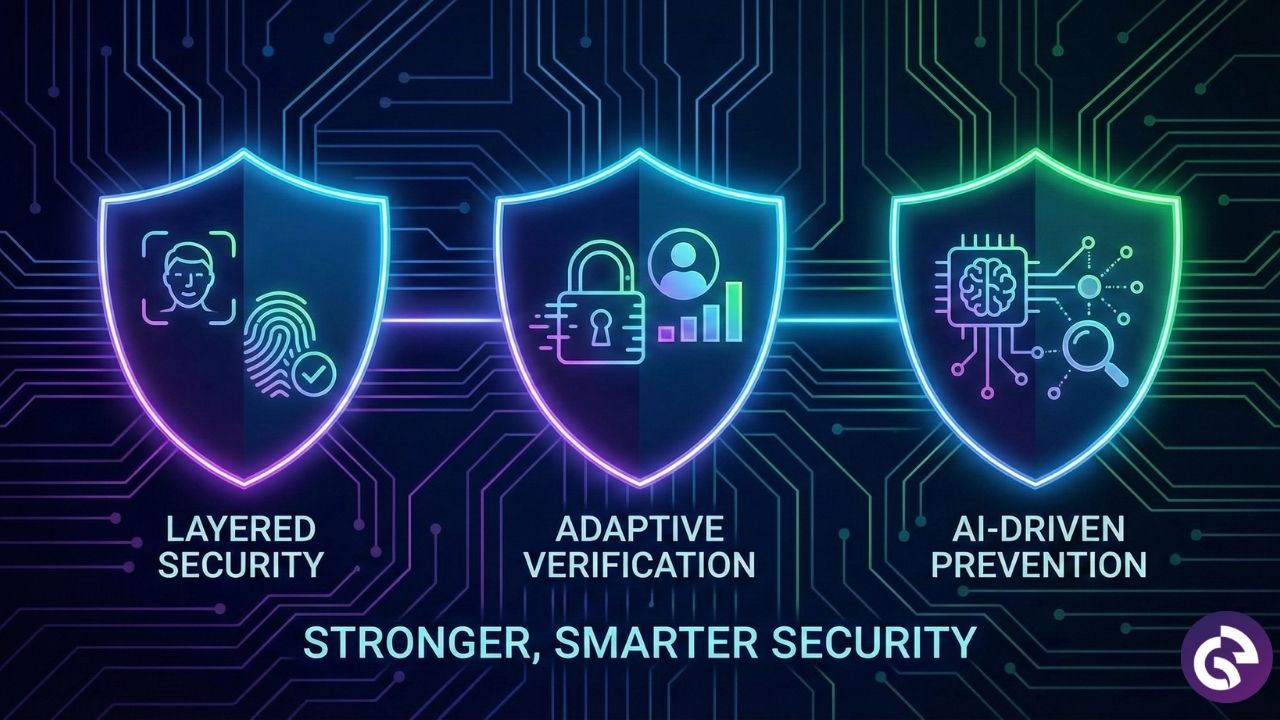
Modern facial recognition systems tackle today’s threats by combining advanced biometric checks, adaptive verification, and AI-driven fraud prevention to ensure stronger and smarter security.
Layered Biometric Security
- Liveness detection combined with face scanning confirms both presence and identity.
- Contextual risk signals, like device behavior and session patterns, add an extra layer of protection.
Adaptive Identity Verification
- Risk-based authentication adjusts security levels based on user behavior.
- Ongoing verification monitors activity throughout the session to detect misuse.
AI-Driven Fraud Prevention
- Pattern detection identifies suspicious behavior across sessions.
- Cross-session analysis helps stop long-term fraud strategies.
Key Considerations When Evaluating Facial Recognition Security
Choosing the right system goes beyond feature comparison. You need to consider anti-spoofing, system design, and privacy safeguards.
Anti Spoofing Depth
Check if the system uses multiple liveness detection methods, like depth sensing, micro-movements, or behavioral cues, to prevent spoofing.
System Architecture
Understand how on-device versus server-side processing works and how data flows, ensuring security and efficiency.
Privacy and Compliance
Systems must respect consent and regulations like GDPR. ENISA guidance also highlights layered identity security for stronger protection.
Facial Recognition Security by Recognito

Recognito delivers facial recognition solutions designed for modern threat environments. Our technology focuses on liveness detection, adaptive verification, and real fraud prevention rather than surface-level matching.
You can explore technical resources and implementation examples through our GitHub repository or contact us to discuss secure deployment tailored to their needs.
Conclusion
The facial recognition threat landscape has evolved. While 3D face spoofing once dominated concerns, it is no longer the primary risk. Today’s threats target enrollment processes, digital workflows, and system integration.
A modern biometric security approach requires layered defenses, adaptive AI, and informed risk assessment. By focusing on real threats rather than outdated fears, organizations can deploy facial recognition with confidence.
Frequently Asked Questions
Is 3D face spoofing still a threat
It exists, but modern liveness detection can reliably spot spoof attempts using depth, motion, and facial cues.
What is the biggest risk in facial recognition today
Enrollment fraud and system-level vulnerabilities pose greater risk than physical spoofing.
How does anti spoofing prevent fraud
It confirms real human presence using depth, motion, and behavioral signals.
Is facial recognition secure for identity verification
Yes, when supported by strong architecture and compliance controls.
What industries face the highest facial recognition risk
Finance, travel, education, and digital platforms handling remote identity verification.

